Internet Security Threat Report Volume 17
Symantec Report
Introduction
More information
- Symantec.cloud Global Threats: http://www.symanteccloud.com/en/gb/globalthreats/
- Symantec Security Response: http://www.symantec.com/security_response/
- Internet Security Threat Report Resource Page: http://www.symantec.com/threatreport/
- Norton Threat Explorer: http://us.norton.com/security_response/threatexplorer/
- Norton Cybercrime Index: http://us.norton.com/cybercrimeindex/
About Symantec
Symantec is a global leader in providing security, storage, and systems management solutions to help consumers and organizations secure and manage their information-driven world. Our software and services protect against more risks at more points, more completely and efficiently, enabling confidence wherever information is used or stored. Headquartered in Mountain View, Calif., Symantec has operations in 40 countries. More information is available at www.symantec.com. .topic { font-size:11px; padding-top:2px; padding-left:10px; color:#FFF; }2011 In Review
2011 In Numbers

Executive Summary
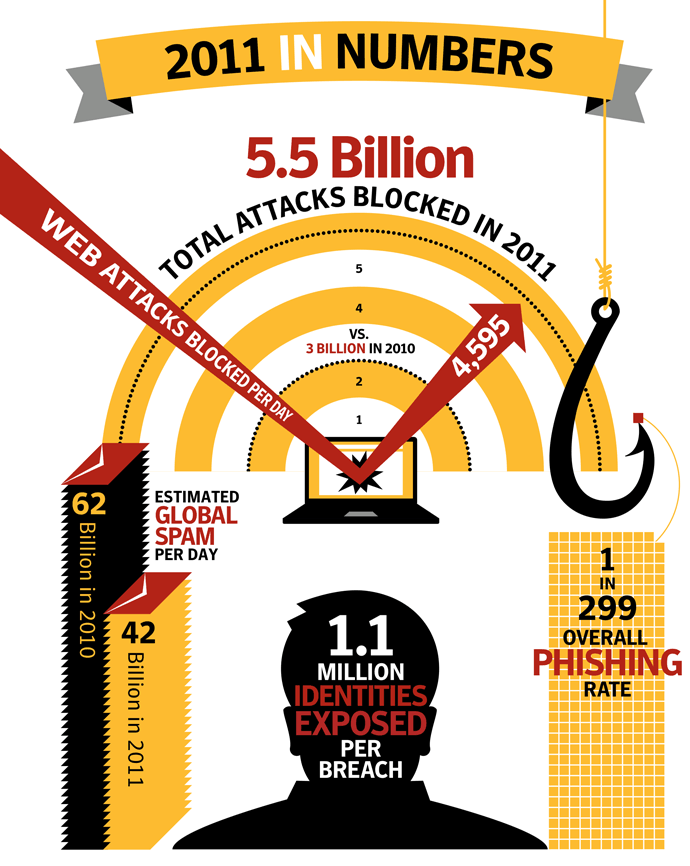
Malicious attacks skyrocket by 81 percent
In addition to the 81% surge in attacks, the number of unique malware variants also increased by 41% and the number of Web attacks blocked per day also increased dramatically, by 36%. Greater numbers of more widespread attacks employed advanced techniques, such as server-side polymorphism to colossal effect. This technique enables attackers to generate an almost unique version of their malware for each potential victim.
Cyber espionage and business: Targeted attacks target everyone
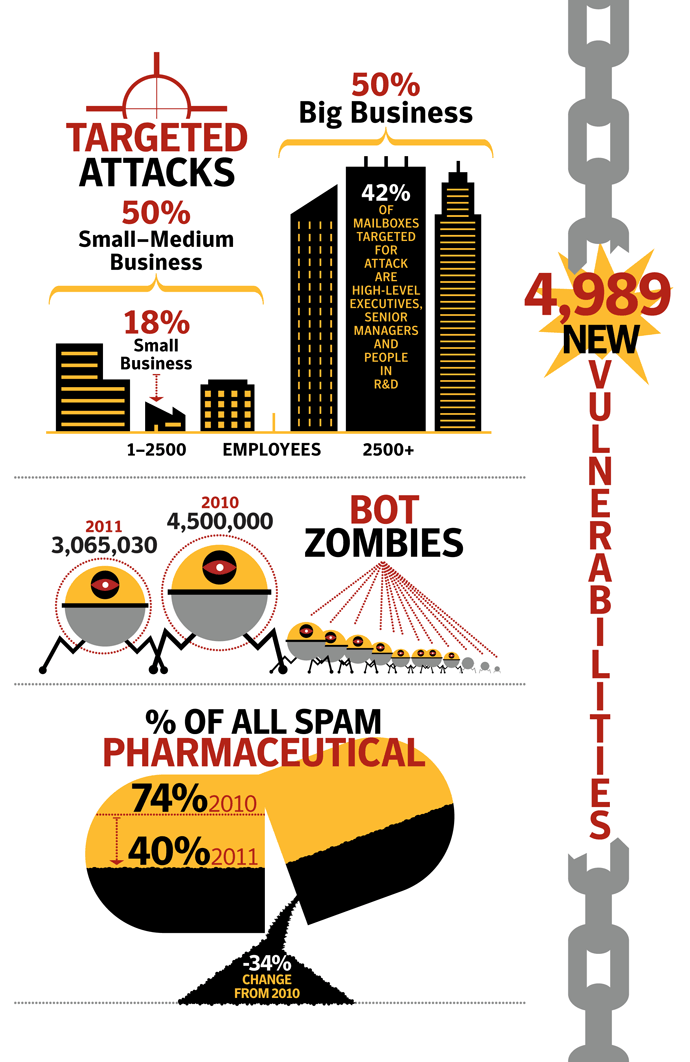
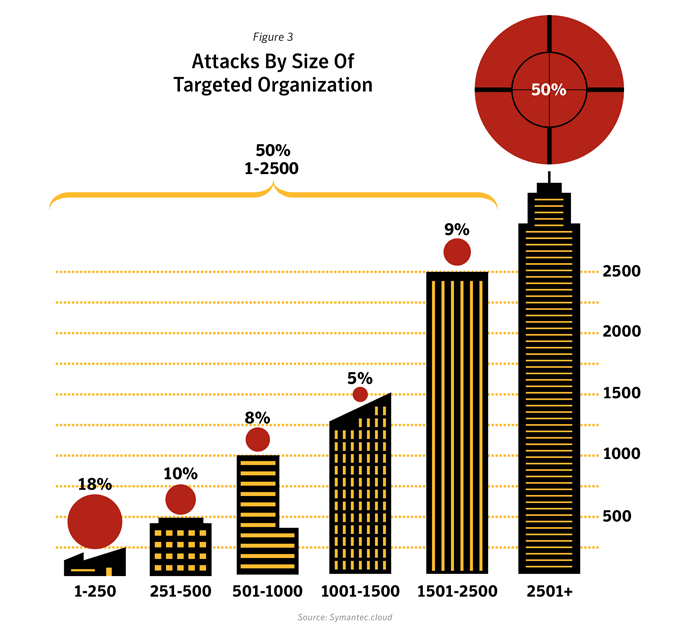
We saw a rising tide of advanced targeted attacks in 2011 (94 per day on average at the end of November 2011). The report data also showed that targeted threats are not limited to the Enterprises and executive level personnel. 50% of attacks focused on companies with less than 2500 employees, and 18% of attacks were focused on organizations with less than 250 employees. It’s possible that smaller companies are now being targeted as a stepping stone to a larger organization because they may be in the partner ecosystem and less well-defended. Targeted attacks are a risk for businesses of all sizes – no one is immune to these attacks.Mobile Phones under Attack
Growth of mobile malware requires a large installed base to attack and a profit motive to drive it. According to the analyst firm, Gartner, smartphones and tablets began to outsell conventional PCs in 2011, with sales of smartphones predicted to reach 645 million by the end of 2012. And while profits remain lucrative in the PC space, mobile offers new opportunities to cybercriminals that potentially are more profitable. A stolen credit card made go for as little as USD 40-80 cents. Malware that sends premium SMS text messages can pay the author USD $9.99 for each text and for victims not watching their phone bill could pay off the cybercriminal countless times. With the number of vulnerabilities in the mobile space rising (a 93.3% increase over 2010) and malware authors not only reinventing existing malware for mobile devices but creating mobile specific malware geared to the unique the opportunities mobile present, 2011 was the first year that mobile malware presented a tangible threat to enterprises and consumers.Certificate Authorities and Transport Layer Security (TLS) v1.0 are targeted as SSL use increases
High-profile hacks of Certificate Authorities, providers of Secure Sockets layer (SSL) Certificates, threatened the systems that underpin trust in the internet itself. However, SSL technology wasn’t the weak link in the DigiNotar breach and other similar hacks; instead, these attacks highlighted the need for organizations in the Certificate Authority supply chain to harden their infrastructures and adopt stronger security procedures and policies. A malware dependent exploit concept against TLS 1.0 highlighted the need for the SSL ecosystem to upgrade to newer versions of TLS, such as TLS 1.2 or higher. Website owners recognized the need to adopt SSL more broadly to combat Man-In-The-Middle (MITM) attacks, notably for securing non-transactional pages, as exemplified by Facebook, Google, Microsoft, and Twitter adoption of Always On SSLii.232 million identities stolen
More than 232.4 million identities were exposed overall during 2011. Although not the most frequent cause of data breaches, breaches caused by hacking attacks had the greatest impact and exposed more than 187.2 million identities, the greatest number for any type of breach in 2011, according to analysis from the Norton Cybercrime Indexiii. The most frequent cause of data breaches (across all sectors) was theft or loss of a computer or other medium on which data is stored or transmitted, such as a USB key or a back-up medium. Theft or loss accounted for 34.3% of breaches that could lead to identities exposed.Botnet takedowns reduce spam volumes
It isn’t all bad news; the overall volume of spam fell considerably in the year from 88.5% of all email in 2010 to 75.1% in 2011. This was largely thanks to law enforcement action which shut down Rustock, a massive, worldwide botnet that was responsible for sending out large amounts of spam. In 2010, Rustock was the largest spam-sending botnet in the world, and with its demise, rival botnets were seemingly unable or unwilling to take its place. At the same time, spammers are increasing their focus on social networking, URL shorteners and other technology to make spam-blocking harder.Safeguarding Secrets: Industrial Espionage in Cyberspace
Safeguarding Secrets: Industrial Espionage in Cyberspace
Cyber-espionage in 2011
The number of targeted attacks increased dramatically during 2011 from an average of 77 per day in 2010 to 82 per day in 2011. And advanced persistent threats (APTs) attracted more public attention as the result of some well publicized incidents.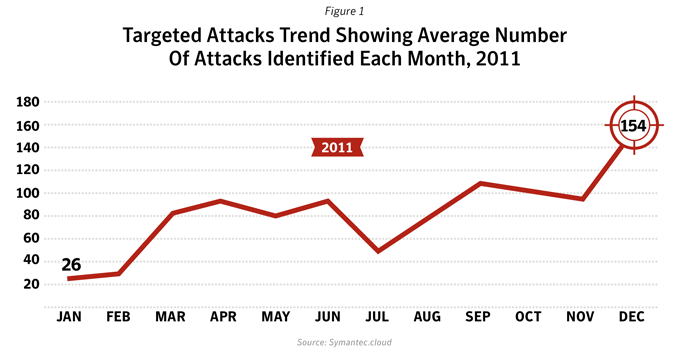
Advanced Persistent Threats
Advanced persistent threats (APTs) have become a buzzword used and misused by the media but they do represent a real danger. For example, a reported attack in March 2011 resulted in the theft of 24,000 files from a US defense contractor. The files related to a weapons system under development for the US Department of Defense (DOD).- They use highly customized tools and intrusion techniques.
- They use stealthy, patient, persistent methods to reduce the risk of detection.
- They aim to gather high-value, national objectives such as military, political or economic intelligence.
- They are well-funded and well-staffed, perhaps operating with the support of military or state intelligence organizations.
- They are more likely to target organizations of strategic importance, such as government agencies, defense contractors, high profile manufacturers, critical infrastructure operators and their partner ecosystem.
Targeted Attacks
Targeted attacks affect all sectors of the economy. However, two-thirds of attack campaigns focus on a single or a very limited number of organizations in a given sector and more than half focus on the defense and aerospace sector, sometimes attacking the same company in different countries at the same time. On average they used two different exploits in each campaign, sometimes using zero-day exploits to make them especially potent.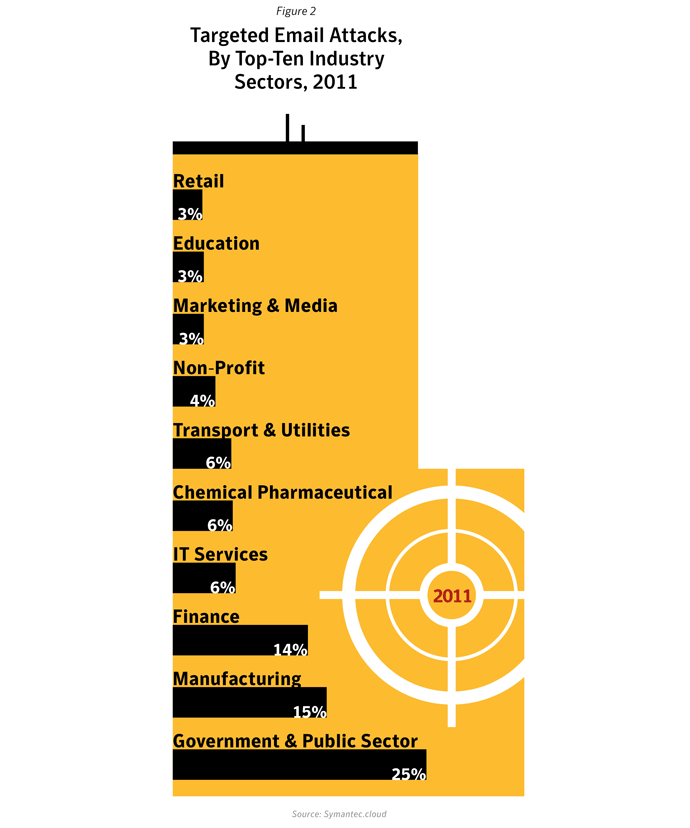
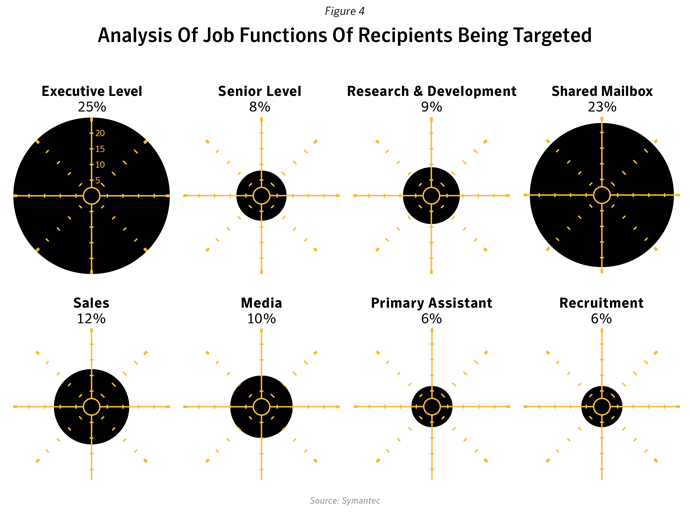
Where attacks come from
Figure 5 represents the geographical distribution of attacking machines’ IP addresses for all targeted attacks in 2011. It doesn’t necessarily represent the location of the perpetrators.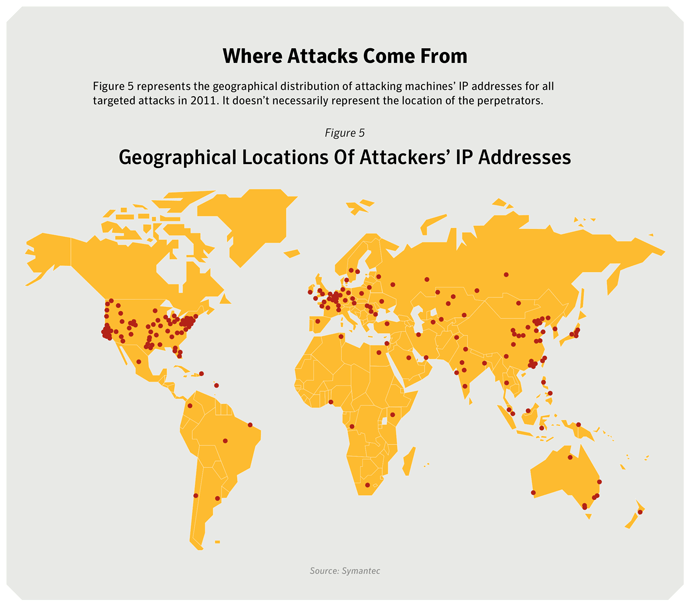
Case study
In 2011, we saw 29 companies in the chemical sector (among others) targeted with emails that appeared to be meeting invitations from known suppliers. These emails installed a well-known backdoor trojan with the intention of stealing valuable intellectual property such as design documents and formulas.Against the Breach: Securing Trust and Data Protection
Data Breaches in 2011
2011 was the year of data breaches. Analysis of the industry sectors showed that companies in the Computer Software, IT and healthcare sectors accounted for 93.0% of the total number of identities stolen. It is likely that hackers perceived some of the victims as softer targets, focused on consumer markets and not information security. Theft or loss was the most frequent cause, across all sectors, accounting for 34.3%, or approximately 18.5 million identities exposed in 2011.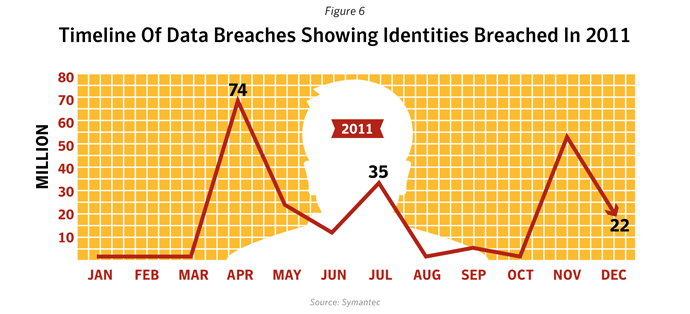
Certificate Authorities under attack
Certificate Authorities (CAs), which issue SSL certificates that help encrypt and authenticate websites and other online services, saw an unprecedented number of attacks in 2011.- March: An attack compromised the access credentials of a Comodo partner in Italy and used the partner’s privileges to generate fraudulent SSL certificates .
- May: It was reported that another Comodo partner was hacked: ComodoBR in Brazilx.
- June: StartCom, the CA operating StartSSL was attacked unsuccessfully in Junexi.
- June: Diginotar was hacked in June. But no certificates were issued at firstxii.
- July: An internal audit discovered an intrusion within DigiNotar’s infrastructure indicating compromise of their cryptographic keys. Fraudulent certificates are issued as a result of the DigiNotar hack for Google, Mozilla add-ons, Microsoft Update and othersxiii.
- August: Fraudulent certificates from the DigiNotar compromise are discovered in the wild. Hacker (dubbed ComodoHacker) claims credit for Comodo and DigiNotar attacks and claims to have attacked other certificate authorities as well. Hacker claims to be from Iran.
- September: Security researchers demonstrate “Browser Exploit Against SSL/TLS” (BEAST for short)xiv, a technique to take advantage of a vulnerability in the encryption technology of TLS 1.0, a standard used by Browsers, Servers and Certificate Authorities.
- September: GlobalSign attacked, although the Certificate Authority was not breached, their web server was compromisedxv., but nothing elsexvi. ComodoHacker claims credit for this attack as well.
- September: Dutch government and other Diginotar customers suddenly had to replace all Diginotar certificates as the major Web browser vendors removed Diginotar from their trusted root storesxvii. DigiNotar files for bankruptcy.
- November: Digicert Sdn. Bhd (Digicert Malaysia) an intermediate certificate authority that chained up to Entrust (and is no relation to the well-known CA, DigiCert Inc.) issued certificates with weak private keys and without appropriate usage extensions or revocation information. As a result Microsoft, Google and Mozilla removed the Digicert Malaysia roots from their trusted root storesxviii. This was not as the result of a hacking attack; this was a result of poor security practices by Digicert Sdn. Bhd.
Building Trust and Securing the Weakest Links
Law-abiding users have a vested interest in building a secure, reliable, trustworthy Internet. The latest developments show that the battle for end-users’ trust is still going on:- Always On SSL. Online Trust Alliancexix endorses Always On SSL, a new approach to implementing SSL across a website. Companies like Facebookxx, Google, PayPal, and Twitterxxi are offering users the option of persistent SSL encryption and authentication across all the pages of their services (not just login pages). Not only does this mitigate man-in-the-middle attacks like Firesheepxxii, but it also offers end-to-end security that can help secure every Web page that visitors to the site use, not just the pages used for logging-in and for financial transactions.
- Extended Validation SSL Certificates. EV SSL Certificates offer the highest level of authentication and trigger browsers to give users a very visible indicator that the user is on a secured site by turning the address bar green. This is valuable protection against a range of online attacks. A Symantec sponsored consumer survey of internet shoppers in Europe, the US and Australia showed the SSL EV green bar increases the feeling of security for most (60%) shoppersxxiii. Conversely, in a US online consumer study, 90% of respondents would not continue a transaction if they see a browser warning page, indicating the absence of a secure connectionxxiv.
- Baseline Requirements for SSL/TLS Certificates. The CA/Browser Forum released “Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates”, the first international baseline standard for the operation of Certification Authorities (CAs) issuing SSL/TLS digital certificates natively trusted in browser software. The new baseline standard was announced in December 2011 and goes into effect July 1, 2012.
- Code signing certificates and private key security. High profile thefts of code signing private keys highlighted the need for companies to secure and protect their private keys if they hold digital certificatesxxv. Stealing code signing keys enables hackers to use those certificates to digitally sign malware and that can help to make attacks using that malware much harder to recognize. That is exactly what happened with the Stuxnet and Duqu attacks.
- DNSSEC. This technology is gaining momentum as a method of preserving the integrity of the domain name system (DNS). However, it is not a panacea for all online security needs, it does not provide website identity authentication nor does it provide encryption. DNSSEC should be used in conjunction with Secure Sockets Layer (SSL) technology and other security mechanisms.
- Legal requirements. Many countries, including the EU Member Statesxxvi and the United States (46 states) have at least sectoral data breach notification legislation, which means that companies must notify authorities and, where appropriate, affected individuals if their data is affected by a data breach. As well as a spur to encourage other territories with less regulation, these requirements can reassure users that in the event of a breach they will be quickly notified and will be able take some action to mitigate against potential impact, including changing account passwords.
Consumerization and Mobile Computing: Balancing the Risks and Benefits in the Cloud
Risks with ‘bring your own device’
Employees are increasingly bringing their own smartphones, tablets or laptops to work. In addition, many companies are giving employees an allowance or subsidy to buy their own computer equipment. These trends, known as ‘bring your own device’, present a major challenge to IT departments more used to having greater control over every device on the network. There is also the risk that a device owned by an employee might be used for non-work activity that may expose it to more malware than a device strictly used for business purposes only.Threats against mobile devices
Over the past ten years we have seen a proliferation of mobile devices but there has not yet been a corresponding rise in mobile threats on the same level as we have seen in PC malware. If we look at how PC malware evolved, there are three factors needed before a major increase of mobile malware will occur: a widespread platform, readily accessible development tools, and sufficient attacker motivation (usually financial). The first has been fulfilled most recently with the advent of Android. Its growing market share parallels the rise in the number of mobile threats during 2011.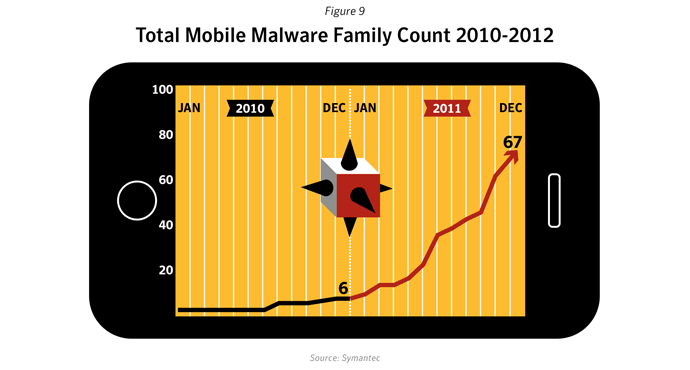
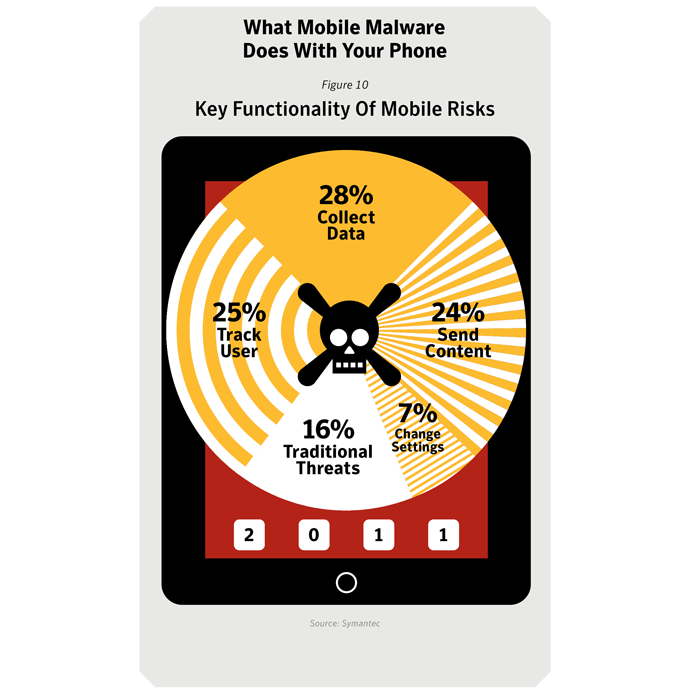
What mobile malware does with your phone
Consumerization of IT and cloud computing
As more people are bringing their own devices to work, consumer technology is invading the office.. They’re also using social networking sites for a variety of purposes, including marketing. And they’re using cloud applications instead of company-managed software to store files or communicate.Confidence in the Cloud: Balancing Risks
Many companies are keen to adopt cloud computing. It can reduce costs by outsourcing routine services, such as email or CRM, to third-party specialists and by swapping upfront capital expenditure with lower, more predictable per-user fees. It can also give companies access to newer and better technology without the difficulties of installing or upgrading in-house hardware.- Security and compliance - the interfaces between users, endpoints and backend systems all need to be secure with appropriate levels of access control in place.
- Is data encrypted as it is transferred over the internet?
- Non-compliance with data protection regulations –for example, if the data is hosted overseas, from a European standpoint this could result in a breach of privacy legislation.
- Lack of vendor validation – is the service reputable and secure? Can the users easily transfer their data to another vendor should the need arise?
- Public and private cloud providers depend on system availability and strong service level agreements (SLAs) can help to promote high availability.
- Secure access control over company data stored on third party systems. Does the service offer control over how the data is stored and how it can be accessed?
- If the service is unavailable for any reason, the company may be unable to access its own data.
- Are there legal risks and liabilities that may arise as a result of vendor terms and conditions? Always make sure the terms and conditions are clear and service level performance can be monitored against the agreed SLAs.
Spam Activity Trends
Spam in 2011
Despite a significant drop in email spam in 2011 (dropping to an average of 75.1% of all email in 2011 compared with 88.5% in 2010), spam continues to be a chronic problem for many organizations and can be a silent-killer for smaller businesses, particularly if their email servers become overwhelmed by millions of spam emails each day. With the power of botnets, robot networks of computers infected with malware and under the control of cybercriminals, spammers can pump out billions of spam emails every day, clogging-up company networks and slowing down communications. There were, on average, 42 billion spam messages a day in global circulation in 2011, compared with 61.6 billion in 2010.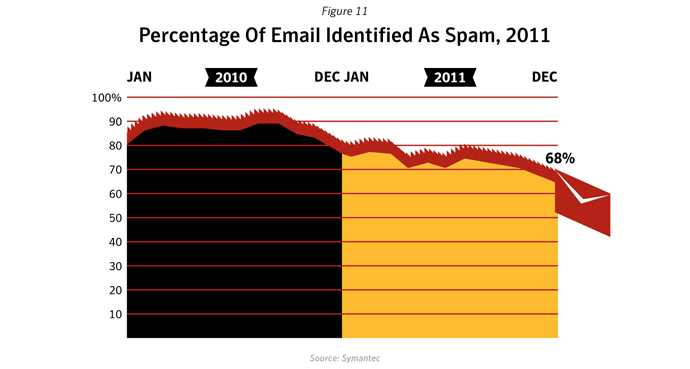
Impact of botnets on spam
Overall in 2011, botnets produced approximately 81.2% of all spam in circulation, compared with 88.2% in 2010. Between March 16th and March 17th, 2011, many Rustock command and control (C&C) servers located in the US were seized and shut down by US federal law enforcement agents, resulting in an immediate drop in the global spam volume from 51 billion spam messages a day in the week before the shutdown to 31.7 billion a day in the week afterwards.The changing face of spam
Between 2010 and 2011, pharmaceutical spam fell by 34%, in large part owing to the demise of the Rustock botnet, which was mainly used to pump-out pharmaceutical spam. In contrast, messages about watches and jewelry, and sex and dating both increased as a percentage. Not only were there fewer spam emails in circulation, but smaller message sizes were the most common and English remained the lingua franca of spamxxix, with Portuguese, Russian and Dutch the next most popular languages (albeit with a much smaller ‘market share’).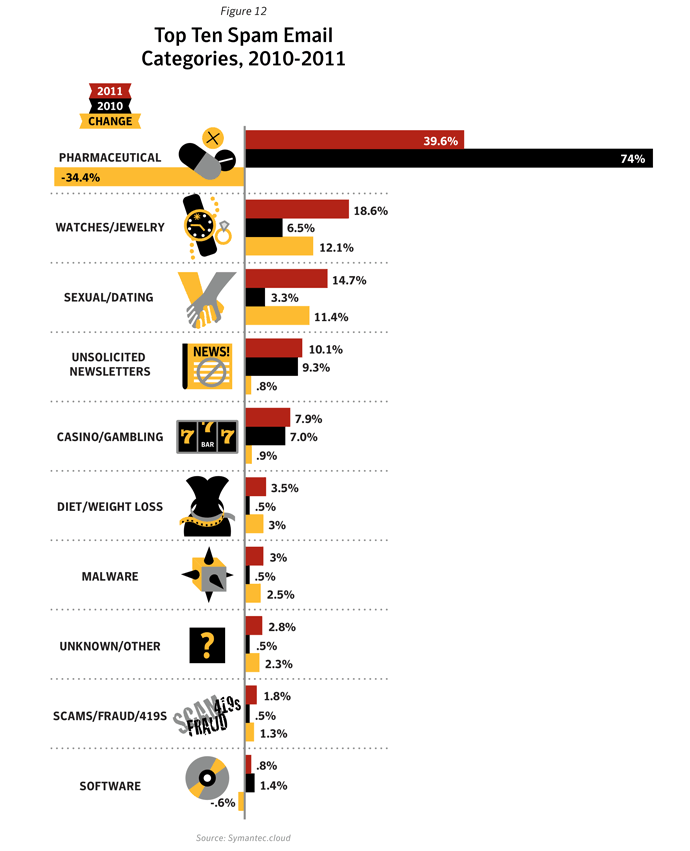
URL shortening and spam
Spammers are making greater use of URL shortening services, even establishing their own shortening services along the way. These sites take a long website address and shorten them, making them easier to share. This has many legitimate uses and is popular on social networking and micro-blogging sites. Spammers take advantage of these services to hide the true destination of links in their unwanted messages. This makes it harder for users to know what they are clicking on and it increases the work needed for spam filtering software to check if a link in an email is legitimate or not.Malicious Code Trends
Malware in 2011
By analyzing malicious code we can determine which threats types and attack vectors are being employed. The endpoint is often the last line of defense, but it can often be the first-line of defense against attacks that spread using USB storage devices, insecure network connections and compromised, infected websites. Symantec’s cloud-based technology and reputation systems can also help to identify and block new and emerging attacks that haven’t been seen before, such as new targeted attacks employing previously unknown zero-day exploits. Analysis of malware activity trends both in the cloud and at the endpoint can help to shed light on the wider nature of threats confronting businesses, especially from blended attacks and threats facing mobile workers.Website malware
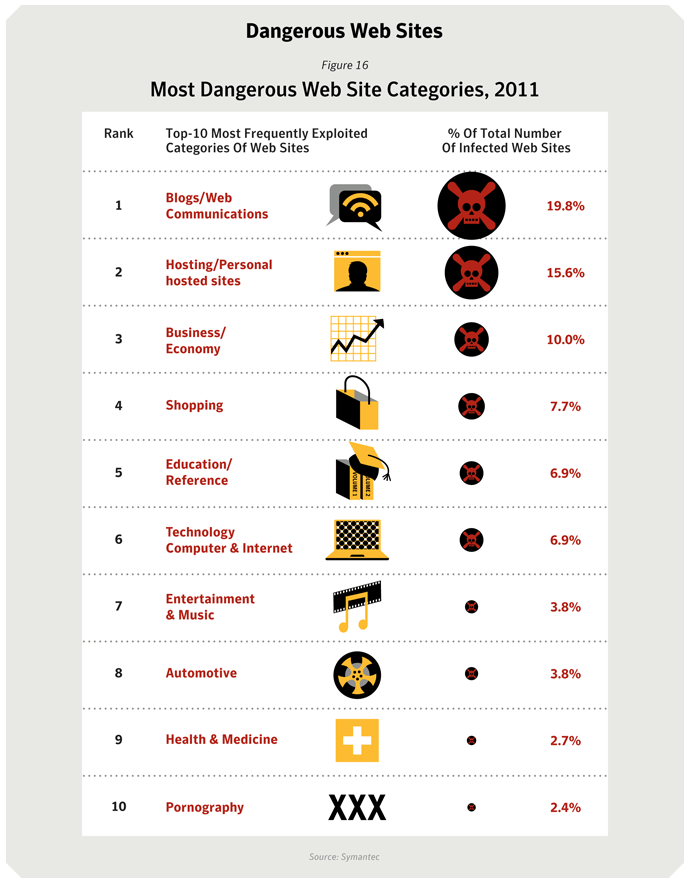
Drive-by attacks continue to be a challenge for consumers and businesses. They are responsible for hundreds of millions of attempted infections every year. This happens when users visit a website that is host to malware. It can happen when they click on a link in an email or a link from social networking site or they can visit a legitimate website that has, itself, been infected.- Blogs and Web communications
- Hosting/Personal hosted sites
- Business/Economy
- Shopping
- Education and Reference.
Email-borne Malware
The number of malicious emails as a proportion of total email traffic increased in 2011. Large companies saw the greatest rise, with 1 in 205.1 emails being identified as malicious for large enterprises with more than 2,500 employees. For small to medium-sized businesses with up to 250 employees, 1 in 267.9 emails were identified as malicious.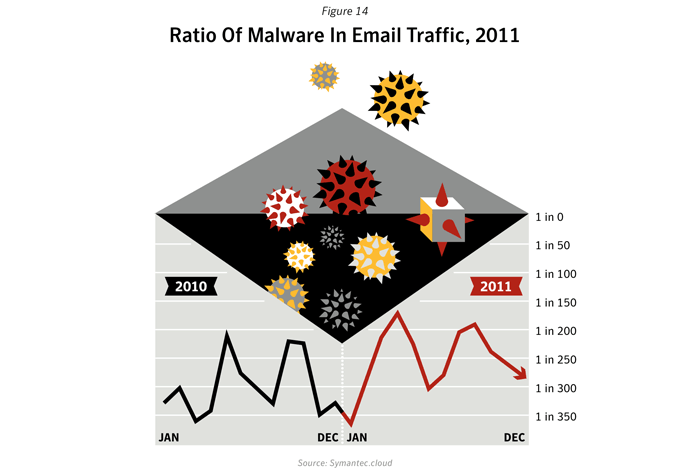
Border Gateway Protocol (BGP) Hijacking
In 2011 we investigatedxxxiii a case where a Russian telecommunications company had had its network hijacked by a spammer. They were able to subvert a fundamental Internet technology - the Border Gateway Protocol - itself to send spam messages that appeared to come from a legitimate (but hijacked) source. Since spam filters rely, in part, on blacklists of known spam senders, this technique could allow a spammer to bypass them. Over the course of the year, we found a number of cases like this. Even though this phenomenon remains marginal at this time, compared to spam sent from large botnets, it is one to watch in the coming year.Polymorphic threats
Polymorphic malware or specifically, “server-side” polymorphism is the latest escalation in the arms race between malware authors and vendors of scanning software. The polymorphic technique works by constantly varying the internal structure or content of a piece of malware. This makes it much more challenging for traditional pattern-matching based anti-malware to detect. For example, by performing this function on a Web server, or in the cloud, an attacker can generate a unique version of the malware for each attack.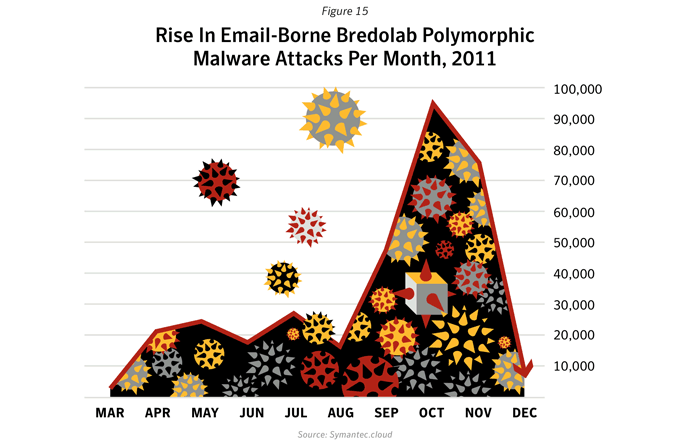
Exploiting the Web: Attack toolkits, rootkits and social networking threats
Attack toolkits, which allow criminals to create new malware and assemble an entire attack without having to write the software from scratch, account for nearly two-thirds (61%) of all threat activity on malicious websites. As these kits become more widespread, robust and easier to use, this number is expected to climb. New exploits are quickly incorporated into attack kits. Each new toolkit version released during the year is accompanied with increased malicious Web attack activity. As a new version emerges that incorporates new exploit functionality, we see an increased use of it in the wild, making as much use of the new exploits until potential victims have patched their systems. For example, the number of attacks using the Blackhole toolkit, which was very active in 2010, dropped to a few hundred attacks per day in the middle of 2011, but re-emerged with newer versions generating hundreds of thousands of infection attempts per day towards the end of the year.- Targeted attacks. The attacker selects a type of user he would like to target. The toolkit creates emails, IMs, blog posts to entice the target audience to the infected content. Typically, this will be a link to a malicious website that will install the malware on the victim’s system.
- Broadcast attacks. The attacker starts by targeting a broad range of websites using SQL injection, web software, or server exploitation. The objective is to insert a link from an infected website to a malicious site that will infect visitors. Once successful, each subsequent visitor will be attacked.
Rootkits
A rootkit is software that enables continued privileged access to a computer while actively hiding its presence from administrators by subverting standard operating system functionality. Rootkits have been around for some time—the Brain virus was the first identified rootkit to employ these techniques on the PC platform in 1986—and they have increased in sophistication and complexity since then.Social media threats
With hundreds of millions of people on social networking sites, it is inevitable that online criminals would attack them there. A social medium is perfect for social engineering: it’s easier to fool someone when they think they’re surrounded by friends. More than half of all attacks identified on social networking Web sites were related to malware hosted on compromised Blogs/Web Communications Web sites. This is where a hyperlink for a compromised Web site was shared on a social network. It is also increasingly used for sending spam messages for the same reasons.
Quick Response (QR) codes
QR codes have sprung up everywhere in the last couple of years. They are a way for people to convert a barcode into a Web site link using a camera app on their smartphone. It’s fast, convenient and dangerous. Spammers are already using it to promote black-market pharmaceuticals and malware authors have used it to install a trojan on Android phones. In combination with link shortening, it can be very hard for users to tell in advance if a given QR code is safe or not, so consider a QR reader that can check a Web site’s reputation before visiting it.Dangerous Web sites
Macs are not immune
The first known Mac-based bot network emerged in 2009 and 2011 saw a number of new threats emerge for Mac OS X, including trojans like MacDefender, a fake anti-virus program. It looks convincing and it installs without requiring admin permission first. Mac users are exposed to sites that push trojans by means of SEO poisoning and social networking. In May 2011, Symantec found a malware kit for Mac (Weyland-Yutani BOT) the first of its kind to attack the Mac OS X platform, and Web injections as a means of attack. While this type of crime kit is common on the Windows platform, this new Mac kit is being marketed as the first of its kindxxxiiv. In addition, many attack tools have become cross-platform, exploiting Java exploits whether they are on Macs or Windows PCs. As a result of these trends, Mac users need to be more mindful of security risks and can’t afford to assume that they are automatically immune from all threats.
Closing the Window of Vulnerability: Exploits and Zero-day Attacks
Number of vulnerabilities
We identified 4,989 new vulnerabilities in 2011, compared to 6,253 the year before. (See Appendix D for more historical data and details on our methodology.) Despite this decline, the general trend over time is still upward and Symantec discovered approximately 95 new vulnerabilities per week.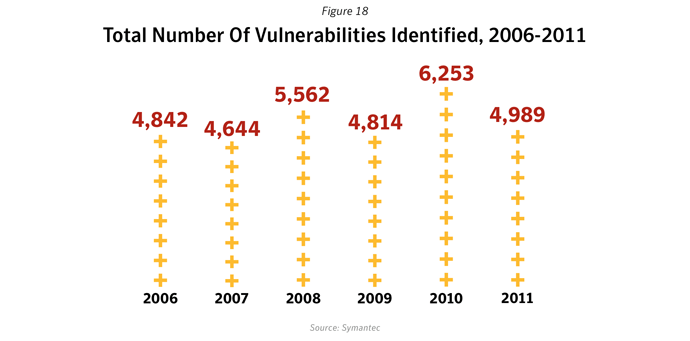
Weaknesses in critical infrastructure systems
SCADA systems (Supervisory Control and Data Acquisition) are widely used in industry and utilities such as power stations for monitoring and control. We saw a dramatic increase in the number of publicly-reported SCADA vulnerabilities from 15 in 2010 to 129 in 2011. Since the emergence of the Stuxnet worm in 2010xxxv, SCADA systems have attracted wider attention from security researchers. However, 93 of the 129 new published vulnerabilities were the product of just one security researcher.Old vulnerabilities are still under attack
On PCs, a six-year old vulnerabilityxxxvi in many Microsoft operating systems was, by far, the most frequently attacked vulnerability in 2011, clocking in at over 61 million attacks against the Microsoft Windows RPC componentxxxvii. It was more heavily attacked than the next four vulnerabilities put togetherxxxviii.- They are cheaper to attack. Criminals have to pay a premium on black market exchangesxxxix for information about newer vulnerabilities but they can buy malware off the shelf to target old ones.
- Attacking newer vulnerabilities may attract more attention than going after older, well-known weaknesses. Some online criminals prefer a lower profile.
- There is a still a large pool of potential victims because a proportion of the user base can’t, won’t or don’t install patches or install a current and active endpoint security product.
Web browser vulnerabilities
Web browsers are a popular target for criminals and they exploit vulnerabilities in browsers such as Internet Explorer, Firefox or Chrome as well as plugins such as PDF readers. Criminals can buy toolkits for between USD $100 and USD $1,000 that will check up to 25 different vulnerabilities when someone visits an infected Web site.New zero-day vulnerabilities create big risks
A zero-day attack exploits an unreported vulnerability for which no vendor has released a patch. This makes them especially serious because they are much more infective. If a non-zero-day attack gets past security, it can still be thwarted by properly-patched software. Not so a zero-day attack.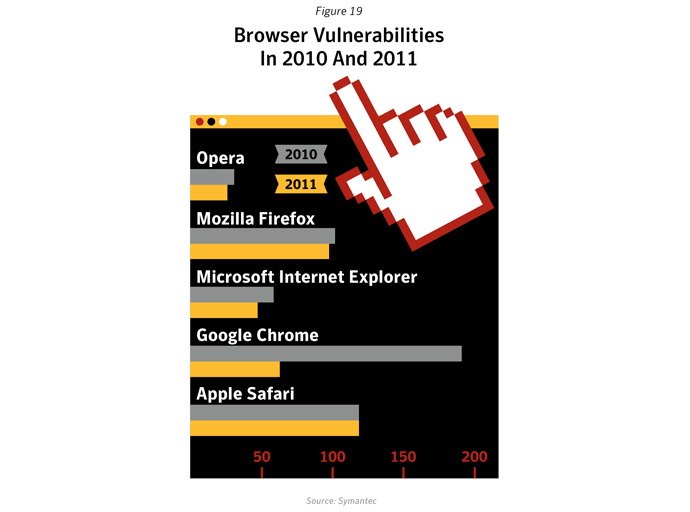
Conclusion: What’s Ahead in 2012
- Targeted attacks and APTs will continue to be a serious issue and the frequency and sophistication of these attacks will increase.
- Techniques and exploits developed for targeted attacks will trickle down to the broader underground economy and be used to make regular malware more dangerous.
- Malware authors and spammers will increase their use of social networking sites still further.
- The CA/Browser Forum will release additional security standards for companies issuing digital certificates to secure the internet trust model against possible future attacks.
- Consumerization and cloud computing will continue to evolve, perhaps changing the way we do business and forcing IT departments to adapt and find new ways to protect end users and corporate systems.
- Malware authors will continue to explore ways to attack mobile phones and tablets and, as they find something effective and money-making, they will exploit it ruthlessly.
- In 2011, malicious code targeting Macs was in wider circulation as Mac users were exposed to websites that were able to drop trojans. This trend is expected to continue through 2012 as attack code exploiting Macs becomes more integrated with the wider web-attack toolkits.
- While external threats will continue to multiply, the insider threat will also create headlines, as employees act intentionally – and unintentionally – to leak or steal valuable data.
- The foundation for the next Stuxnet-like APT attack may have already been laid. Indeed Duqu may have been the first tremors of a new earthquake, but it may take longer for the aftershock to reach the public domain.
Threat Activity Trends
- Threat Activity Trends
- Malicious Activity by Source
- Malicious Website Activity
- Analysis of Malicious Web Activity by Attack Toolkits
- Analysis of Web-based Spyware and Adware Activity
- Analysis of Web Policy Risks from Inappropriate Use
- Analysis of Website Categories Exploited to Deliver Malicious Code
- Bot-infected Computers
- Analysis of Mobile Threats
- Data Breaches that Could Lead to Identity Theft
Spam and Fraud Activity Trends
- Malicious code: This includes programs such as viruses, worms, and Trojans that are covertly inserted into programs. The purposes of malicious code include destroying data, running destructive or intrusive programs, stealing sensitive information, or compromising the security or integrity of a victim’s computer data.
- Spam zombies: These are remotely controlled, compromised systems specifically designed to send out large volumes of junk or unsolicited email messages. These email messages can be used to deliver malicious code and phishing attempts.
- Phishing hosts: A phishing host is a computer that provides website services in order to illegally gather sensitive user information while pretending that the attempt is from a trusted, well-known organization by presenting a website designed to mimic the site of a legitimate business.
- Bot-infected computers: Malicious programs have been used to compromise these computers to allow an attacker to control the targeted system remotely. Typically, a remote attacker controls a large number of compromised computers over a single, reliable channel in a botnet, which can then be used to launch coordinated attacks.
- Network attack origins: This measures the originating sources of attacks from the Internet. For example, attacks can target SQL protocols or buffer overflow vulnerabilities.
- Web-based attack origins: This measures attack sources that are delivered via the Web or through HTTP. Typically, legitimate websites are compromised and used to attack unsuspecting visitors.
Methodology
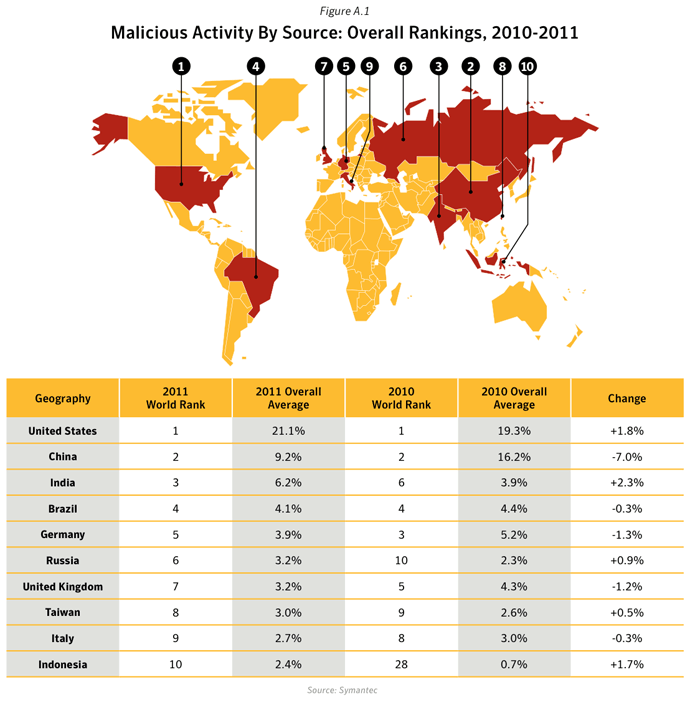
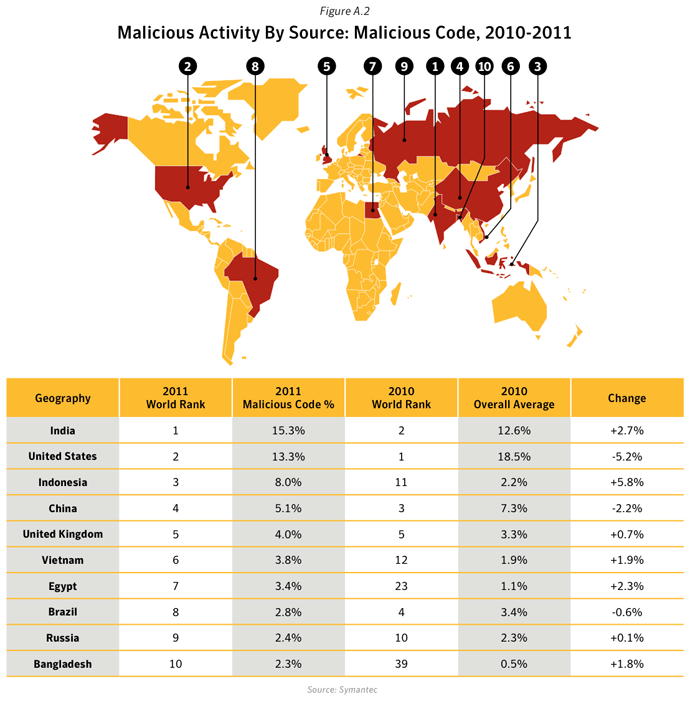
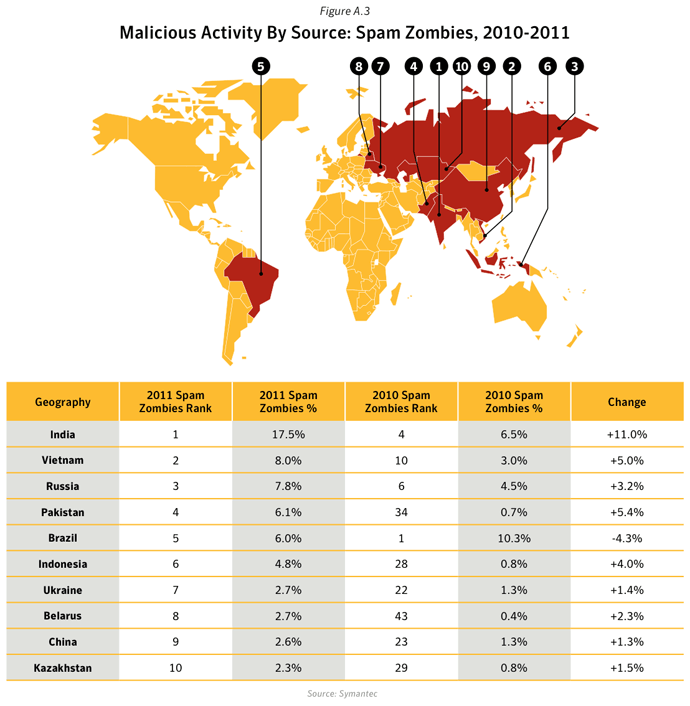
This metric assesses the sources from which the largest amount of malicious activity originates. To determine malicious activity by source, Symantec has compiled geographical data on numerous malicious activities, namely: malicious code reports, spam zombies, phishing hosts, bot-infected computers, network attack origins, and Web-based attack origins. The proportion of each activity originating in each source is then determined. The mean of the percentages of each malicious activity that originates in each source is calculated. This average determines the proportion of overall malicious activity that originates from the source in question and the rankings are determined by calculating the mean average of the proportion of these malicious activities that originated in each source.Data
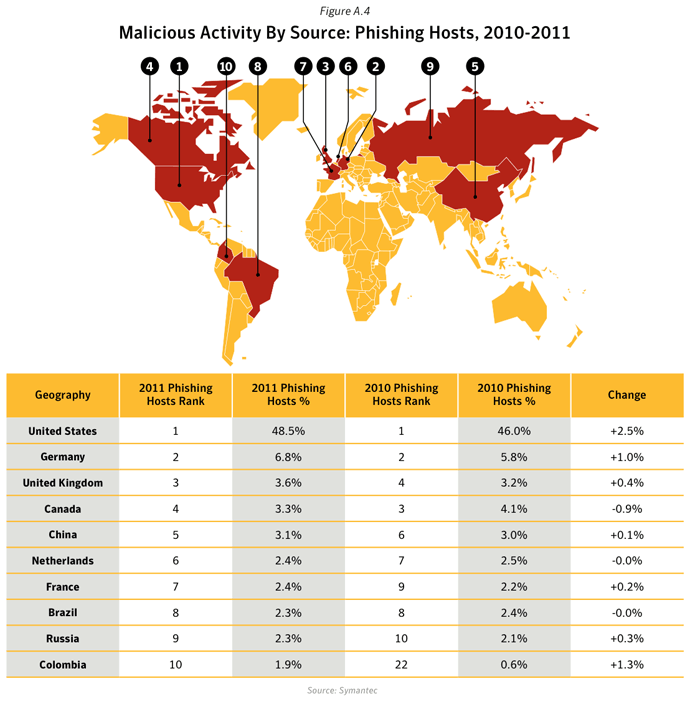
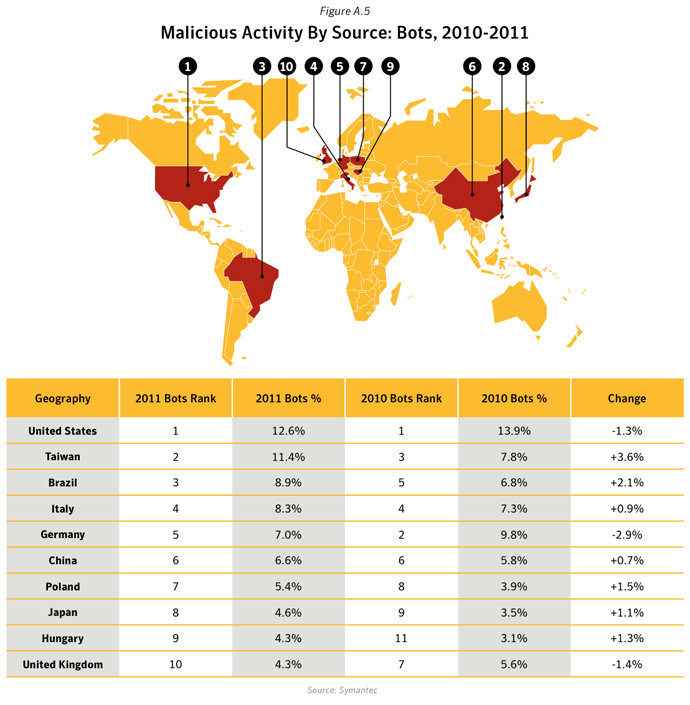
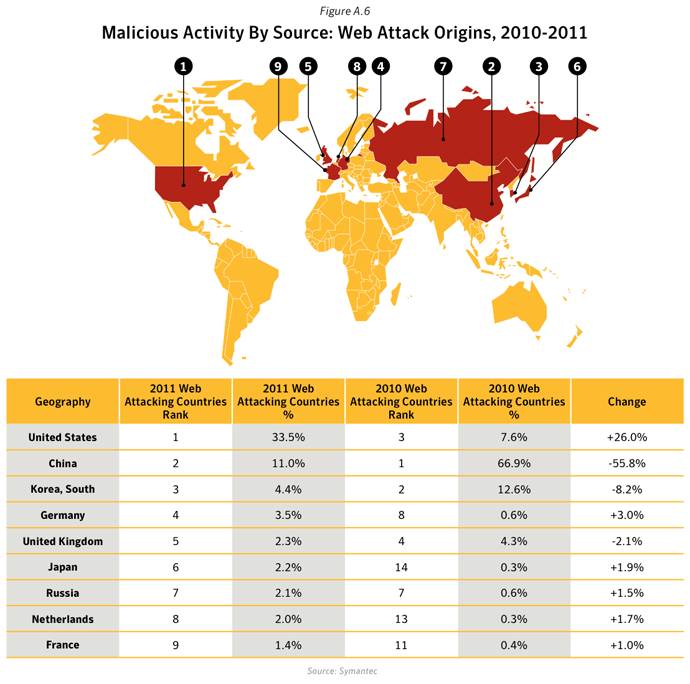
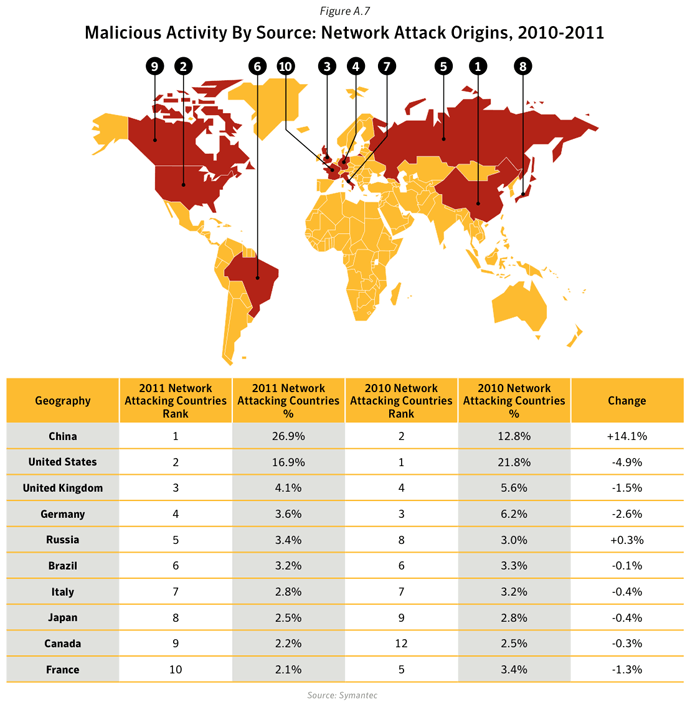
Commentary
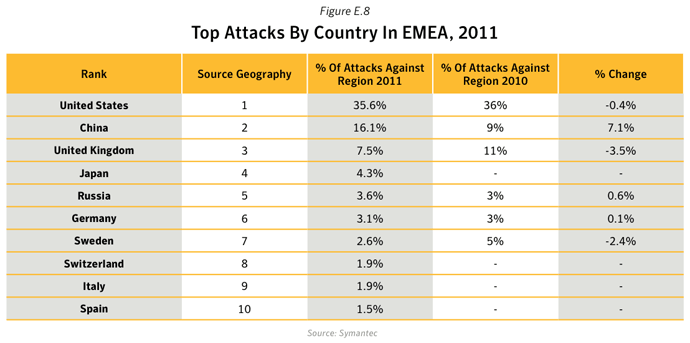
- In 2011, the United States and China remained the top two sources overall for malicious activity. The overall average proportion of attacks originating from the United States in 2011 increased by 1.8 percentage points compared with 2010, while the same figure for China saw a decrease by approximately 7 percentage points compared with 2010.
- The United States was ranked in first position for the source of all activities except for Malicious Code, Spam Zombies and Network Attacks, for which India was ranked in first position in the first two cases, and China the latter.
- 12.6% of bot activity originated in The United States: The United States was already the main source of bot-infected computers for the Rustock until in March 20111, when the botnet was disrupted. Rustock had been one of the largest and most dominant botnets in 2010 and frequently associated with the Tidserv Trojan. Rustock was estimated to comprise of approximately 1.5 million bot-infected computers and was taken out of action in March 2011. This resulted in a seismic shift in the botnet landscape. By the end of 2011, other botnets with spam zombies in other parts of the world were able to take on a more dominant role in spam distribution.
- 33.5% of Web-based Attacks originated in the United States: Web-based attacks originating from the United States increased by 26.0 percentage points in 2011. Factors that contributed to this activity include attacks related to the Blackhole and Phoenix Web attack kits, exploiting legitimate websites that have been compromised in order to conduct further attacks. Web-based attacks originating from China decreased by 55.8 percentage points in 2011.
- 26.9% of Network Attacks originated in China. China has the largest population of Internet users2 in the Asia region, with approximately 513 million internet users in 2011. The internet penetration rate in China was 38.4% in 2011.
- 48.5% of Phishing websites were hosted in the United States. In 2011, with approximately 245 million internet users, The United States had an internet penetration rate of 78.3%.
- 17.5% of Spam Zombies were located in India, an increase of 11.0 percentage points compared with 2010. The proportion of spam zombies located in the United States fell by 6.4 percentage points to 1.8%, resulting in the United States being ranked in 15th position in 2011, compared with 2nd position in 2010. This decline was in large part as a result of the disruption of the Rustock botnet, which at its peak in 2010 had an estimated 1.5M computers under its control.
- 15.3% of all Malicious Code activities originated from India, an increase of 2.7 percentage points compared with 2010. India is home to the second largest population of internet users in Asia in 2011, with an estimated 121.0 million users and an Internet penetration rate of 10.2%.
Malicious Website Activity
Background
The circumstances and implications of Web-based attacks vary widely. They may target specific businesses or organizations, or they may be widespread attacks of opportunity that exploit current events, zero-day vulnerabilities, or recently patched and publicized vulnerabilities that some users have yet to protect themselves against. While major attacks may have individual importance and often receive significant attention when they occur, examining overall Web-based attacks provides insight into the threat landscape and how attack patterns may be shifting. Analysis of the underlying trend can provide insight into potential shifts in Web-based attack usage and can assist in determining if attackers are more or less likely to employ Web-based attacks in the future.Methodology
This metric assesses changes to the prevalence of Web-based attack activity by tracking the trend in the average number of malicious websites blocked each day by users of Symantec.cloud Web security services, for websites that have been compromised and contain malicious code. Underlying trends observed in the sample data provide a reasonable representation of overall malicious Web-based activity trends.Data
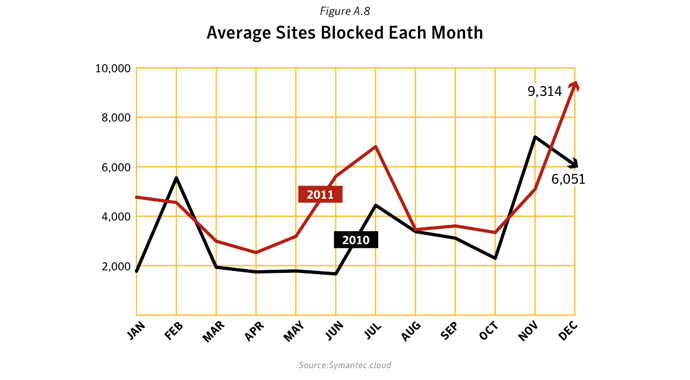
Commentary
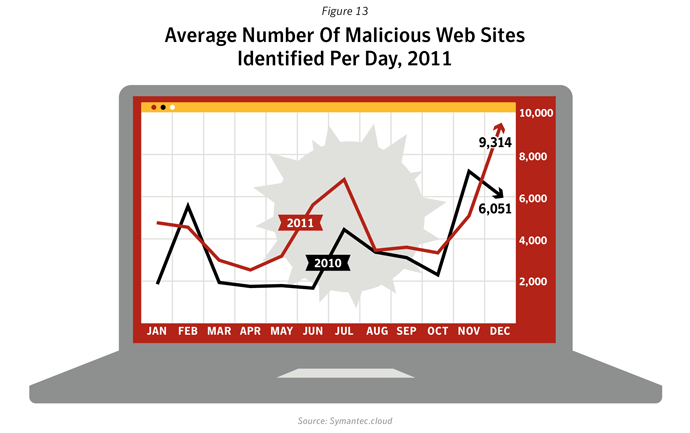
- The average number of malicious websites blocked each day rose by 36.0% in 2011 to 4,595, compared with 3,379 in 2010.
- The peak rate of malicious activity was 9,315 in December 2011, when approximately double the average number of malicious websites was being blocked each day. This increase was related to a rise in the number of malicious IFRAME tags being blocked. Detection for a malicious IFRAME is triggered in HTML files that contain hidden IFRAME elements with JavaScript code that attempts to perform malicious actions on the computer; for example, when visiting a malicious Web page, the code attempts to quietly direct the user to a malicious URL while the current page is loading.
- In 2011, the number of malicious domains blocked rose to 55,294 compared with 42,926 in 2010, an increase of 28.8%.
- Further analysis of malicious code activity may be found in Appendix X: Malicious Code Trends - Top Malicious Code Families.
Analysis of Malicious Web Activity by Attack Toolkits
Background
The increasing pervasiveness of Web browser applications, along with increasingly common, easily exploited Web browser application security vulnerabilities, has resulted in the widespread growth of Web-based threats. Attackers wanting to take advantage of client-side vulnerabilities no longer need to actively compromise specific networks to gain access to those computers. Symantec analyzes attack activity to determine which types of attacks and attack toolkits attackers are utilizing. This can provide insight into emerging Web attack trends and may indicate the types of attacks with which attackers are having the most success.Methodology
This metric assesses the top Web-based attack activity originating from compromised legitimate sites and intentionally malicious sites set up to target Web users in 2011. To determine this, Symantec ranks attack activity by the volume of associated reports observed during the reporting period. The top 10 Web-based attack activities are analyzed for this metric.Data
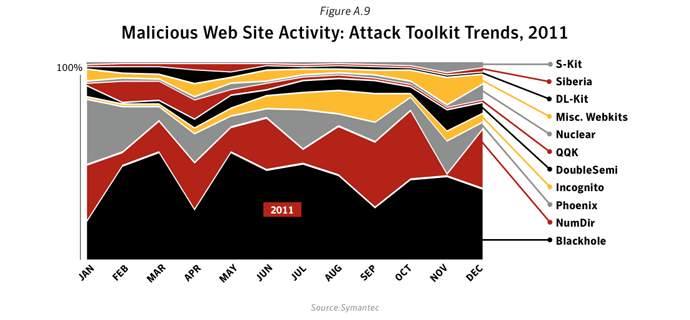
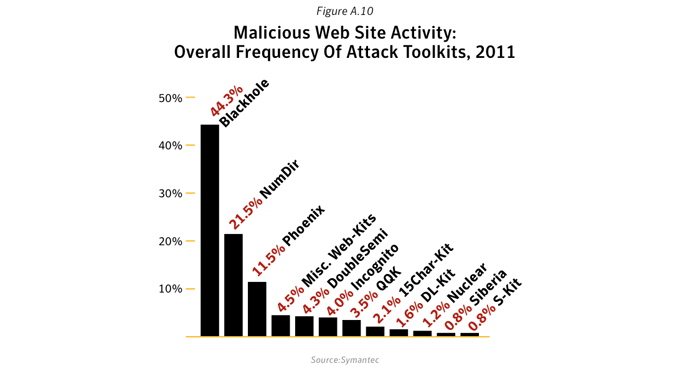
Commentary
Web-based client side exploit toolkits, or web-kits, have been around since about March of 2006 with the release of WebAttacker. For some time, these web-kits expanded their list of targeted victim software, but existed with essentially the same business model; nefarious users could purchase the attack kit and use it to build their hijacked computer networks. Once the market was established, prices steadily increased from WebAttacker’s $15 (USD) price tag on into the $1,000 (USD) range. The market existed in this fashion, with the web-kits including ever more exploits, and ever more IPS (Intrusion Prevention Systems) evasion techniques until about 2009 when web-kits began to be sold as a service, or simply kept as private.Public vs. Private web-kits
Symantec has seen a variety of web exploit kits sold in the public for several years now. Some are offered as a buy outright, service contract, or license models. Other web-kits on the other hand appear to remain private for their lifetime. In these cases, it is likely that the operators are either selling infected machines, or more likely using the infected machines in house.Payloads
The malware installed via a web-kit infection is frequently comprehensive, and includes various Peer-to-peer and IRC bots, rootkits, and misleading apps. Web-kits have been a major contributor to several pervasive malware families, including Qakbot, Bredolab, TidServe, ZeroAccess, Bamital, Zeus, Waledac, Zlob, Virut, Sasfis, Bank-stealing Trojans, Sality, Vundo, MebRoot, KoobFace and CycBot. For more information on these malware families, please visit http://www.symantec.com/security_response/.Analysis of Web-based Spyware and Adware Activity
Background
One of the main goals of a drive-by Web-based installation is the deployment of malicious code, but often a compromised website is also used to install spyware or adware code. This is because the cyber criminals pushing the spyware and adware in this way are being paid a small fee for each installation. However, most adware vendors, such as those providing add-in toolbars for Web browsers, are not always aware how their code came to be installed on the users’ computers; the expectation that is that it is with the permission of the end-user, when this is typically not the case in a drive-by installation and may be in breach of the vendors’ terms and conditions of use.Methodology
This metric assesses the prevalence of Web-based spyware and adware activity by tracking the trend in the average number of spyware and adware related websites blocked each day by users of Symantec.cloud Web security services. Underlying trends observed in the sample data provide a reasonable representation of overall malicious Web-based activity trends.Data
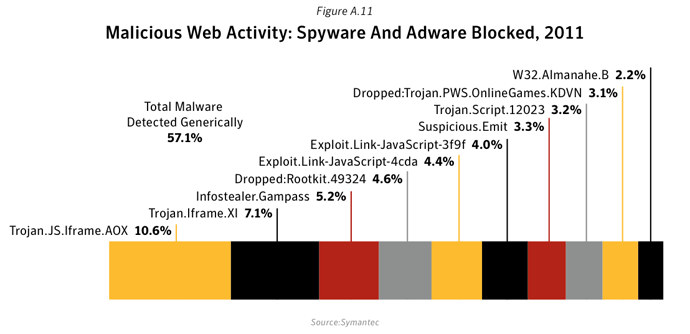
Commentary
- Only two examples of spyware were found in the top-ten list of unwanted programs in 2011, including Spyware.Perfect and Spyware.Keylogger. Spyware.Perfect is a program that tracks the keystrokes on the computer and logs them in a file. It can be configured to periodically send the log files by email.
- The most frequently blocked adware code was related to the Zugo search-based toolbar products and the FunWeb family of adware.
- Adware:W32/FunWeb is a family of adware programs that are used to display unsolicited advertising content, often through the use of pop-up windows. FunWeb variants are often bundled with other applications, games and browser plug-ins. Some variants of FunWeb may also redirect users’ browser home page and download additional code functionality.
- 57.1% of spyware and adware was detected using generic techniques.
Analysis of Web Policy Risks from Inappropriate Use
Background
Many organizations implement an acceptable usage policy to limit employees’ use of internet resources to a subset of Web sites that have been approved for business use. This enables an organization to limit the level of risk that may arise from users visiting inappropriate or unacceptable Web sites, such as those containing sexual images and other potentially illegal or harmful content. Often there will be varying degrees of granularity imposed on such restrictions, with some rules being applied to groups of users or rules that only apply at certain times of the day; for example, an organization may wish to limit employees access to video sharing Web sites to only Friday lunchtime, but may also allow any member of the PR and Marketing teams access at any time of the day. This enables an organization to implement and monitor its acceptable usage policy and reduce its exposure to certain risks that may also expose the organization to legal difficulties.Methodology
This metric assesses the classification of prohibited websites blocked by users of Symantec.cloud Web security services. The policies are applied by the organization from a default selection of rules that may also be refined and customized. This metric provides an indication of the potential risks that may arise from uncontrolled use of Internet resources.Data
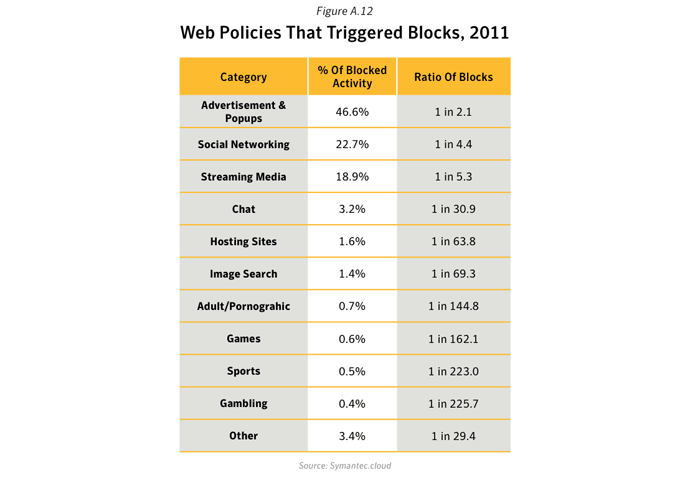
Commentary
- 46.6% of Web activity blocked through policy controls was related to Advertisement & Popups. Web-based advertisements pose a potential risk though the use of “malvertisements,” or malicious advertisements. These may occur as the result of a legitimate online ad-provider being compromised and a banner ad being used to serve malware on an otherwise harmless website.
- The second most frequently blocked traffic was categorized as Social Networking, accounting for 22.7% of policy-based filtering activity blocked, equivalent to approximately one in every 4 Web sites blocked. Many organizations allow access to social networking Web sites, but in some cases implement policies to only permit access at certain times of the day and block access at all other times. This information is often used to address performance management issues, perhaps in the event of lost productivity due to social networking abuse.
- Activity related to streaming media policies resulted in 18.9% of policy-based filtering blocks in 2011. Streaming media is increasingly popular when there are major sporting events or high profile international news stories. This activity often results in an increased number of blocks, as businesses seek to preserve valuable bandwidth for other purposes. This rate is equivalent to one in every 5 websites blocked.
Analysis of Website Categories Exploited to Deliver Malicious Code
Background
As organizations seek to implement appropriate levels of control in order to minimize risk levels from uncontrolled Web access, it is important to understand the level of threat posed by certain classifications of websites and categories in order to provide better understanding of the types of legitimate websites that may be more susceptible to being compromised and potentially expose users to greater levels of risk.Methodology
This metric assesses the classification of malicious Web-sites blocked by users of Norton Safe Web4 technology. Data is collected anonymously from over 50 million computers worldwide, where customers voluntarily contribute to this technology, including Norton Community Watch. Norton Safe Web is processing more than 2 billion real-time rating requests each day, and monitoring over 12 million daily software-downloads. Reputation ratings are being tracked for more than 25 million Web sites.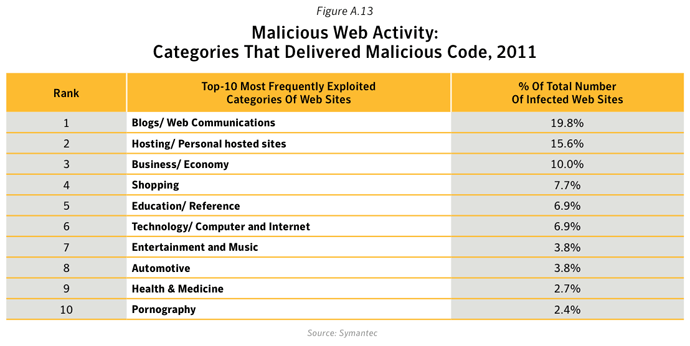
Commentary
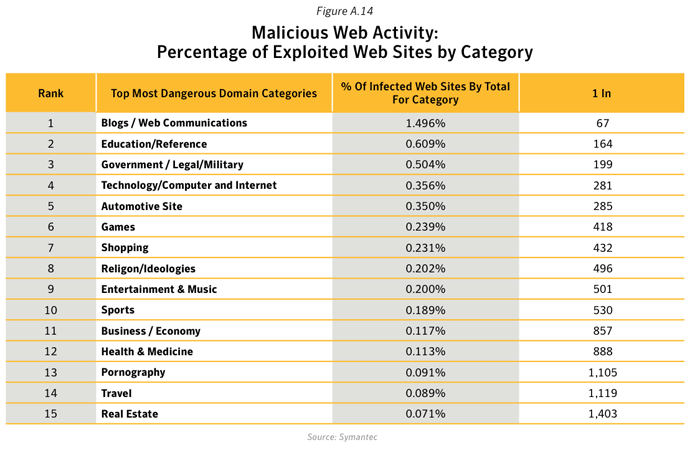
- Approximately 61% of Web sites used to distribute malware were identified as legitimate, compromised Web sites. This figure excludes URLs that contained just an IP address and did not include general domain parking and pay-per-click Web sites.
- 19.8% of malicious Web site activity on legitimate, compromised domains was classified in the Blogs and Web Communications category.
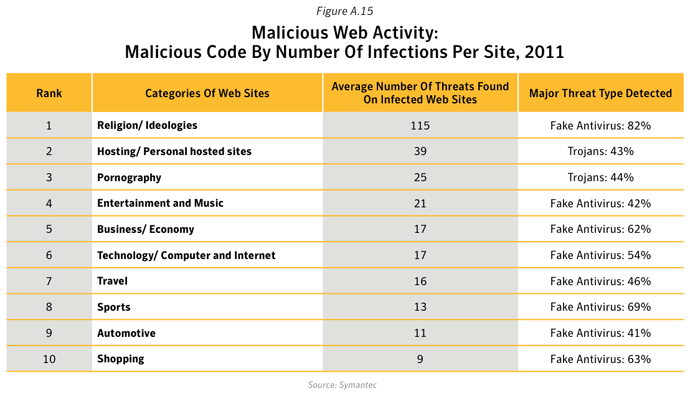
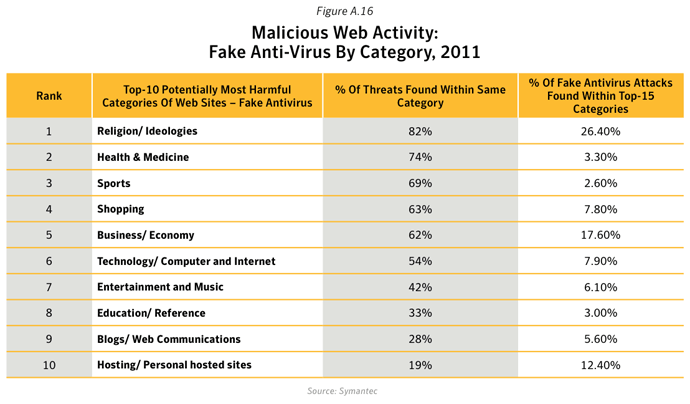
- Interestingly, pornographic Web sites were not exploited much overall, accounting for 2.4% of all infected Web sites; however, infected pornographic Web sites were found to host a greater number of threats than other categories (except for Religion/Ideologies and Hosting/Personal Hosted Sites – see below). Ranked in third position in figure A16, approximately 25 threats were identified on each infected pornographic Web site, with 44% of these threats being identified as Trojans.
- 1 in 67 web sites classified as Blogs/Web Communications were found to be compromised with potentially harmful malicious content, compared with 1 in 164 for Education/Reference.
- Web sites classified as Religion/Ideologies were found to host the greatest number of threats per site than other categories, with an average of 115 threats per Web sites, the majority of which related to Fake or Rogue Antivirus software.
- Analysis of Web sites that were used to deliver drive-by Fake Antivirus attacks revealed that 82% of threats found on compromised Religion/Ideologies Web sites were related to Fake Antivirus software. 26.4% of Fake Antivirus attacks were found on compromised Religion/Ideologies Web sites.
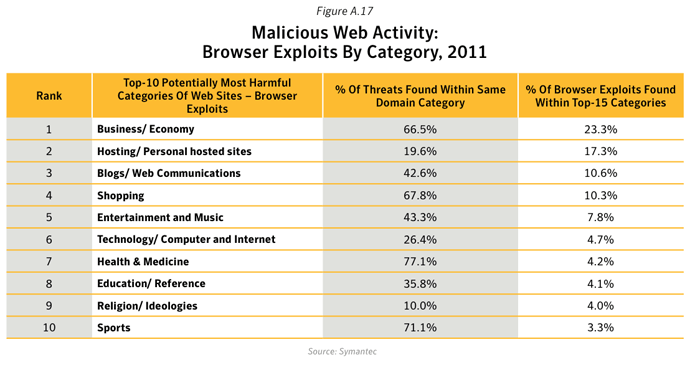
- Analysis of Web sites that were used to deliver attacks using browser exploits revealed that 66.5% of threats found on compromised Business / Economy Web sites were related to browser exploits. 23.3% of browser exploit attacks were found on compromised Business / Economy Web sites.
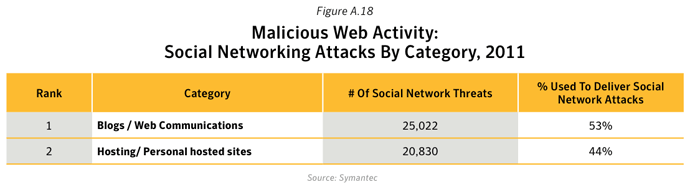
- 53% of attacks used on social networking Web sites were related to malware hosted on compromised Blogs / Web Communications Web sites. This is where a URL hyperlink for a compromised Web site is shared on a social network. Compromised Hosting/ Personal hosted sites similarly accounted for 44% of social networking attacks.
5For more details about Symantec Rulespace, please visit http://www.rulespace.com/
Bot-infected Computers
Background
Bot-infected computers, or bots, are programs that are covertly installed on a user’s machine in order to allow an attacker to control the targeted system remotely through a communication channel, such as Internet relay chat (IRC), P2P, or HTTP. These channels allow the remote attacker to control a large number of compromised computers over a single, reliable channel in a botnet, which can then be used to launch coordinated attacks.Methodology
A bot-infected computer is considered active on a given day if it carries out at least one attack on that day. This does not have to be continuous; rather, a single such computer can be active on a number of different days. A distinct bot-infected computer is a distinct computer that was active at least once during the period. Of the bot-infected computer activities that Symantec tracks, they can be classified as actively attacking bots or bots that send out spam, i.e. spam zombies.Data
Commentary
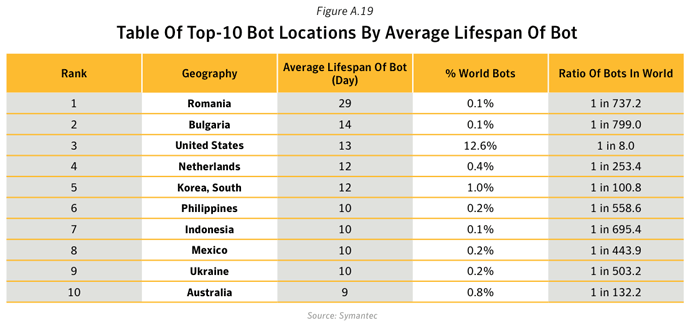
- Bots located in Romania were active for an average of 29 days in 2011; 1 in 737 of bots worldwide was located in Romania. Romania has one of the lowest fixed-broadband adoption rates in Europe, with fewer than 15%7 of households being connected to high-speed Internet access.
- It takes more than twice as long to identify and clean-up a bot-infected computer in Romania than in the United States, although the number of infections in the United States is on a magnitude of more than a hundred times greater than that of Romania. One factor contributing to this disparity may be a low level of user-awareness of the issues involved combined with the lower availability of remediation guidance and support tools in the Romanian language.
- In the United States, which was home to 1 in 8 (12.6%) of global bot-infected computers, the average lifespan for a bot was 13 days.
- Further analysis revealed that 65.2% of bots were controlled using HTTP-based command and control channels.
6Command and control 7http://ec.europa.eu/information_society/digital-agenda/scoreboard/pillars/broadband/index_en.htm
Analysis of Mobile Threats
Background
Since the first smartphone arrived in the hands of consumers, speculation about threats targeting these devices has abounded. While threats targeted early “smart” devices such as those based on Symbian and Palm OS in the past, none of these threats ever became widespread and many remained proof-of-concept. Recently, with the growing uptake in smartphones and tablets, and their increasing connectivity and capability, there has been a corresponding increase in attention, both from threat developers and security researchers.Methodology
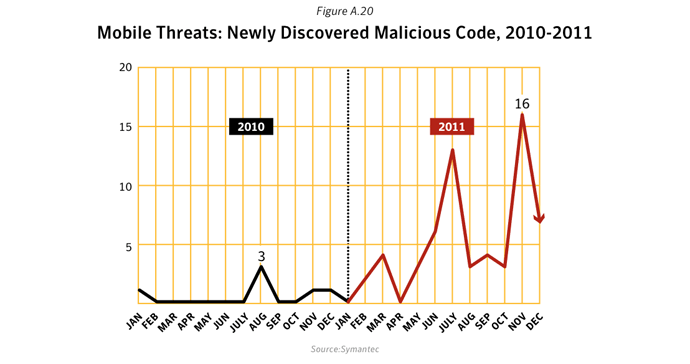
In 2011, there were a significant number of vulnerabilities reported that affect mobile devices. Symantec documented 315 vulnerabilities in mobile device operating systems in 2011, compared to 163 in 2010, an increase of 93.3%.Data
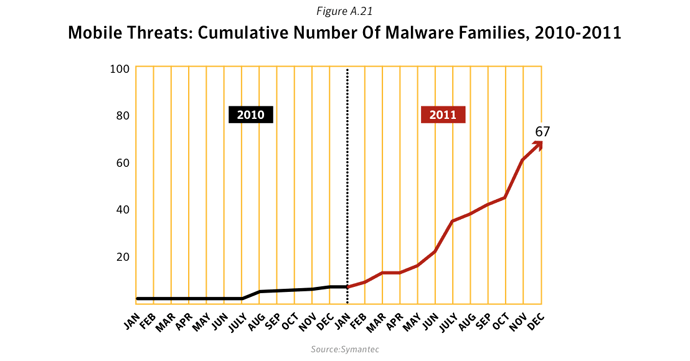
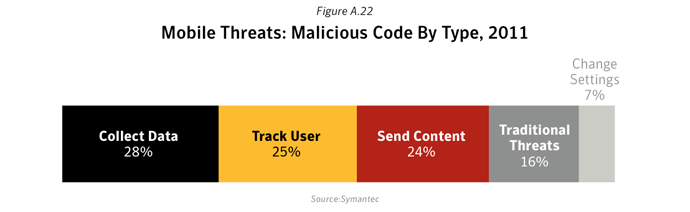
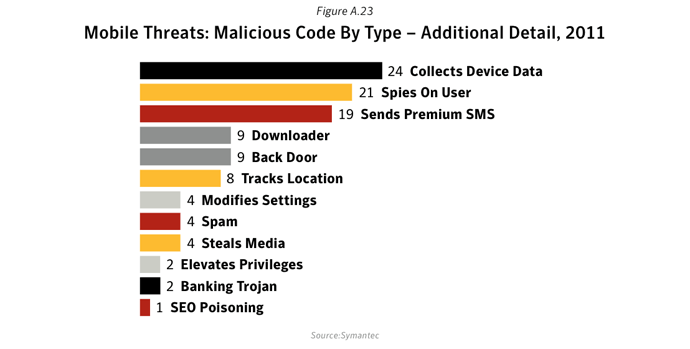 NB. For a more detailed breakdown of these larger categories: each
subcategory is color-coded to indicate with primary category above it
belongs to.
NB. For a more detailed breakdown of these larger categories: each
subcategory is color-coded to indicate with primary category above it
belongs to.The following are specific definitions of each subcategory:
- Collects Device Data—gathers information that is specific to the functionality of the device, such as IMEI, IMSI , operating system, and phone configuration data.
- Spies on User—intentionally gathers information from the device to keep monitor a user, such as phone logs and SMS messages, and sends them to a remote source.
- Sends Premium SMS—sends SMS messages to premium-rate numbers that are charged to the user’s mobile account.
- Downloader—can download other risks on to the compromised device.
- Back door—opens a back door on the compromised device, allowing attackers to perform arbitrary actions.
- Tracks Location—gathers GPS information from the device specifically to track the user’s location.
- Modifies Settings—changes configuration settings on the compromised device.
- Spam—sends spam email messages from the compromised device.
- Steals Media—sends media, such as pictures, to a remote source.
- Elevates Privileges—attempts to gain privileges beyond those laid out when installing the app bundled with the risk.
- Banking Trojan—monitors the device for banking transactions, gathering the sensitive details for further malicious actions.
- SEO Poisoning—periodically sends the phone’s browser to predetermined URLs in order to boost search rankings.
Commentary
Mobile applications (“apps”) with malicious intentions rose to prominence in 2011, presenting serious risks to users of mobile devices. These metrics show the different functions that these bad mobile apps performed during the year. The data was compiled by analyzing the key functionality of malicious mobile apps. Symantec has identified five primary mobile risk types:Growth in Android Threats
The Opfake family, a threat targeting Eastern Europe, is a good example. This threat was originally written for Windows Mobile/Symbian/JAVAME phones. Similar experiments have occurred in China where Android.Adsms and Android.Stiniter have appeared. Both originated as Symbian threats before the malware authors moved to Android. We expect this to be a common trend, especially among affiliate network related threatsOld tricks moving to new platforms
Premium SMS dialers have always been a problem on the mobile threat landscape, especially in Eastern Europe, where dialers showed up on mobiles phones not to long after the introduction of the micro edition of Java virtual machine for mobile devices. It should be no surprise that the authors who have been leveraging this lucrative revenue source appear to be making a switch to the newer, popular platforms.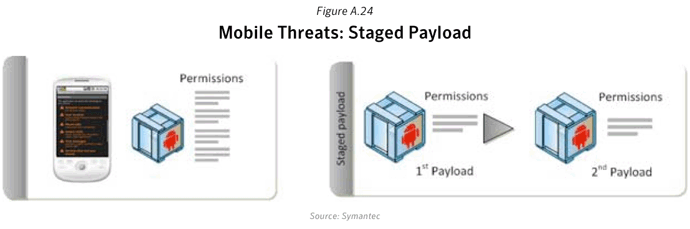

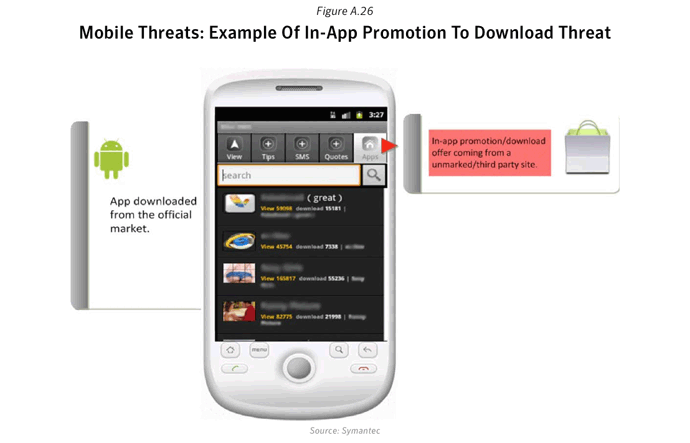
Social engineering a key tool used by mobile malware authors
Because of the so called “Hardware Fragmentation10” ” issue surrounding the Android Platform, a popular online streaming video service in the US; had initially pushed an Android client app in a limited release, only to certain devices that provided the best user experience.The rise of mobile threats with political agendas
Hactivism is not restricted to PC. Mobile malware with no visible monetary gain but instead with a goal is to send a message was seen in 2011. An example: for many across the Arab World, December 18 2010 marked the birth of what is now come to be commonly known as the ‘Arab Spring’. Among the many tools used to coordinate and inform, to get the word out about the mass ‘market protests’; Symantec discovered a Trojan mass mailer/downloader embedded in an Android App.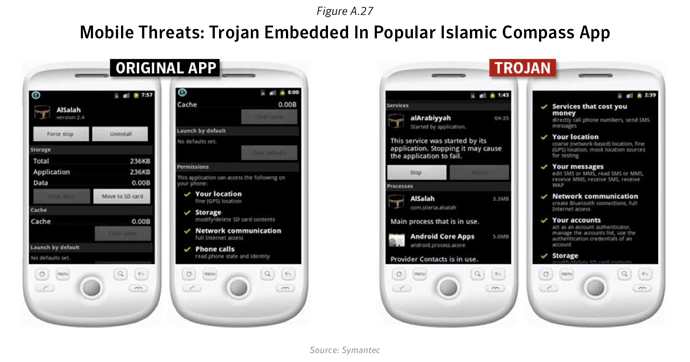
App Store here… App Store there… App everywhere….
With the projected growth of smart phone sales set to overtake that of regular featured phones, it’s no surprise to see the demand for content drive the emergence of new application market places, app stores, and download sites. Sales in 2011 alone are expected to bring in $15 billion dollars (USD).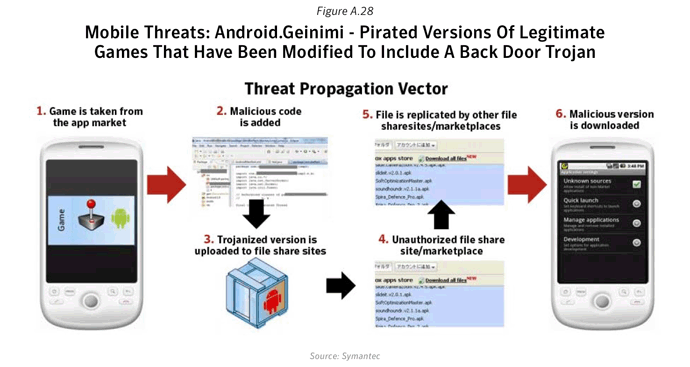

9International Mobile Subscriber Identity
10http://www.symantec.com/connect/blogs/hardware-fragmentation-thwarts-android-call-recording-trojan 11http://www.time.com/time/magazine/article/0,9171,2044723,00.htmlData Breaches that Could Lead to Identity Theft
Background
Political activism and hacking were two big themes resulting in data theft in 2011, and ones that continue to persevere into 2012. There were many high profile hacking breaches last year that received lots of media attention for obvious reasons. Hacking can undermine institutional confidence in a company, and loss of personal data can result in damage to an organizations reputation. Despite the media hype around these breaches, hacking came in second to old-fashioned theft as the greatest source of data breaches last year according to the Norton Cybercrime Index data12. In the event of a data breach, many countries have existing data breach notification legislation that regulates the responsibilities of organizations conducting business after a data breach has occurred. For example, the EU13, the United States (46 states)14, the District of Columbia, Puerto Rico, and the Virgin Islands have all enacted legislation requiring notification of security breaches involving personal information.Methodology
The data for the data breaches that could lead to identity theft is procured from the Norton Cybercrime Index (CCI). The Norton CCI is a statistical model which measures the levels of threats including malicious software, fraud, identity theft, spam, phishing and social engineering daily. Data for the CCI is primarily derived from Symantec Global Intelligence Network and for certain data from ID Analytics15. The majority of the Norton CCI's data comes from Symantec's Global Intelligence Network, one of the industry's most comprehensive sources of intelligence about online threats. The data breach section of the Norton CCI is derived from data breaches that have been reported by legitimate media sources and have exposed personal information, including name, address, Social Security numbers, credit card numbers, or medical history. Using publicly available data the Norton CCI determines the sectors that were most often affected by data breaches, as well as the most common causes of data loss.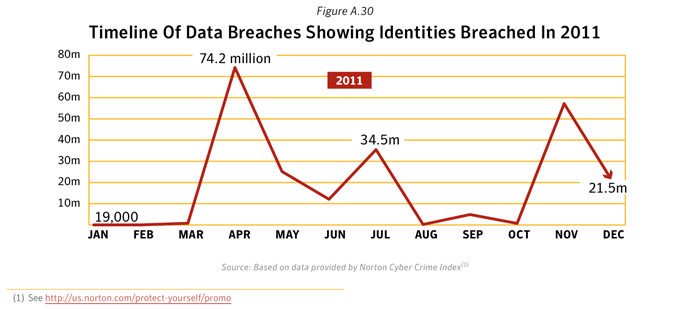
Data and commentary for Data and commentary for data breaches that could lead to identity theft by sector
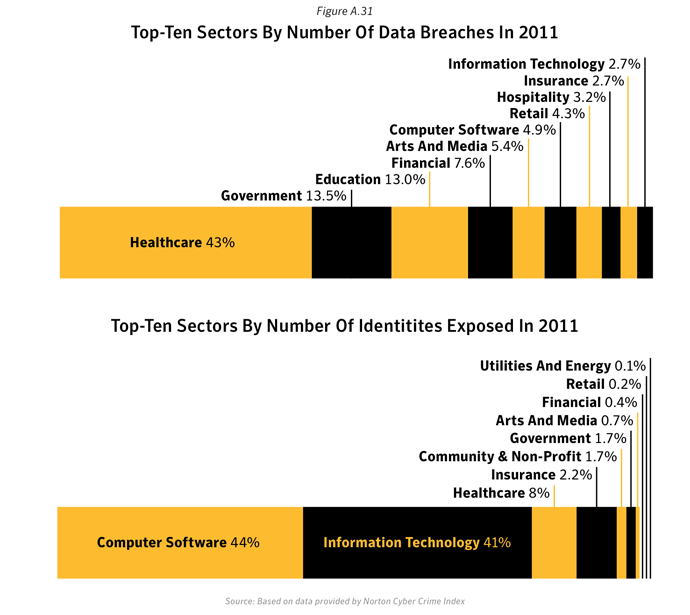
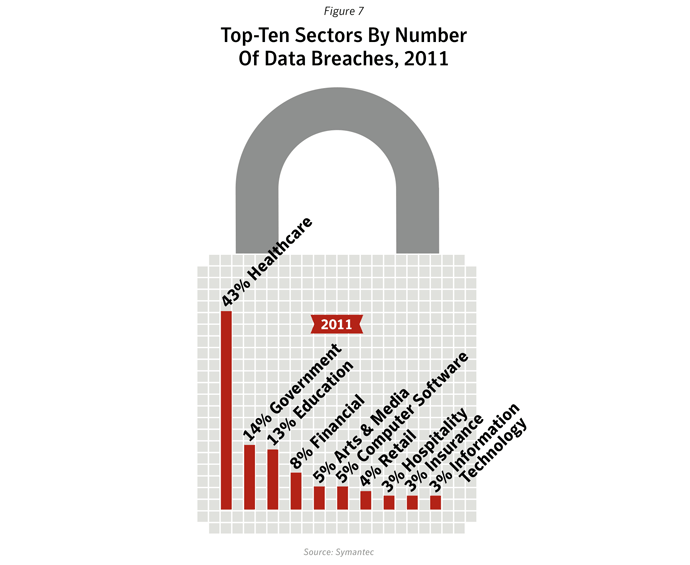
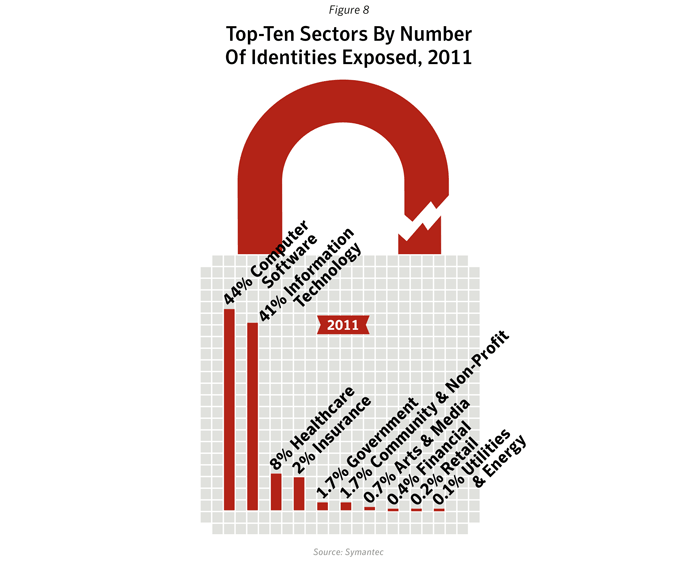
Top-ten sectors by number of data breaches
- Healthcare, government and education sectors ranked top for number of data breaches, but ranked lower for number of identities exposed: Although the healthcare, government and education sectors accounted for the top three largest percentages for number of data breaches in 2011, those breaches accounted for approximately 9.7% of all reported identities exposed during 2011 (figure A.31).
- This is due to the average number of identities exposed in each of the data breaches in these sectors being relatively low. The average number of identities exposed per data breach was approximately 133,500 for these three sectors combined, compared with an average of 19.4 million identities exposed per breach for the computer software sector alone (figure A.32).
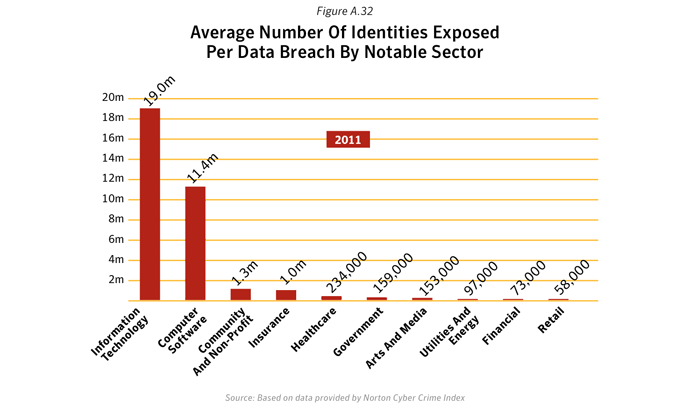
- Top data breaches are reflected in top sectors for identities exposed: The top three sectors of Computer Software, IT and Healthcare had the largest number of identities exposed due to data breaches in 2011; these three sectors accounted for 93.0% of the total number of identities exposed.
Data and commentary for data breaches that could lead to identity theft by cause
Top causes for data breach by number of breaches
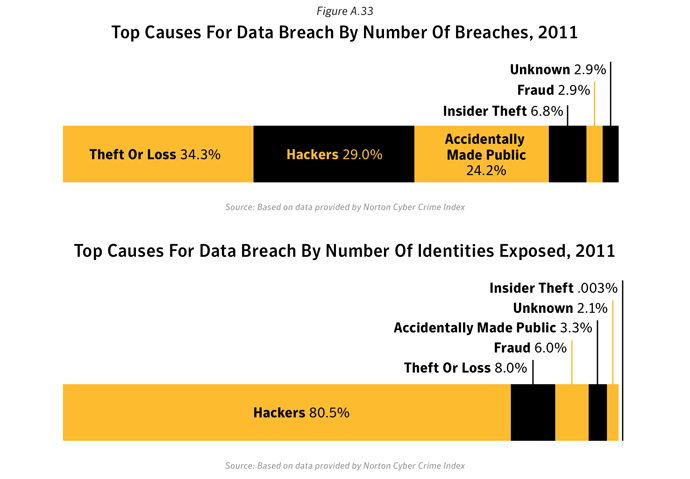
Top causes for data breach by number of identities exposed
- Theft or loss was the top cause for data breaches: The most frequent cause of data breaches (across all sectors) that could facilitate identity theft in 2011 was theft or loss of a computer or other medium on which data is stored or transmitted, such as a USB key or a back-up medium (figure A.33).
- Theft or loss accounted for 34.3% of breaches that could lead to identities exposed in 2011 and this equated to approximately 18.5 million identities exposed in total.
- The second most frequent data breach type was related to Hackers (29.0%), which exposed approximately 187.2 million identities in 2011, the greatest number for any cause of breach in 2011.
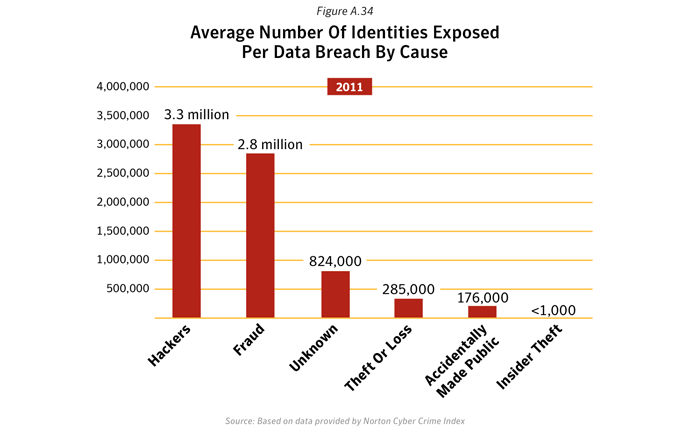
- Hacking was the leading source for reported identities exposed: Although hacking was the second most common cause of data breaches that could lead to identity theft in 2011, it was the top cause for the number of reported identities exposed. Hacking was responsible for over 80.5% of the identities exposed in the largest data breaches that occurred in 2011.
- The average number of identities exposed per data breach in Hacking incidents was approximately 3.3 million.
Data and Commentary for type of information exposed in deliberate breaches
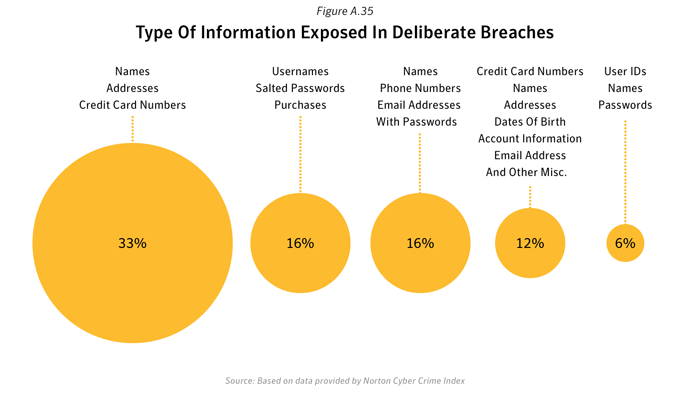
- The most common types of identity information leaked in deliberate data breaches was names, addresses and credit card numbers; accounting for one-third of the identities breached in 2011.
- Names, phone numbers, email addresses and passwords were found in 16% of breaches.
- Usernames, passwords and purchase information were identified in 16% of the identity breaches.
Vulnerability Trends
Total Number of Vulnerabilities
Background
The total number of vulnerabilities for 2011 is based on research from independent security experts and vendors of affected products. The yearly total also includes zero-day vulnerabilities that attackers uncovered and were subsequently identified post-exploitation. Calculating the total number of vulnerabilities provides insight into vulnerability research being conducted in the threat landscape. There are many motivations for conducting vulnerability research, including security, academic, promotional, software quality assurance, and, of course, the malicious motivations that drive attackers. Symantec gathers information on all of these vulnerabilities as part of its DeepSight vulnerability database and alerting services. Examining these trends also provides further insight into other topics discussed in this report.Methodology
Information about vulnerabilities is made public through a number of sources. These include mailing lists, vendor advisories, and detection in the wild. Symantec gathers this information and analyzes various characteristics of the vulnerabilities, including technical information and ratings in order to determine the severity and impact of the vulnerabilities. This information is stored in the DeepSight vulnerability database, which houses over 47,000 distinct vulnerabilities spanning a period of over 20 years. As part of the data gathering process, Symantec scores the vulnerabilities according to version 2.0 of the community-based CVSS (Common Vulnerability Scoring System)1. Symantec adopted version 2.0 of the scoring system in 2008. The total number of vulnerabilities is determined by counting all of the vulnerabilities published during the reporting period. All vulnerabilities are included, regardless of severity or whether or not the vendor who produced the vulnerable product confirmed them.Data
Commentary
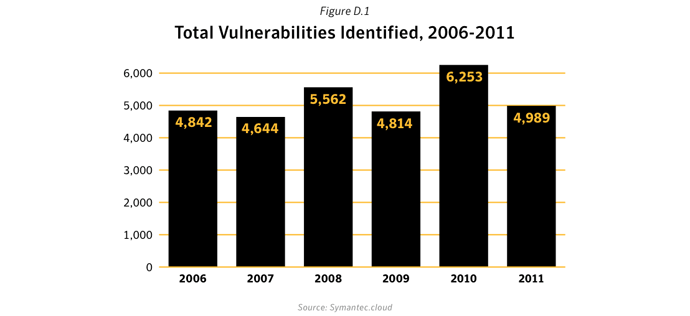
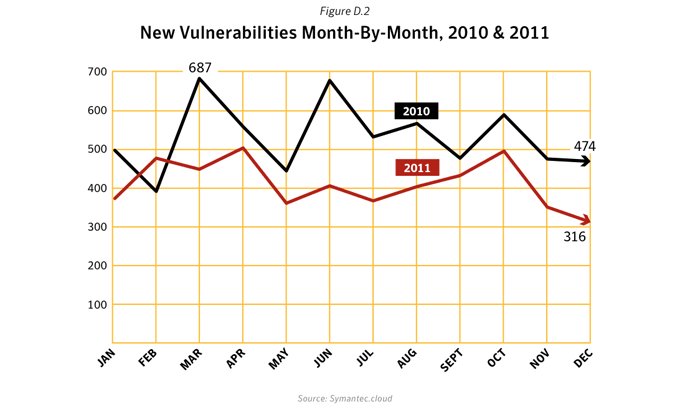
- Actual number of new vulnerabilities reported is down, but trend is still upwards: The total number of new vulnerabilities reported in 2011 stood at 4,989. This figure works out to approximately 95 new vulnerabilities a week. Compared with the number from 2010 which was 6,253, it represents a decrease of 20% from that of 2010. While this may seem like positive news, it must be viewed in the context of a longer time window. When we look at the trend over the longer term, we can see that the overall pattern is still on an upward trajectory. So far, the number of vulnerabilities reported in January 2012, amounts to 488 and is already well ahead of the numbers reported in the same month last year.
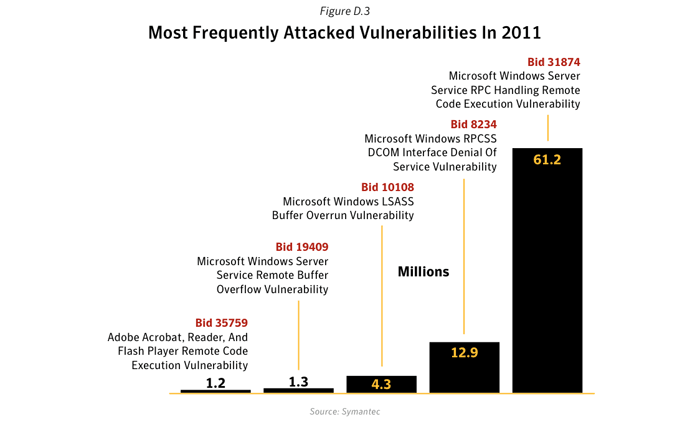
- The most often exploited vulnerabilities are not the newest: From observation of in-field telemetry, we can see that the most frequently used vulnerability in attacks is not the newest. Our data show that the most commonly attacked component by a wide margin is the Microsoft Windows RPC component. The attacks against this component are mostly using the Microsoft Windows Server Service RPC Handling Remote Code Execution Vulnerability (BID 31874 ). This vulnerability was first reported back in October 2008 and Symantec blocked 61.2 million attempts to exploit it in 2011. This figure represents 4.7 times the volume of the second most exploited vulnerability, the Microsoft Windows RPCSS DCOM Interface Denial of Service Vulnerability (BID 8234 ), from July 2003.
- The next two most often used vulnerabilities are the Microsoft Windows LSASS Buffer Overrun Vulnerability (BID 10108 4), dating from April 2004 and the Microsoft Windows Server Service Remote Buffer Overflow Vulnerability (BID 194095 ), from August 2008.
- Finally the fifth most exploited vulnerability is the Adobe Acrobat, Reader, and Flash Player Remote Code Execution Vulnerability (BID 357596 ), reported in July 2009.
- All of the top five vulnerabilities are several years old with
patches available: So why are they used so often even several years
after patches are available? There could be several reasons why this is
the case:
- Trading of vulnerabilities7 either through legitimate or clandestine channels has given exploitable vulnerabilities a significant monetary value. Because of the restricted information available on some of these new vulnerabilities, criminals may not be able to take advantage of them unless they are willing to pay the often substantial asking prices. If they are unable or unwilling to pay, they may resort to existing, widely available, tried and tested vulnerabilities to achieve their goals, even if it may potentially be less effective.
- For those willing to pay, they will want to ensure maximum return on their investment. This could mean they will use it discretely and selectively rather than making a big splash and arousing the attention of security vendors and other criminal groups looking for new vulnerabilities to use.
- Older vulnerabilities have a more established malware user base and so account for a greater amount of traffic. For example, widespread and well-established malware threats, such as W32.Downadup8 and its variants, use the Microsoft Windows Server Service RPC Handling Remote Code Execution Vulnerability (BID 31874), which continues to register over 200,000 hits each day. Because these threats use vulnerabilities to spread in an automated fashion, the number of attacks they can launch would generally be far higher than for targeted attacks.
- For various reasons, not all of the user population apply security patches quickly or at all. This means older vulnerabilities can often still be effective, even years after patches are available. Because of this, there will always a window of opportunity for criminals to exploit and they are all too aware of this.
- File based vulnerabilities: The most commonly exploited data file format is the PDF file format. One of the PDF related vulnerabilities, Adobe Acrobat, Reader, and Flash Player Remote Code Execution Vulnerability (BID 357599 ) registered as the fifth most often used vulnerability in 2011 with just over 1 million attacks reported. PDF files containing vulnerabilities are often associated with Advanced Persistent Threat (APT10 ) style attacks, rather than self-replicating malware. However, in this particular case, the vulnerability in question was most often used in Web toolkit based attacks. This attack scenario involves creating malicious websites to host exploit code. Users may then be tricked into visiting these malicious toolkit websites either by website redirection (e.g. malicious IFRAMEs), SEO poisoning or by sending out spam emails, instant messages or social media updates with links to the malicious website.
- One thing to note, websites hosting malicious toolkits often contain multiple exploits that can be tried against the visitor. In some cases, the kit will attempt to use all exploits at its disposal in a non-intelligent fashion whereas in more modern advanced kits, the website code will attempt to fingerprint the software installed on the computer before deciding which exploit(s) to send to maximise the success rate. The fact that there are so many Web kit based exploit attempts made using this old vulnerability may suggest that a considerable number of users have not updated their PDF readers to a non-vulnerable version.
2 See http://www.securityfocus.com/bid/31874
3 See http://www.securityfocus.com/bid/8234
4 See http://www.securityfocus.com/bid/10108
5 See http://www.securityfocus.com/bid/19409
6 See http://www.securityfocus.com/bid/35759
8 See http://www.symantec.com/security_response/writeup.jsp?docid=2008-112203-2408-99
9 See http://www.securityfocus.com/bid/35759
10 See http://go.symantec.com/apt
Zero-Day Vulnerabilities
Background
Zero-day vulnerabilities are vulnerabilities against which no vendor has released a patch. The absence of a patch for a zero-day vulnerability presents a threat to organizations and consumers alike, because in many cases these threats can evade purely signature-based detection until a patch is released. The unexpected nature of zero-day threats is a serious concern, especially because they may be used in targeted attacks and in the propagation of malicious code.Methodology
Zero-day vulnerabilities are a sub-set of the total number of vulnerabilities documented over the reporting period. A zero-day vulnerability is one that appears to have been exploited in the wild prior to being publicly known. It may not have been known to the affected vendor prior to exploitation and, at the time of the exploit activity, the vendor had not released a patch. The data for this section consists of the vulnerabilities that Symantec has identified that meet the above criteria.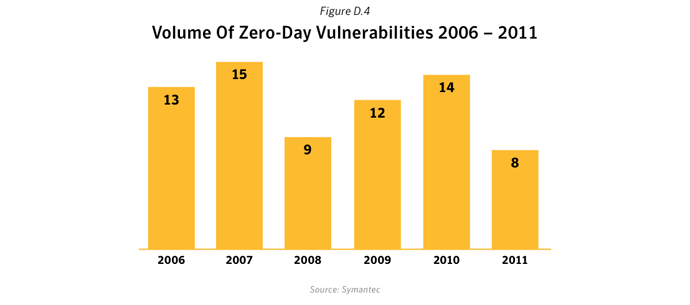
Commentary
2011 produced the lowest number of zero-day vulnerabilities in the past 6 years. There was a 43% drop in vulnerabilities seen in 2011 compared with 2010. However the number of vulnerabilities seen in 2010 was somewhat inflated due to W32.Stuxnet, which itself contributed to four11 of the zero-day vulnerabilities seen in that year.Notable Zero-day Attacks
RSA
A number of high-profile attacks in 2012 utilized zero-day vulnerabilities. In March RSA revealed that they were the victim of a targeted attack in which data related to their SecurID™ product was stolen13. This stolen data was then used in further attacks against a number of military contractors. In order to gain access to the RSA network the attackers first sent a crafted email message to a number of employees with the subject line “2011 Recruitment Plan”. The message contained an attachment called 2011 Recruitment Plan.xls, as shown in figure D.6.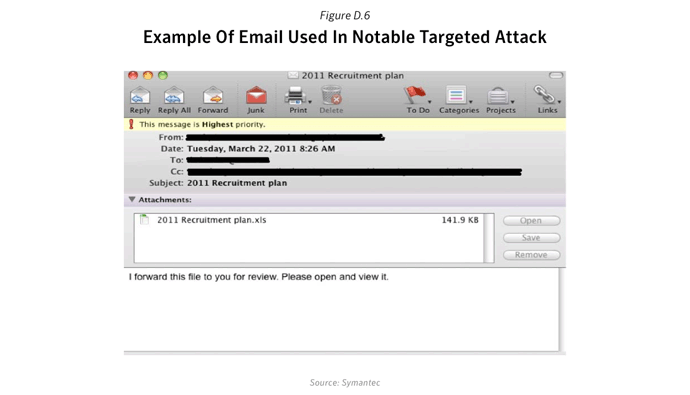
W32.Duqu
W32.Duqu was discovered in September 2012 was determined to have been based on the same source code as W32.Stuxnet. W32.Duqu is designed to capture and exfiltrate data which may be used to enable a future Stuxnet-like attack.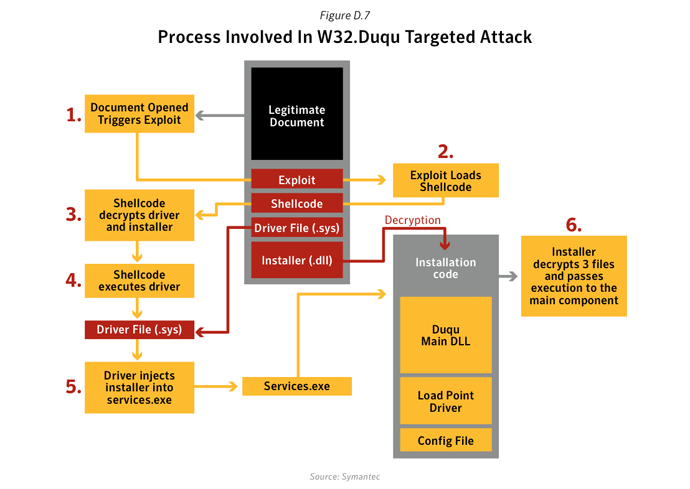
The Sykipot Attacks
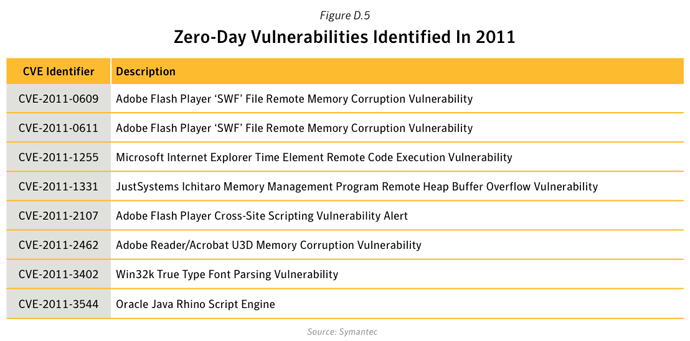
The Sykipot threat has been in existence since 2006 but gained attention in December 2012 due to a series of targeted attacks in which it exploited CVE-2011-2462 - Adobe Reader/Acrobat U3D Memory Corruption Vulnerability, a zero-day vulnerability. This wasn’t the first time that the Sykipot attackers used a zero-day vulnerability. In March 2010 the same attackers used an Internet Explorer zero-day to download and install Backdoor.Sykipot - CVE-2010-0806, Microsoft Internet Explorer 'iepeers.dll' Remote Code Execution Vulnerability.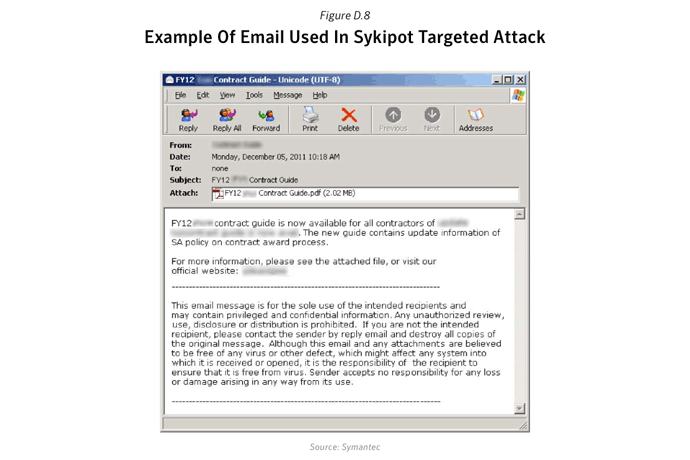
- Defense contractors
- Telecommunications
- Computer Hardware
- Chemical
- Energy
- Government Departments
- When the PDF attachment is launched it exploits CVE-2011-2462 in order to install the Backdoor program, Backdoor.Sykipot. Backdoor.Sykipot can then receive a variety of commands from the attackers, ultimately leading to the exfiltration of sensitive documents.
Window of Exposure for Zero-day Vulnerabilities
The window of exposure for vulnerabilities is the difference in days between the time when exploit code affecting a vulnerability is made public and the time when the affected vendor makes a patch publicly available for that vulnerability. During this time, the computer or system on which the affected application is deployed may be susceptible to attack. Attackers will attempt to maximize the window of exposure by making swift use of exploits in attacks.Commentary
An example of attackers taking advantage of the window of exposure is the usage of CVE-2011-2462 Adobe Acrobat and Reader U3D Memory Corruption Vulnerability. This vulnerability was used in targeted attacks in the wild on December 1st 2011. An advisory was published by the vendor on December 6th 201114 confirming that the vulnerability was being exploited in attacks against Adobe Reader 9.x. Version 10.x was also vulnerable but was not being exploited in the wild. On December 16 Adobe Reader and Acrobat version 9.4.7 was released to correct this vulnerability for versions 9.x. Version 10.2 was released on January 10th 2012 to correct version 10.1.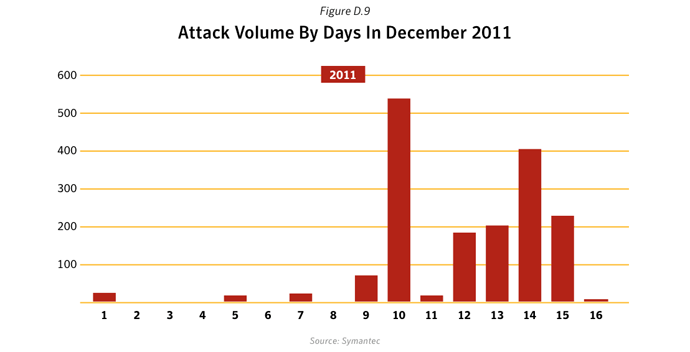
Web Browser Vulnerabilities
Background
Web browsers are nowadays ever-present components for computing for both enterprise and individual users on desktop and on mobile devices. Web browser vulnerabilities are a serious security concern due to their role in online fraud and in the propagation of malicious code, spyware, and adware. In addition, Web browsers are exposed to a greater amount of potentially untrusted or hostile content than most other applications and are particularly targeted by multi-exploit attack kits.Methodology
Browser vulnerabilities are a sub-set of the total number of vulnerabilities cataloged by Symantec throughout the year. To determine the number of vulnerabilities affecting browsers, Symantec considers all vulnerabilities that have been publicly reported, regardless of whether they have been confirmed by the vendor. While vendors do confirm the majority of browser vulnerabilities that are published, not all vulnerabilities may have been confirmed at the time of writing. Vulnerabilities that are not confirmed by a vendor may still pose a threat to browser users and are therefore included in this study.Data
This metric examines the total number of vulnerabilities affecting the following Web browsers:- Apple Safari
- Google Chrome
- Microsoft Internet Explorer
- Mozilla Firefox
- Opera
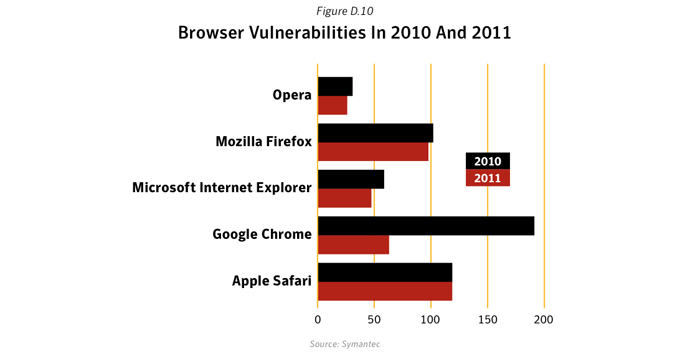
Commentary
- Chrome vulnerabilities dropped off dramatically in 2011. After a spike in 2010 (191), the documented vulnerabilities for Chrome browser dropped to 62 for 2011, which is a similar level as in previous years. A reason for the 2010 spike might have been the introduced bug bounty program and the rapid development of the browser in 2010.
- For Firefox, Internet Explorer, Safari and Opera the number of reported vulnerabilities decreased marginally in 2011.
- These five browsers combined had 351 reported vulnerabilities in total in 2011, which is a strong decrease from 500 in 2010. This decline can be attributed to the decrease of Chrome browser vulnerabilities. However, a decline in the number of reported vulnerabilities does not necessarily imply that risk levels have diminished; many Web-based attack kits will continue to exploit existing vulnerabilities and rapidly incorporate exploits for new vulnerabilities.
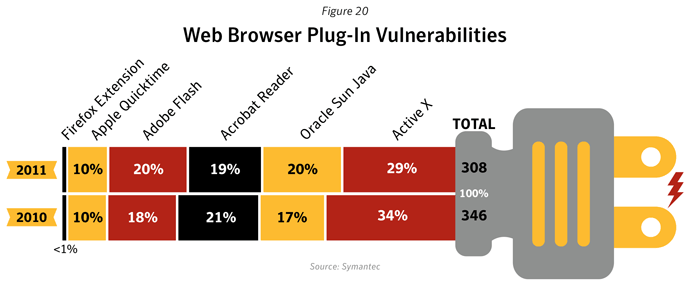
Web Browser Plug-in Vulnerabilities
Background
This metric examines the number of vulnerabilities affecting plug-ins for Web browsers. Browser plug-ins are technologies that run inside the Web browser and extend its features, such as allowing additional multimedia content from Web pages to be rendered. Although this is often run inside the browser, some vendors have started to use sandbox containers to execute plug-ins in order to limit the potential harm of vulnerabilities.Methodology
Web browser plug-in vulnerabilities comprise a sub-set of the total number of vulnerabilities cataloged by Symantec over the reporting period. The vulnerabilities in this section cover the entire range of possible severity ratings and include vulnerabilities that are both unconfirmed and confirmed by the vendor of the affected product. Confirmed vulnerabilities consist of security issues that the vendor has publicly acknowledged, by either releasing an advisory or otherwise making a public statement to concur that the vulnerability exists. Unconfirmed vulnerabilities are vulnerabilities that are reported by third parties, usually security researchers, which have not been publicly confirmed by the vendor. That a vulnerability is unconfirmed does not mean that the vulnerability report is not legitimate, only that the vendor has not released a public statement to confirm the existence of the vulnerability.Data
Symantec analyzed the following plug-in technologies:- Adobe Reader
- Adobe Flash Player
- Apple QuickTime
- Microsoft ActiveX
- Mozilla Firefox extensions
- Oracle Sun Java Platform Standard Edition (Java SE)
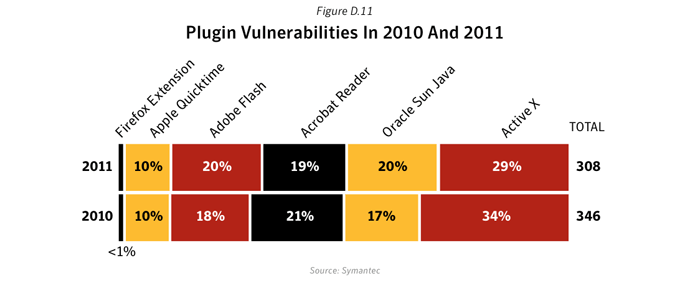
Commentary
- In 2011, 308 vulnerabilities affecting browser plug-ins were documented by Symantec, a slight decrease, compared to 346 vulnerabilities affecting browser plug-ins in 2010.
- ActiveX vulnerabilities decreased further in 2011, continuing the trend for the recent years. This may be due to the increased usage of Internet Explorer 8 which has an enhanced security features surrounding ActiveX plug-ins15 .
- Adobe Flash and Java vulnerabilities increased both by 3 percent in 2011. This trend was already visible in 2010 and grew again. This is also reflected in the vulnerability usage in attack toolkits which have focused around Adobe Flash, Adobe PDF Reader and Java in 2011.
Web Attack Toolkits
SCADA Vulnerabilities
Background
This metric will examine the SCADA (Supervisory Control and Data Acquisition) security threat landscape. SCADA represents a wide range of protocols and technologies for monitoring and managing equipment and machinery in various sectors of critical infrastructure and industry. This includes—but is not limited to—power generation, manufacturing, oil and gas, water treatment, and waste management. Therefore, the security of SCADA technologies and protocols is a concern related to national security because the disruption of related services can result in the failure of infrastructure and potential loss of life—among other consequences.Methodology
This discussion is based on data surrounding publicly known vulnerabilities affecting SCADA technologies. The purpose of the metric is to provide insight into the state of security research in relation to SCADA systems. To a lesser degree, this may provide insight into the overall state of SCADA security. Vulnerabilities affecting SCADA systems may present a threat to critical infrastructure that relies on these systems. Due to the potential for disruption of critical services, these vulnerabilities may be associated with politically motivated or state-sponsored attacks. This is a concern for governments and/or enterprises that are involved in the critical infrastructure sector. While this metric provides insight into public SCADA vulnerability disclosures, due to the sensitive nature of vulnerabilities affecting critical infrastructure there is likely private security research conducted by SCADA technology and security vendors. Symantec does not have insight into any private research because the results of such research are not publicly disclosed.Data
The number of SCADA vulnerabilities rose dramatically in 2011: In 2011, there were 129 public SCADA vulnerabilities, a massive increase over the 15 vulnerabilities in 2010.Commentary
The security of SCADA systems has always been an area of concern, but prior to 2010 it was on a more theoretical level. Since the emergence of W32.Stuxnet in 2010 there has been an increased focus on the security of SCADA systems. The security of these systems also gained attention in November 2011 when reports emerged of 2 separate alleged breaches. On November 10, 2011 the Illinois Statewide Terrorism & Intelligence Center (STIC) issued a report stating that the SCADA system at an Illinois water systems had been breached and that resulting action has caused a water pump to burn out. ICS-CERT later issued a report stating that there was no evidence to support these claims16 . On November 18th a hacker who goes by the name pr0f posted a statement to pastebin17 in which he claimed to have accessed the SCADA system used to manage water and sewage systems in South Houston, Texas.Malicious Code Trends
- Backdoors allow an attacker to remotely access compromised computers.
- Viruses propagate by infecting existing files on affected computers with malicious code.
- Worms are malicious code threats that can replicate on infected computers or in a manner that facilitates them being copied to another computer (such as via USB storage devices).
- Trojans are malicious code that users unwittingly install onto their computers, most commonly through either opening email attachments or downloading from the Internet. Trojans are often downloaded and installed by other malicious code as well. Trojan horse programs differ from worms and viruses in that they do not propagate themselves.
Top Malicious Code Families
Background
Symantec analyzes new and existing malicious code families to determine which threats types and attack vectors are being employed in the most prevalent threats. This information also allows system administrators and users to gain familiarity with threats that attackers may favor in their exploits. Insight into emerging threat development trends can help them to bolster security measures and mitigate future attacks.Methodology
A malicious code family is initially compromised up of a distinct malicious code sample. As variants to the sample are released, the family can grow to include multiple variants. Symantec determines the most prevalent malicious code families by collating and analyzing anonymous telemetry data gathered for the reporting period. Over the course of 2011, such products reported 1.8 billion such malicious code detections, compared with 1.5 billion in 2010. This figure includes malicious code detections identified in Symantec endpoint technology, including Norton as well as the Symantec.cloud security services for email and Web.Data
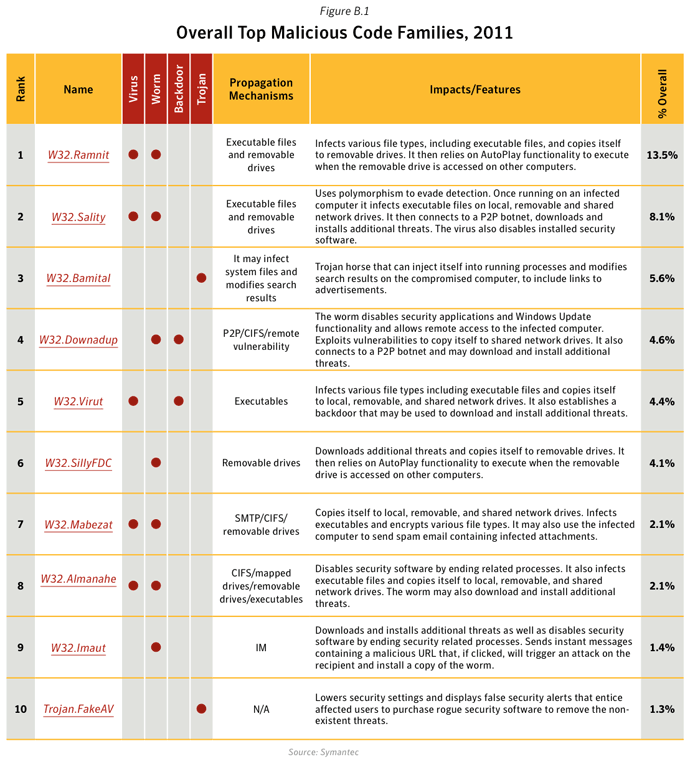
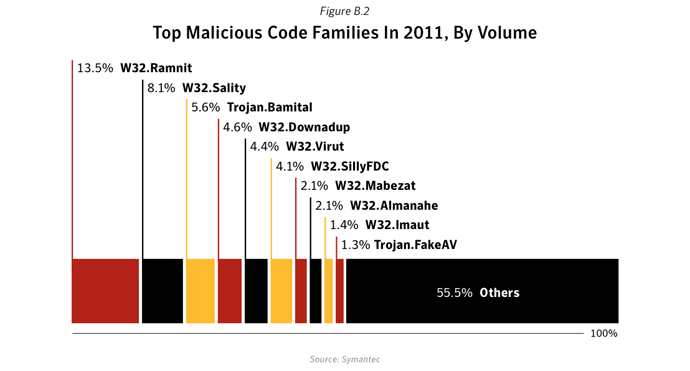
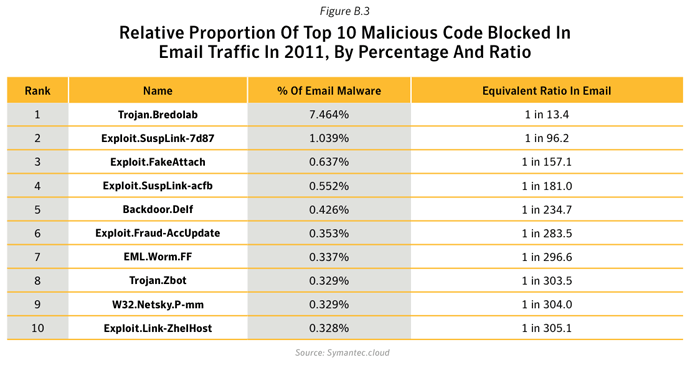
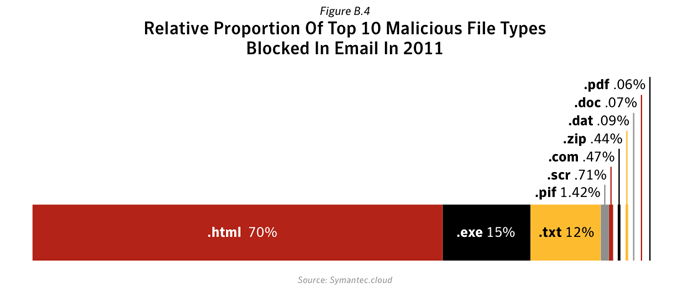
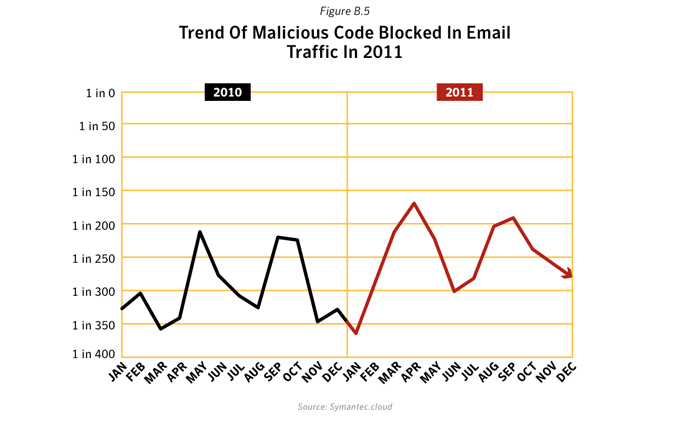
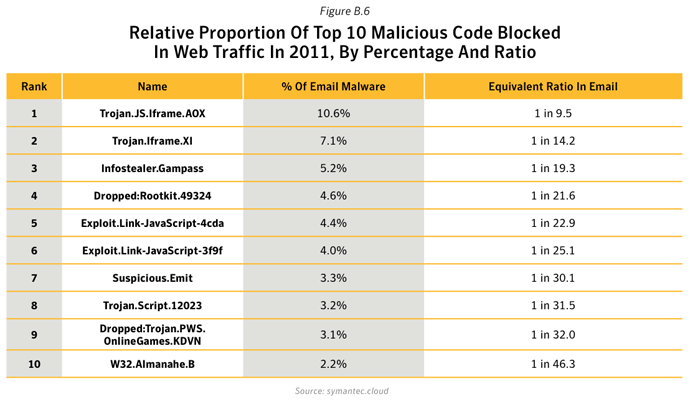
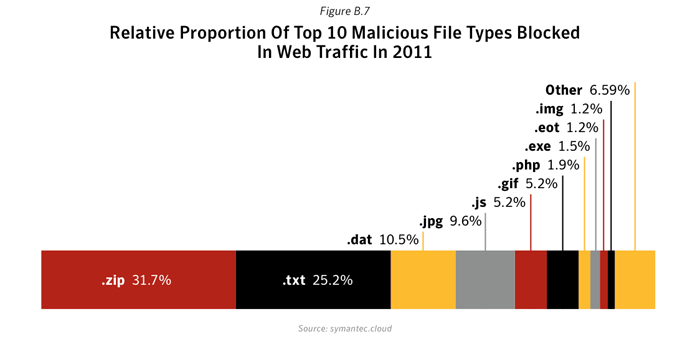
Commentary
- Ramnit overtakes Sality to become the most prevalent malicious code family in 2011. Ranked sixth in 2010, the top malicious code family by volume of potential infections in 2011 was Ramnit.
- Samples of the Ramnit family of malware were responsible for significantly more potential infections than the second ranked malicious code family in 2011, Sality. This is primarily the result of activity by W32.Ramnit!html, which accounts for 51% of all Ramnit malware blocked in 2011.
- W32.Ramnit!html is a generic detection for .html files infected by W32.Ramnit.
- First discovered in 2010, W32.Ramnit!html has been a prominent feature of the threat landscape since then, often switching places with Sality throughout the year as the two families jockey for first position.
- Ramnit spreads by encrypting and then appending itself to DLL, EXE and HTML files. It can also spread by copying itself to the recycle bin on removable drives and creating an AUTORUN.INF file so that the malware is potentially automatically executed on other computers. This can occur when an infected USB device is attached to a computer. The reliable simplicity of spreading via USB devices and other media makes malicious code families such as Ramnit, Sality (as well as SillyFDC and others) effective vehicles for installing additional malicious code on computers.
- The Sality family of malware, ranked second, remains attractive to attackers because it uses polymorphic code that can hamper detection. Sality is also capable of disabling security services on affected computers. These two factors may lead to a higher rate of successful installations for attackers. Sality propagates by infecting executable files and copying itself to removable drives such as USB devices. Similar to Ramnit, Sality also relies on AUTORUN.INF functionality to potentially execute when those drives are accessed.
- Downadup is losing momentum: Downadup (a.k.a. Conficker) was ranked in fourth position in 2011, compared with 2010 when it was ranked second-most malicious code family by volume of potential infections in 2010. Downadup propagates by exploiting vulnerabilities in order to copy itself to network shares. Downadup was estimated still to be on more than 3 million PCs worldwide at the end of 20111 , compared with approximately 5 million at the end of 2010.
- Overall in 2011, 1 in 238.8 emails was identified as malicious, compared with 1 in 284.3 in 2010; 39.1% of email-borne malware comprised hyperlinks that referenced malicious code, in contrast with malware that was contained in an attachment to the email. This figure was 23.7% in 2010, an indication that cyber criminals are attempting to circumvent security countermeasures by changing the vector of attacks from purely email to the Web.
- In 2011, 17.9% of malicious code detected in 2011 was identified and blocked using generic detection technology. Many new viruses and Trojans are based on earlier versions, where code has been copied or altered to create a new strain, or variant. Often these variants are created using toolkits and hundreds of thousands of variants can be created from the same piece of malware. This has become a popular tactic to evade signature-based detection, as each variant would traditionally need its own signature to be correctly identified and blocked. By deploying techniques, such as heuristic analysis and generic detection, it’s possible to correctly identify and block several variants of the same malware families, as well as identify new forms of malicious code that seek to exploit certain vulnerabilities that can be identified generically.
- Trojan.Bredolab was the most frequently blocked malware in email traffic by Symantec.cloud in 2011. This was owing to a rise in the number of strains of aggressively polymorphic malware, where variants of the Bredolab Trojan were contained in the payload of the email attachment.
- Trojan.Bredolab is an example of highly polymorphic malware; malicious code that is continually changed (by structure or content) to hide its presence from security countermeasures and in 2011, Symantec.cloud stopped Trojan.Bredolab in substantial volumes using Skeptic™ technology.
- Trojan.Bredolab frequently acts as a downloader or installer
for many secondary threats, including Trojan.Fakeavalert,
Backdoor.Rustock, Trojan.Srizbi, and W32.Waledac
The email would often use social engineering to encourage the recipient into opening it. Many such variants were also deployed by URL hyperlinks contained in some variations of the attacks using embedded links or attachments of the HTML file type.
- Attached HTML files were the most frequently blocked malicious email attachment in 2011.
- Web-based ZIP file format archives were the most frequently blocked malicious file type in 2011.
- Trojan.JS.Iframe.AOX was the most frequently blocked malicious activity in Web traffic filtered by Symantec.cloud in 2011. Detection for a malicious IFRAME is triggered in HTML files that contain hidden IFRAME elements with JavaScript code that attempts to perform malicious actions on the computer; for example, when visiting a malicious Web page, the code attempts to quietly direct the user to a malicious URL while the current page is loading.
- Stuxnet in 2011: Despite being developed for a very specific type of target, the number of reports of potential Stuxnet infections observed by Symantec in 2011 placed the worm at rank 18 among malicious code families, compared with 29 in 2010. The Stuxnet worm generated a significant amount of attention in 2010 because it was the first malicious code designed specifically to attack Programmable Logic Controller (PLC) industry control systems.2 Notably, Stuxnet was the first malicious code family that may directly affect the physical world and proves the feasibility for malicious code to cause potentially dramatic physical destruction.
- Duqu, the precursor to a new Stuxnet? In October 2011, Symantec received reports of a new threat (W32.Duqu3 ) that was created from the same code base as Stuxnet. Whilst the code base was near identical, and the methods around the attacks are similar, the purpose of the new threat appears to be completely different from Stuxnet. Where Stuxnet was primarily designed to sabotage industrial machinery, Duqu appears to be designed for information theft, particularly information related to industrial systems and other secrets. This activity could be carried out with a goal to use the stolen information to plan and mount future attacks of a similar nature to those made by Stuxnet.
Analysis of Malicious Code Activity by Geography, Industry Sector and Company Size
Background
Malicious code activity trends can also reveal patterns that may be associated with particular geographical locations, or hotspots. This may be a consequence of social and political changes in the region, such as increased broadband penetration and increased competition in the marketplace that can drive down prices, increasing adoption rates. Of course there may also be other factors at work, based on the local economic conditions that may present different risk factors. Similarly, the industry sector may also have an influence on an organization’s risk factor, where certain industries may be exposed to different levels of threat, by the nature of their business.Methodology
Analysis of malicious code activity based on geography, industry and size are based on the telemetry analysis from Symantec.cloud clients for of threats detected and blocked against those organizations in email traffic during 2011.Data
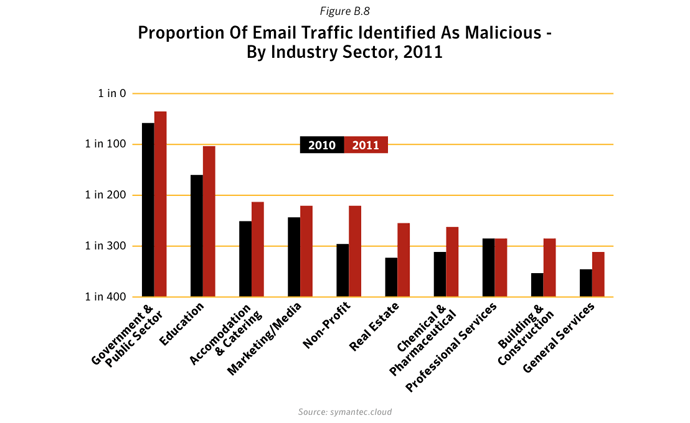
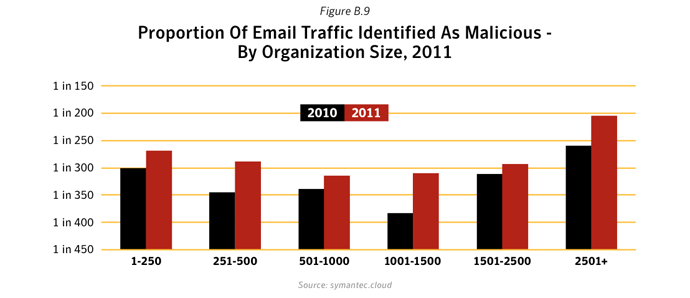
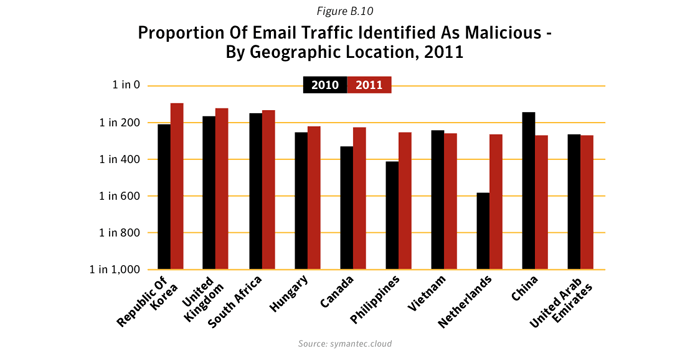
Commentary
- The rate of malicious attacks carried by email has increased for eight of the top-ten geographies being targeted; malicious email threats fell in 2011 for organizations in both Vietnam and China.
- Businesses in the Republic of Korea (South Korea) were subjected to the highest average ratio of malicious email-borne email in 2011, with 1 in 94.2 emails blocked as malicious, compared with 1 in 209.6 in 2010.
- Globally, organizations in the Government and Public sector were subjected to the highest level of malicious attacks in email traffic, with 1 in 41.1 emails blocked as malicious in 2011, compared with 1 in 65.7 for 2010.
- Malicious email threats have increased for all sizes of organizations, with 1 in 205.1 emails being blocked as malicious for large enterprises with more than 2,500 employees in 2011, compared with 1 in 259.7 in 2010.
- 1 in 267.9 emails were blocked as malicious for small to medium-sized businesses with between 1-250 employees in 2011, compared with 1 in 300.0 in 2010
Propagation Mechanisms
Background
Worms and viruses use various means to spread from one computer to another. These means are collectively referred to as propagation mechanisms. Propagation mechanisms can include a number of different vectors, such as instant messaging (IM), Simple Mail transfer protocol (SMTP), Common Internet File System (CIFS), peer-to-peer file transfers (P2P), and remotely exploitable vulnerabilities.4 Some malicious code may even use other malicious code as a propagation vector by locating a computer that has been compromised through a backdoor server and using it to upload and install itself.Methodology
This metric assesses the prominence of propagation mechanisms used by malicious code. To determine this, Symantec analyzes the malicious code samples that propagate and ranks associated propagation mechanisms according to the related volumes of potential infections observed during the reporting period. 5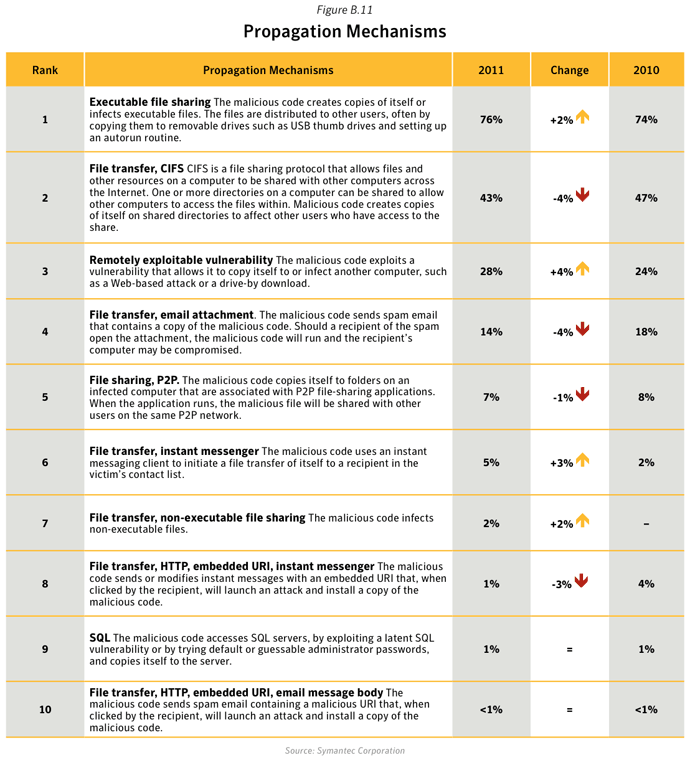
Commentary
As malicious code continues to become more sophisticated, many threats employ multiple mechanisms.- Executable file sharing activity increases: In 2011, 76 percent of malicious code propagated as executables, an increase from 74 percent in 2010. This propagation mechanism is typically employed by viruses and some worms to infect files on removable media. For example, variants of Ramnit and Sality use this mechanism, and both families of malware were significant contributing factors in this metric, as they were ranked as the two most common potential infections blocked in 2011.
- Remotely exploitable vulnerabilities increase: The percentage of malicious code that propagated through remotely exploitable vulnerabilities in 2011 at 28 percent was 4 percentage points higher than in 2010. Examples of attacks employing this mechanism also include Downadup, which although seems to be in decline, is still a major contributing factor to the threat landscape, ranked on fourth position in 2011.
- File transfer using CIFS is in decline: It is worth noting that despite an increase in between 2009 and 2010, the percentage of malicious code that propagated through CIFS file transfer fell by four percentage points between 2010 and 2011. Fewer attacks exploited CIFS as an infection vector in 2011.
- File transfer via email attachments continues to decline: It is worth noting the continued decline in the percentage of malicious code that propagated through email attachments for the fifth year running. Between 2010 and 2011, the proportion of malware using this mechanism fell by four percentage points.
- While this propagation mechanism is still effective, Symantec anticipates that this downward trend will continue into the near future. This is in part owing to a shift in malicious attacks through malicious URLs contained in emails rather than attachments, compared with 2010. In 2011, 39.1% of email attacks used malicious URLs, compared with 23.7% in 2010.
5 Because malicious code samples often use more than one mechanism to propagate, cumulative percentages may exceed 100 percent.
Industrial Espionage: Targeted Attacks and Advanced Persistent Threats (APTs)
Background
With targeted attacks and advanced persistent threats being very much in the news in 2011, in this section we review targeted attacks and look more closely at what has been described as “advanced persistent threats” or APTs for short. Terms such as APT have been overused and sometimes misused by the media, but APTs are a real threat to some companies and industries.Methodology
Defining what is meant by targeted attacks and APT is important in order to better understand the nature of this mounting threat and to make sure that you have invested in the right kinds of defenses for your organization.Data and Commentary
In 2010 Stuxnet and Hydraq grabbed headlines and gave clear demonstration to warnings the security community had raised for years; that malware could be used for cyber-terrorism, real world destruction and industrial espionage.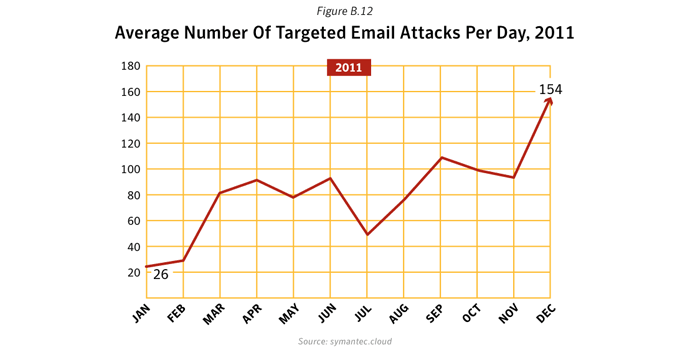
The Characteristics of a Targeted Attack
Defining a larger versus medium versus small company can be somewhat arbitrary. For the purposes of our research we have defined large companies as those having over 2,500 employees. Medium companies are between 250 and 500; and small as those companies with less than 250 employees. When comparing the number of targeted attacks directed at companies with 2,500 or more employees and companies with less than 2,500 we see an equal split.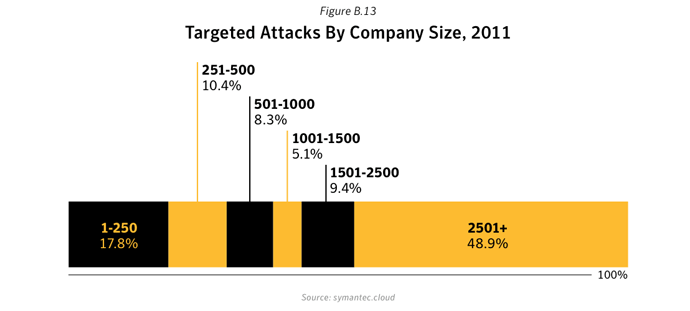
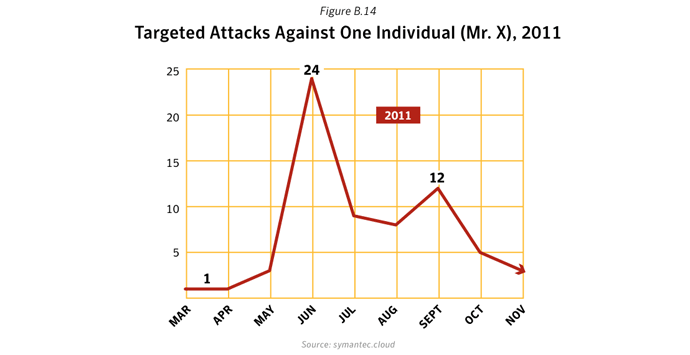
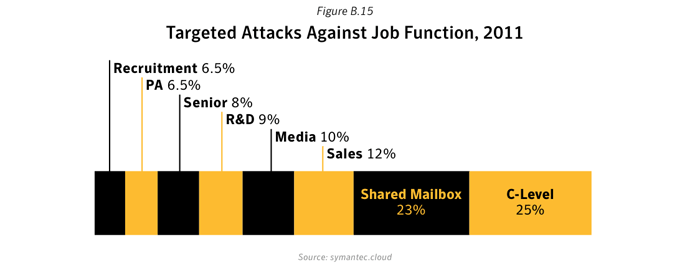
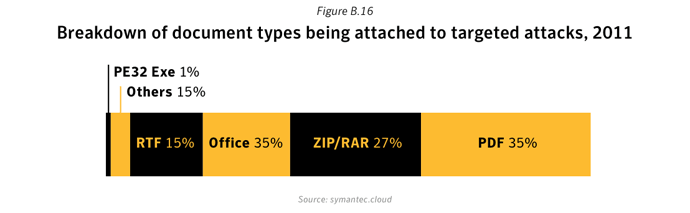
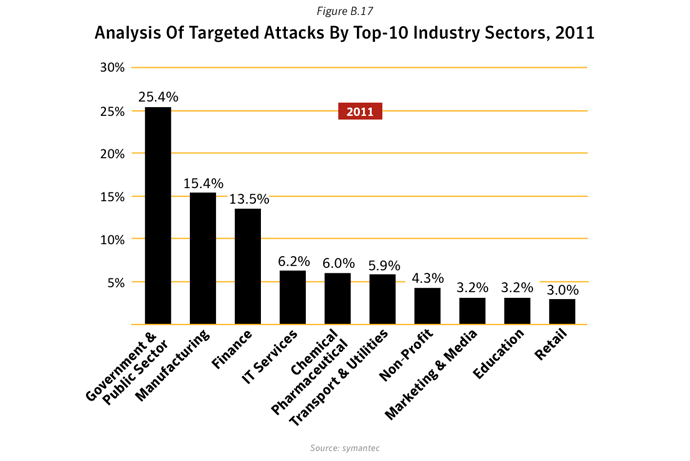
Case Study – MOTA campaign
NR4 is one mass-scale attack campaign out of 130 that the Symantec’s TRIAGE technology analyzed. (There is no significance to the name NR4). We do not know the ultimate goal of the attackers behind this campaign, but we do know that they targeted diplomatic and government organizations.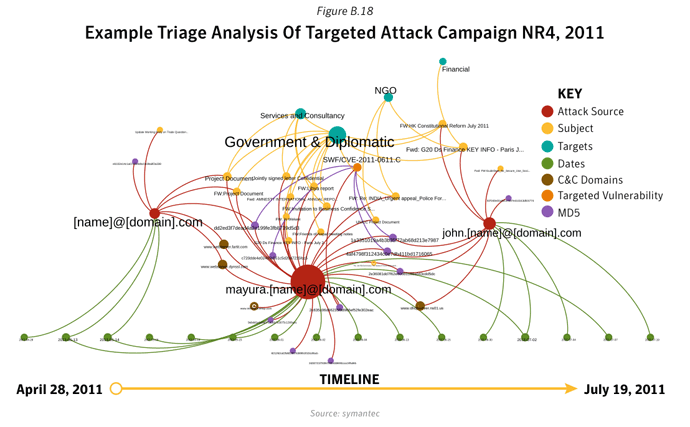
Conclusion
Targeted attacks should be concern for all organization, large and small. While C-level executives and those that work with a company’s IP should be careful, everyone in an organization is at risk of being targeted. This is especially true of workers who in the course of their jobs typically receive email from people they don’t know. In the end, no matter the size or type of organization you have or your role in that organization, you are at risk and best practices must be followed to protect the organization. Don’t become the weakest link in the supply chain.TRIAGE Analysis of Targeted Attacks
Background
Symantec’s advanced TRIAGE data analytics technology aims at answering some fundamental questions about targeted attacks, such as:- Attribution: Can we link series of similar attacks, perhaps targeting different organizations - on the same or different dates - to larger-scale campaigns likely organized by the same group of individuals?
- How many different groups of attackers can we identify based on their modus operandi?
- What are the characteristics and dynamics of such attack campaigns? Can we observe multiple connections among those attacks, for example regarding the subjects used the malicious attachments, the targeted recipients or the date of the attack?
Methodology
To identify series of targeted attacks that are likely performed by the same individuals, we have used a novel attack attribution named TRIAGE. Developed by Symantec in the context of the European funded WOMBAT research project (http://www.wombat-project.eu/), TRIAGE is a novel attack attribution method based on a multi-criteria decision algorithm. This new attribution method has been implemented in an analytical software framework that is now being maintained in the context of VIS-SENSE, a European research project that aims at improving security analysis with novel Visual Analytics technologies.Data and Commentary
Insights into targeted attack campaignsSymantec’s TRIAGE technology has identified 130 clusters of attacks, which are quite likely reflecting different campaigns organized by the same groups of individuals. Indeed, within the same cluster, all attacks are linked by at least 3 or 4 characteristics among the following ones:
- The origins of the attack (Email ‘From’ address or IP address used by the attacker).
- The attack date.
- The characteristics of the malicious file attached to the email (MD5 checksum, AV signature and file name).
- The email subject.
- The targeted recipient (‘To:’ or ‘Bcc:’ address fields in the email).

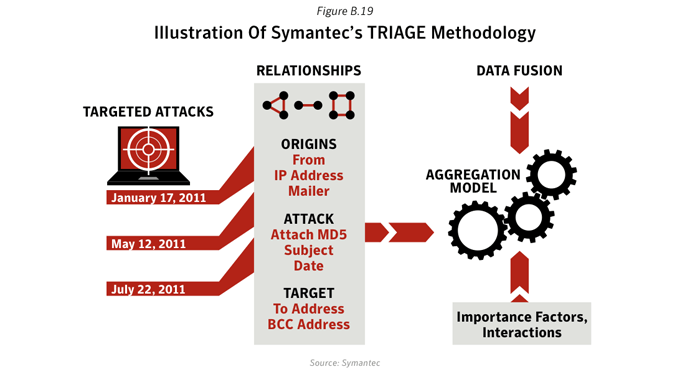
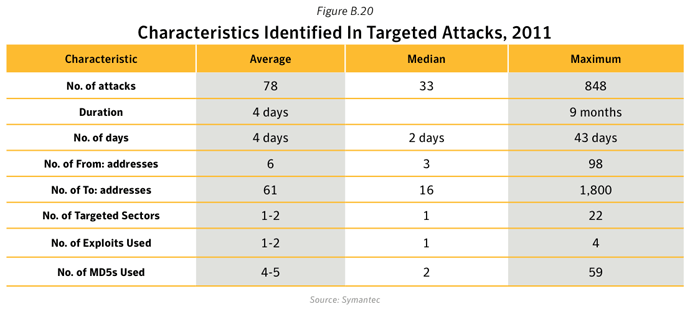
- Type 1 - Single-sector: highly focused attack campaigns targeting one (1.a) or several (1.b) organizations within the same activity Sector;
- Type 2 - Multi-sector: larger-scale campaigns that usually target a large number of organizations across multiple sectors. This type of attacks fit the profile of Massive Organizationally Targeted Attack (MOTA).
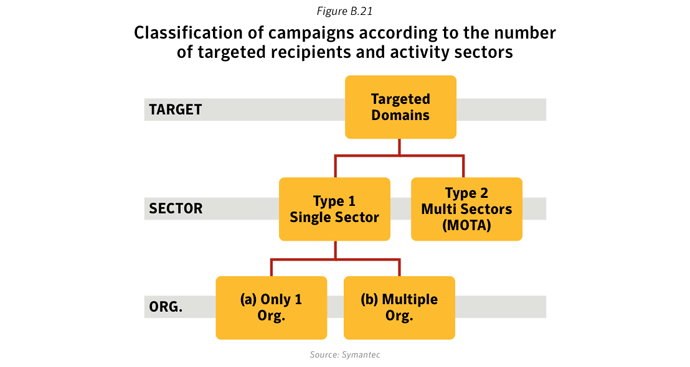
Type 1 – Highly targeted campaigns: Sykipot attacks
Two-thirds of attack campaigns identified by Symantec were targeting either a single, or a very limited number of organizations active in the same sector. Over 50% of those single-sector campaigns target the Government and Defense sectors. However, other industries clearly are experiencing such highly targeted attacks. Symantec research shows that “niche” sectors are usually more targeted by highly focused attacks. Industries active in sectors like Agriculture, Construction, Oil and Energy mainly see attacks that are highly targeted at a small number of companies and individuals within them.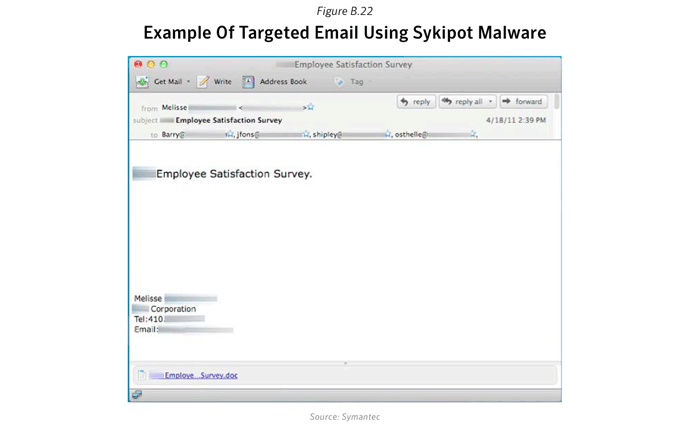
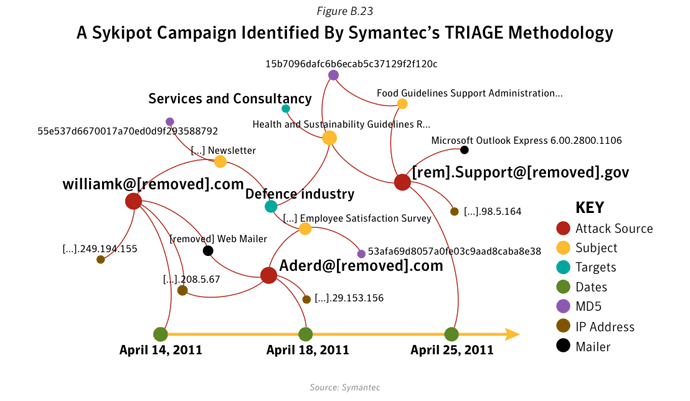
Type 2 – Massive Organizational Targeted Attacks (MOTA): Nitro and Taidoor attacks
One third of attack campaigns were organized on a large-scale and fit the profile of a Massive Organizationally Targeted Attack (MOTA): they target multiple people in multiple organizations, in different sectors, over multiple days. Most of these large-scale campaigns are very well resourced, with up to 4 different exploits used during the same campaign. Some are even multilingual: the language used in the email attack is tuned to the targeted recipients.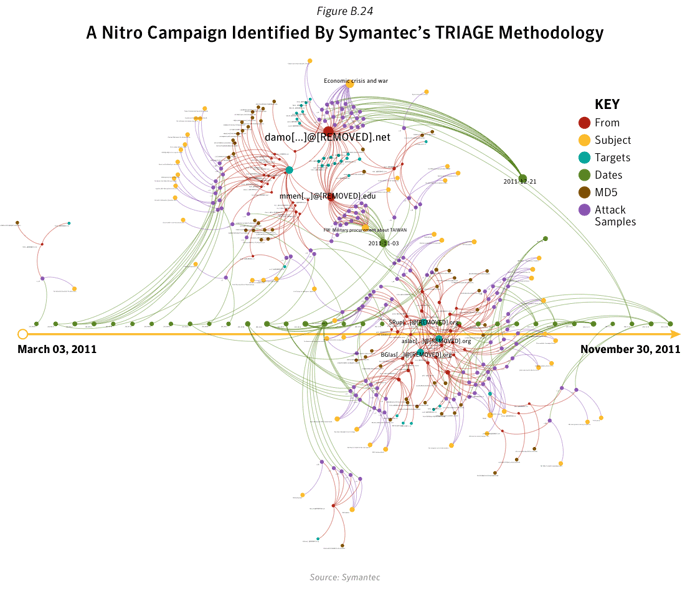
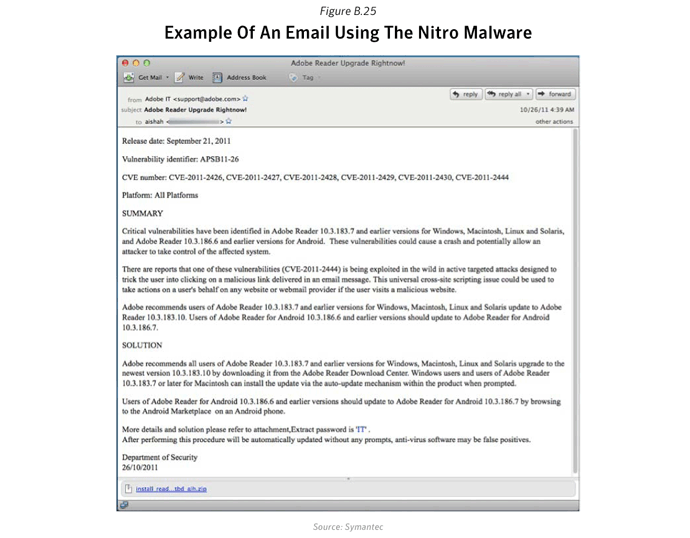
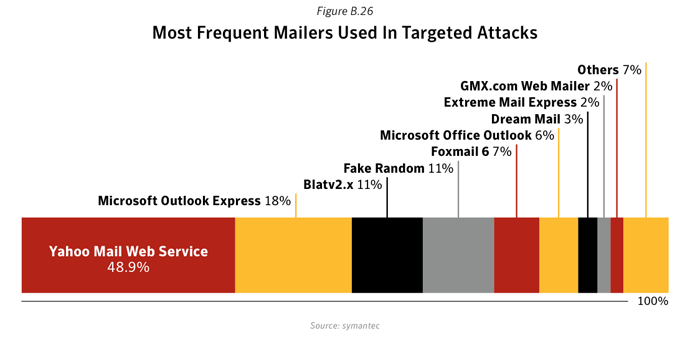
Spam and Fraud Activity Trends
- Analysis of Spam Activity Trends
- Analysis of Spam Activity by Geography
- Industry Sector and Company Size
- Analysis of Spam Delivered by Botnets
- Spam Botnets Analysis – A Strategic Viewpoint
- Significant Spam Tactics
- Spam by Language
- Spam by Category
- Future Spam Trends
- BGP Hijacking
- Phishing Activity Trends
- Analysis of Phishing Activity by Geography
Analysis of Spam Activity Trends
Background
This section discusses the patterns and trends relating to spam message volumes and the proportion of email traffic identified as spam during 2011.Methodology
The analysis for this section is based global spam and overall email volumes for 2011. Global values are determined based on the statistically representative sample provided by Symantec’s Brightmail2 operations and spam rates include spam blocked by Symantec.cloud.Data and Commentary
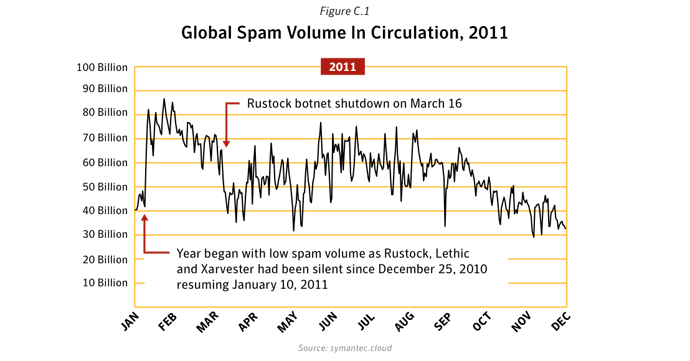
- There were approximately 41.1 billion spam emails in circulation worldwide each day overall in 2011, compared with 61.6 billion in 2010; a decrease of 31.8% in global spam volume.
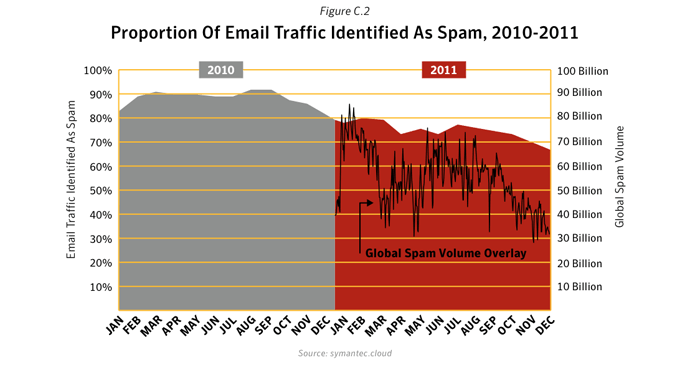
- Overall for 2011, 75.1% of email traffic was identified as spam, compared with 88.5% in 2010; a decrease of 13.4 percentage points.
Analysis of Spam Activity by Geography, Industry Sector and Company Size
Background
Spam activity trends can also reveal patterns that may be associated with particular geographical locations, or hotspots. This may be a consequence of social and political changes in the region, such as increased broadband penetration and increased competition in the marketplace that can drive down prices, increasing adoption rates. Of course there may also be other factors at work, based on the local economic conditions that may present different risk factors. Similarly, the industry sector may also have an influence on an organization’s risk factor, where certain industries may be exposed to different levels of threat, by the nature of their business.Methodology
Analysis of spam activity based on geography, industry and size is determined from the patterns of spam activity for Symantec.cloud clients for threats during 2011.Data
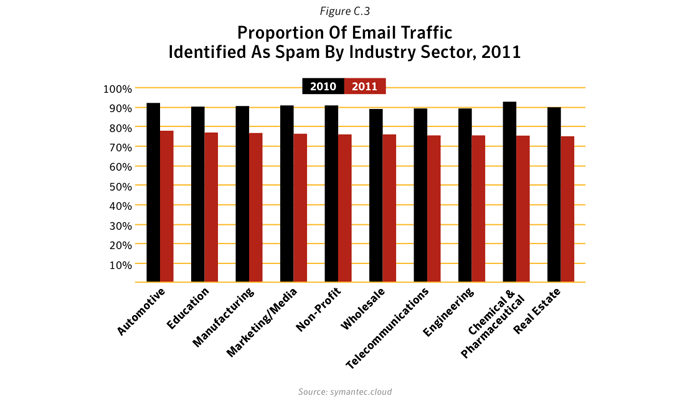
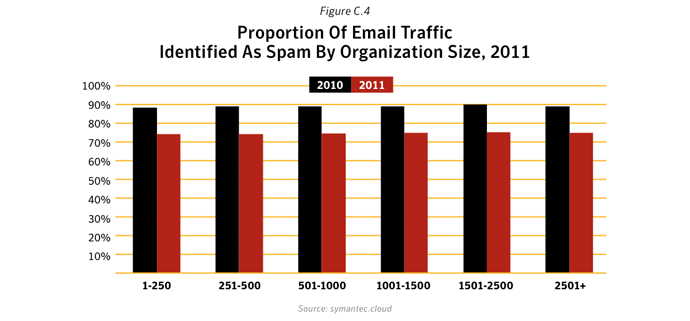
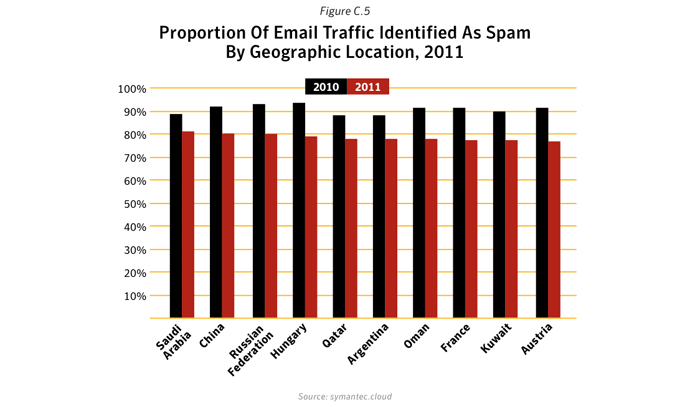
Commentary
- The spam rate has decreased across all top-ten geographies in 2011. The highest rate for spam is for organizations in Saudi Arabia, with an overall average spam rate of 80.9%. In 2010, the highest rate was in Italy, with an overall average spam rate of 93.5%.
- The spam rate has decreased across all top-ten industry sectors in 2011. Organizations in the automotive sector were subjected to the highest spam rate of 77.9% in 2011; in 2010, the engineering sector had the highest spam rate of 93.5%.
- The spam rate has decreased for all sizes of organization in 2011. 75.2% of emails sent to large enterprises with more than 2,500 employees in 2011 were identified as spam, compared with 90.1% in 2010.
- 74.6% of emails sent to small to medium-sized businesses with up to 250 employees in 2011 were identified as spam, compared with 89.7% in 2010.
Analysis of Spam Delivered by Botnets
Background
This section discusses botnets and their use in the sending of spam. Like ballistics analysis in the real world can reveal the gun used to fire a bullet, botnets can similarly be identified by common features within the structure of email headers and corresponding patterns during the SMTP3 transactions. Spam emails are classified for further analysis according to the originating botnet during the SMTP transaction phase. This analysis only reviews botnets involved in sending spam and does not look at botnets used for other purposes, such as for financial fraud or DDoS attacks.Methodology
Symantec.cloud spam honeypots collected between 5–10 million spam emails each day during 2011. These are classified according to a series of heuristic rules applied to the SMTP conversation and the email header information. Further information and examples of this analysis can be found later in this Appendix: “Spam Botnet Analysis – A Strategic Viewpoint.”Data
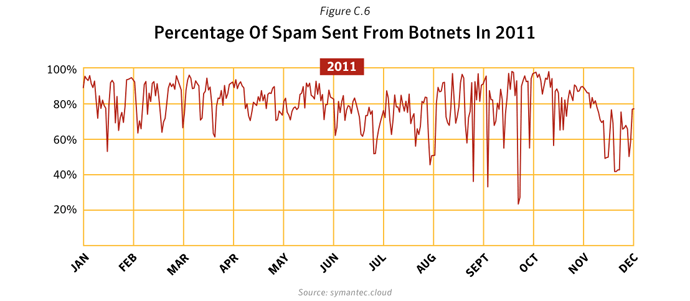
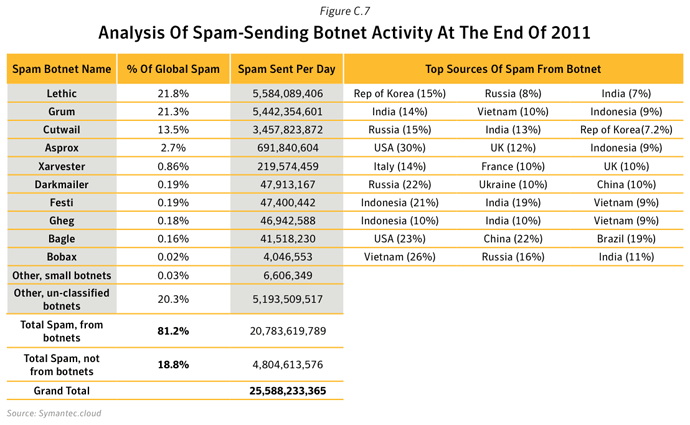
Commentary
- Over in 2011, approximately 78.8% of all spam was distributed by spam-sending botnets, compared with 88.2% in 2011, a decrease of 9.4 percentage points. This was in large part owing to the disruption of the Rustock botnet on 16 March 2011. By the end of 2011, this number rose to 81.2%.
- In the 7 days prior to the disruption of the Rustock botnet, each day approximately 51.2 billion spam emails were in circulation worldwide. In the 7 days following, this number fell to 31.7 billion, a decrease of 38.0% in global spam volume.
- The global spam rate during the 7 days prior to when the Rustock botnet ceasing spamming was 78.2%, compared with 70.0% in the 7 days after.
- During the second-half of 2011, the change in frequency of botnet spam being distributed from botnets became much more noticeable, as shown in figure C.6. Large spam runs often lasted for only two or three days and when the spam run ceased, the volume of botnet-spam fell considerably; however, when Rustock was in operation during 2010 and during the first quarter of 2011, it was almost continually sending spam at a fairly regular and steady rate.
Spam Botnet Analysis – A Strategic Viewpoint
Background
Most previous studies on spamming botnets have primarily focused on identifying botnet characteristics and signatures, but not on understanding the community behavior of spam botnets. In this analysis Symantec has looked at the global behavior of spam botnets by correlating their spam campaigns through multiple characteristics. The goal is to better understand the modus operandi of spammers controlling those botnets and how these are used for spam campaign operations.Methodology
Symantec used a three month-data set collected by our spam traps, comprising approximately 1 million spam messages. Twelve characteristics were extracted from the email headers and message bodies, which in turn were correlated to classify spam messages that were likely to have originated from the same spammer operation. These characteristics include attributes such as the character set used, the Subject: lines, the From: domains, the URIs appearing in the message bodies.Data and Commentary
Correlating interconnections between botnet spam campaigns
- Research shows that different botnets may perform very similar spam campaigns in the same period of time, and are strongly interconnected through several characteristics of spam messages.
- For example, Figure C.8 visualizes approximately 1,200 spam campaigns sent through Rustock, Grum, Cutwail and Mega-D. The small nodes in the center of the graph indicate bot host names that are shared among 2 or more botnets. Similar interconnections were obtained for other characteristics as well, such as the Subject: lines, From: domains, URLs, etc.
- The analysis hypothesized there were three possible explanations for these interconnections between different botnets:
- (i) Certain computers can be compromised by more than one bot and are used in parallel by different spammers to perform similar-looking spam campaigns;
- (ii) Spammers controlling those botnets are collaborating (e.g., load balancing various spam campaigns on two or more botnets); and
- (iii) Botnet signatures may sometimes fail to identify bots with 100% of accuracy.
- Figure C.9, below, shows another example of a spam campaign sent through Lethic and Maazben on 3 consecutive dates, and involving shared URLs, Subject: lines, character sets and host names. At the time of analysis, all URIs were redirecting to the same website, which was distributing fake pharmaceutical products. A number of From: domains used in this campaign were also shared by the two botnets, but not shown on the graph.
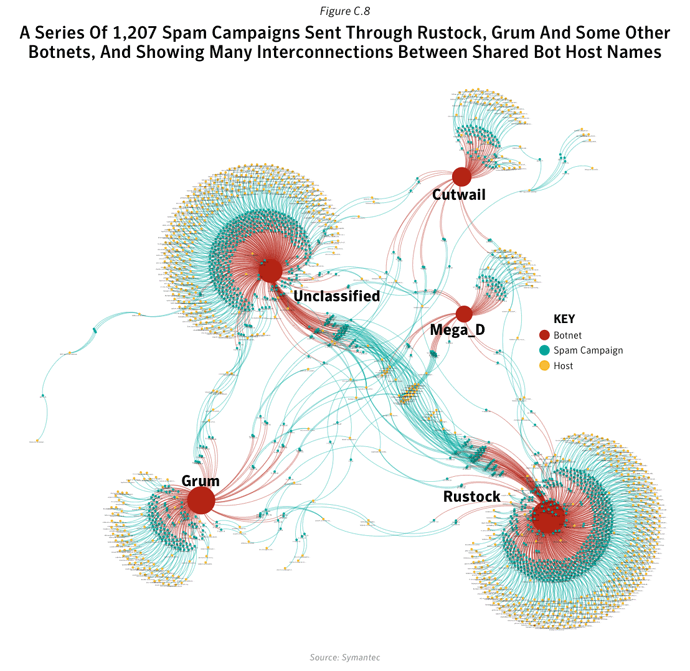
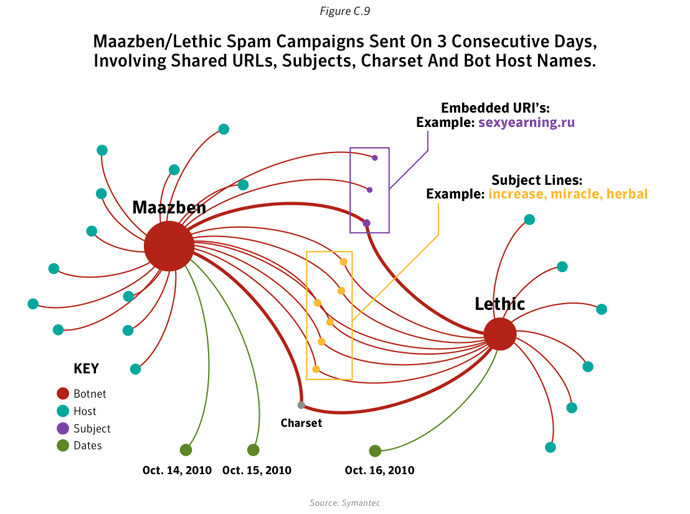
Dynamics of spam campaigns
- Symantec research has showed that spam campaigns sent through Rustock/Grum botnets are rather long-lived and stable, whereas campaigns distributed through Lethic and Maazben are instead short-lived (they last on average between 2 and 7 days), and have a more polymorphic behavior with respect to certain features, such as the frequent use of different disposable URLs and From: domains, which are being changed every day.
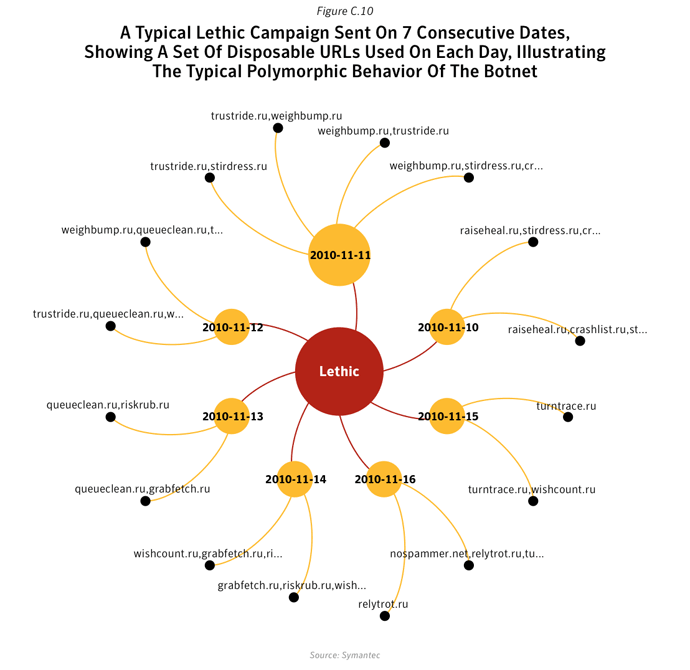
Impact of the Rustock take-down
- On March 16th -17th 2011, Rustock C&C servers located in the U.S. were seized by federal law enforcement agents, thanks to a coordinated anti-botnet action led by the security industry and U.S. federal authorities. As a result of this action (dubbed Operation b107), the botnet was almost completely shut down.
- Looking at global spam volumes, Bagle apparently stepped up to service the spammers. However, this relative increase in spam activity from Bagle was not a direct consequence of the Rustock takedown.
- Instead, our research shows that Grum has much more likely taken over (at least in part) Rustock activities. We found that the two botnets were strongly interconnected by a number of common elements, such as the Subject: lines, the From: domains used to send spam, the charset, and more importantly, the URIs embedded in the messages. Perhaps even more conclusively, those shared URIs were pointing to different domains registered by the same person (according to WHOIS data registry).
- All those interconnections between the two botnets lead us to think that part of Rustock activity was likely to have been offloaded to Grum shortly after its takedown.
Significant Spam Tactics
Background
This section discusses significant spam tactics used throughout 2010, including the size of spam messages and the languages used in spam emails.Size of Spam Messages
- In 2011, 61.0% of spam messages were between 2KB and 5KB in size. For spammers, smaller file sizes mean more messages can be sent using the same resources, typically botnets.
- Increased sizes are often associated with malicious activity, where email attachments contain malicious executable code.
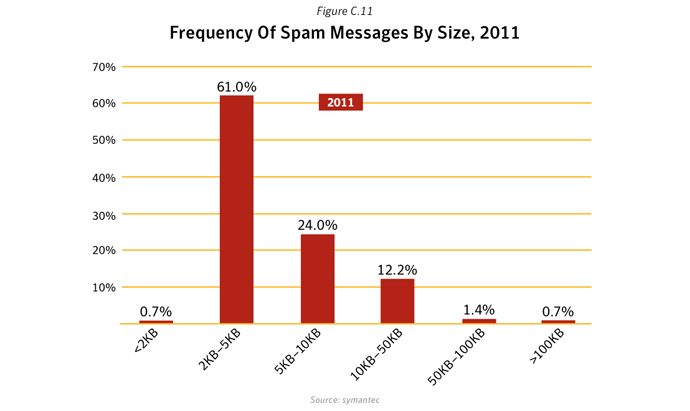
Proportion of Spam Messages Containing URLs
- In 2011, 86.2% of spam messages contained at least one URL hyperlink, compared with 91.1% in 2010, a decrease of 4.9 percentage points.
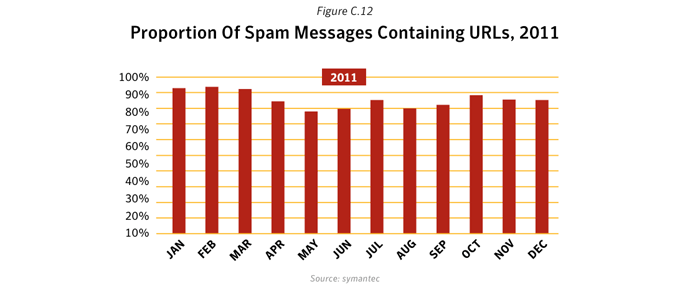
Top-Level Domains (TLD) Identified in Spam URLs
- In 2011, 58.5% of spam URLs was for domains registered in the .com TLD, that is to say, spam URLs that were registered in the .com top-level domain.
- The second most frequently used TLD was .ru, which is the top-level country code domain for Russian, and accounted for approximately 11.5% of all spam URL domains.
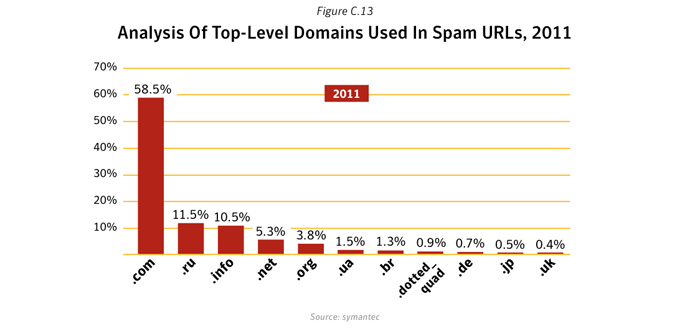
Spam by Language
Background and Methodology
The data for this section is based on the analysis of spam processed by the Symantec.cloud Skeptic4 technology. A series of checks are made against the language of the subjects and headers available from the Skeptic knowledgebase.Data
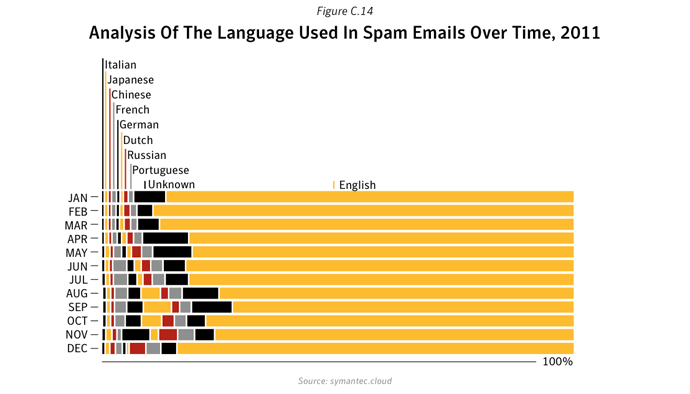
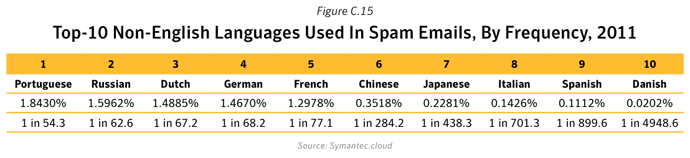
Commentary
- Spam in English still dominates, but has decreased over the year. At the end of 2010, 90% of spam detected was in English, falling to 88.7% by the end of 2011. This indicates a growth in non-English language spam as well as overall spam volumes diminishing over the same period.
- An email is classified as unknown when there is not enough recognizable text within the body of the email to be able to determine a language, typically because the body only contains a very small amount of HTML code, such as a hyperlink to a website or an image. The use of spam with only images or URLs fell in 2011. Of the percentage of non-English spam approximately half was classified as “unknown” at the end of 2010, falling to 26% by the end of 2011.
4http://www.symanteccloud.com/en/gb/globalthreats/learning_center/what_is_skeptic
Spam by Category
Background
Spam is created in a variety of different styles and complexities. Some spam is plain text with a URL; some is cluttered with images and/or attachments. Some comes with very little in terms of text, perhaps only a URL. And, of course, spam is distributed in a variety of different languages. It is also common for spam to contain “Bayes poison” (random text added to messages that has been haphazardly scraped from websites to “pollute” the spam with words bearing no relation to the intent of the spam message itself). Using Bayes poison is done to thwart spam filters that typically try to deduce spam based on a database of words that are frequently repeated in spam messages.Methodology
Once per month, several thousand random spam samples are collected and classified by Symantec.cloud into one of the following categories:- Casino/Gambling
- Degrees/Diplomas
- Diet/Weight Loss
- Jobs/Money Mules
- Malware
- Mobile Phones
- Pharmaceutical
- Phishing
- Scams/Fraud/419s
- Sexual/Dating
- Software
- Unknown/Other
- Unsolicited Newsletters
- Watches/Jewelry
Data
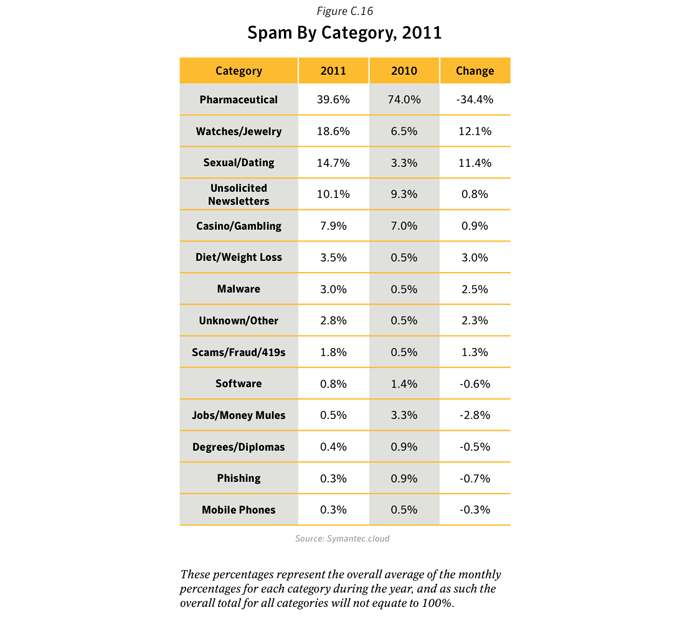
Commentary
- Pharmaceutical products still dominate, although to a lesser extent than in previous years. Approximately two fifths (39.6%) of all spam in 2011 was related to pharmaceutical products, a fall of 34.4 percentage points compared with 2011. This was in large part as a result of the disruption of the Rustock botnet. Pharmaceutical spam accounted for the majority of Rustock’s spam output.
- The disruption of the Rustock botnet in March 2011 had a major impact on the decline in pharmaceutical spam products, although other botnets have also been involved in distributing pharmaceutical spam in 2011, including Grum, Cutwail, and Donbot.
- A category with a low percentage still means millions of spam messages. Although it is difficult to be certain what the true volume of spam in circulation is at any given time, Symantec estimates that approximately 42.1 billion spam emails were sent globally each day in 2011. Where some of the categories listed earlier represent 0.5 percent of spam, this figure equates to more than 210 million spam emails in a single day.
- Spam related to Watches/Jewelry, Sexual/Dating, Casino/Gambling, Unsolicited Newsletters and Scams/Fraud all increased. Particularly notable is increase in the Sexual/Dating category, which rose by 12.1 percentage points since 2010. These are often email messages inviting the recipient to connect to the scammer through instant messaging, or a URL hyperlink where they are then typically invited to a pay-per-view adult-content Web cam site. Often any IM conversation would be handled by a bot responder, or a person working in a low-pay, offshore call center.
Future Spam Trends: BGP Hijacking
Case Study - Beware of “Fly-by Spammers”
Background
Routing between Autonomous Systems (AS) is achieved using the Border Gateway Protocol (BGP), which allows ASes to advertise to others the addresses of their network and receive the routes to reach the other ASes (figure C.17, below).Methodology
In order to study this phenomenon, a tool monitoring the routes towards spamming hosts based on traceroute has been developed by Symantec to determine whether spammers actually manipulate the Internet routing to launch spam campaigns.Data and Commentary
On August 20th, the network administrator of the Russian telecommunication company "Link Telecom" complained on the North American Network Operators’ Group (NANOG) mailing list that his network had been hijacked by a spammer. The victim AS 31733 had five hijacked prefixes. On both August 25th and August 29th, changes were observed in the routes towards AS 31733 advertised in BGP. These changes were the result of the owner regaining control over his network.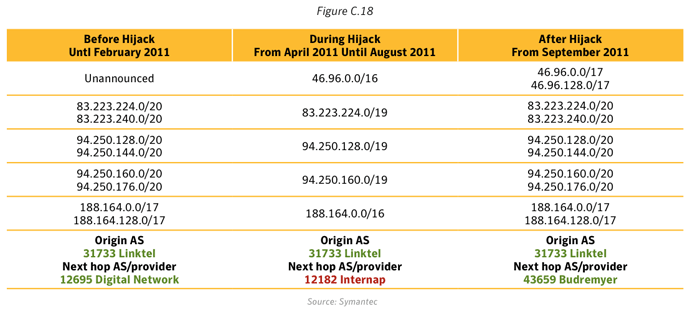
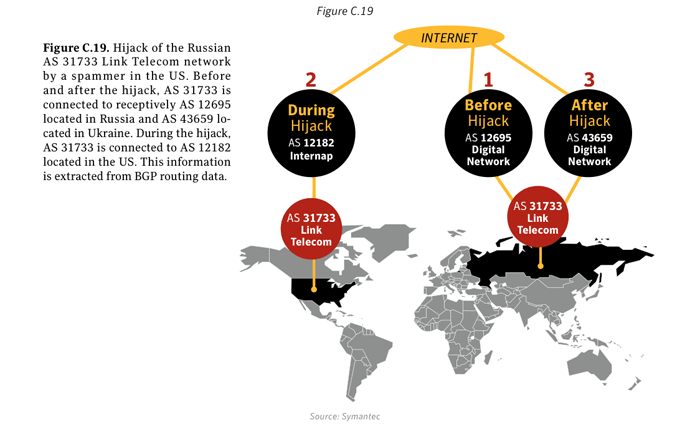
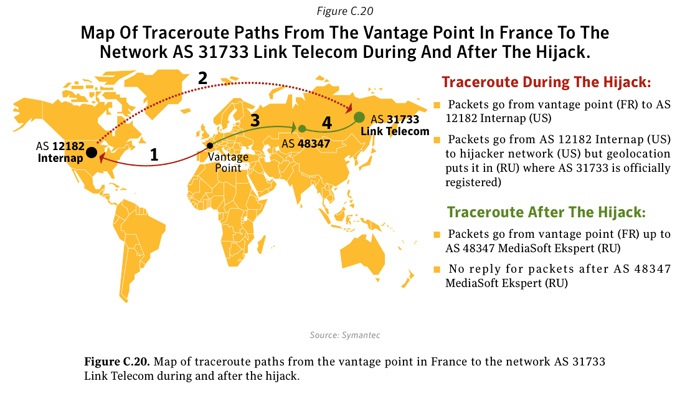
Phishing Activity Trends
Background
This section discusses the proportion of malicious email activity that is categorized as phishing attacks and looks more closely at the emerging trends, particularly social engineering techniques and how attackers can automate the use of RSS news feeds to incorporate news and current affairs stories into their scams.Methodology
The data for this section is based on the analysis of email traffic collected from Symantec.cloud global honeypots and from the analysis of malicious and unwanted email traffic data collected from customers worldwide. The analysis of phishing trends is based on emails processed by Symantec.cloud Skeptic technology, and analysis of phishing emails collected in spam honeypots. Symantec.cloud spam honeypots collected between 5–10 million spam emails each day during 2011.Data and Commentary
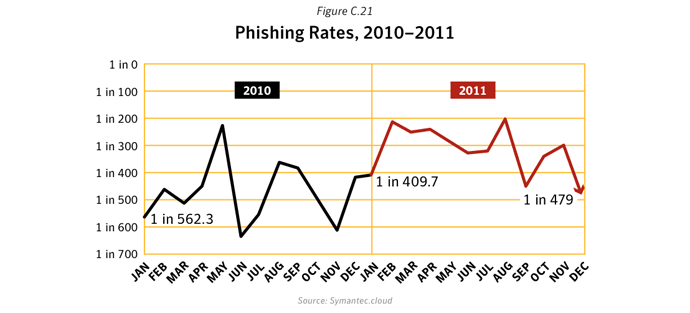
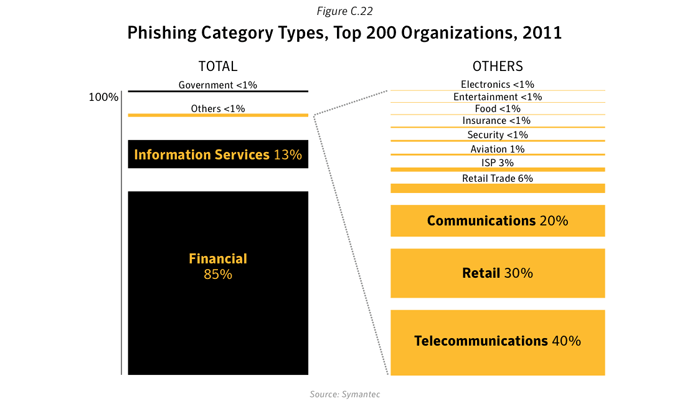
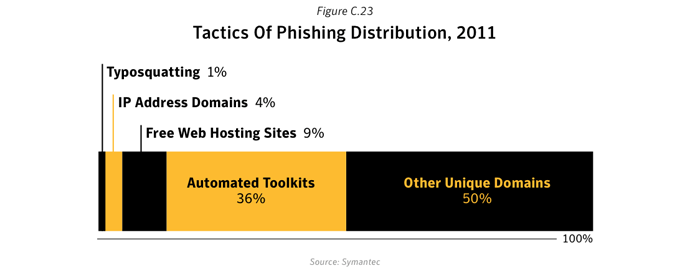
Commentary
- Overall for 2011, 1 in 298.9 emails was identified and blocked as a phishing attack, compared with 1 in 442.1 in 2010; an increase of 0.11 percentage points.
- 85.2% of phishing attacks in 2011 related to spoofed financial organizations, compared with 56% in 2010.
- Phishing URLs spoofing banks attempt to steal a wide variety of information that can be used for identity theft and fraud. Attackers seek information such as names, government-issued identification numbers, bank account information, and credit card numbers. Cybercriminals are more focused on stealing financial information that can make them large amounts of money quickly versus goods that require a larger time investment, such as scams.
- Phishing schemes continued to use major events to entice recipients: Many email-based fraud attempts referred to major events in 2011. Examples included the Japanese earthquake, where the criminals would attempt to exploit people’s sympathies for the victims of the disaster. Many charities sought donations to provide support and cyber criminals exploited this by sending 419-scam emails in which they spoofed legitimate charities with fraudulent websites.
- 36.2% of phishing attacks were conducted through the use of phishing toolkits.
Analysis of Phishing Activity by Geography, Industry Sector and Company Size
Background
Phishing activity trends can also reveal patterns that may be associated with particular geographical locations, or hotspots, for example, the industry sector may also have an influence on an organization’s risk factor, where certain industries may be exposed to different levels of threat, by the nature of their business.Methodology
Analysis of phishing activity based on geography, industry and size is determined from the patterns of spam activity for Symantec.cloud clients for threats during 2011.Data
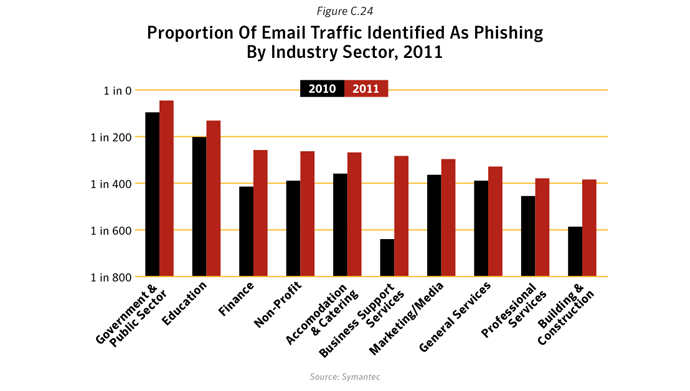
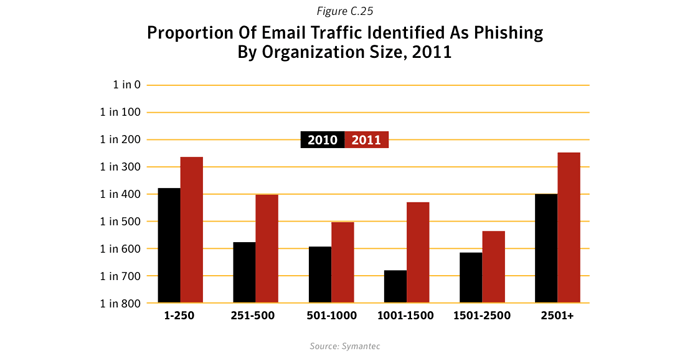
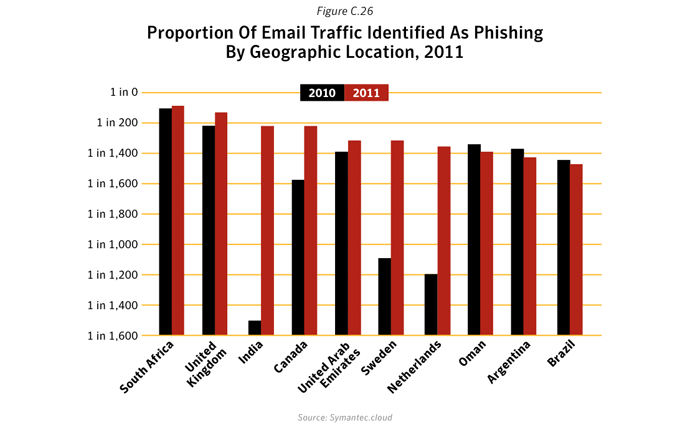
Commentary
- The phishing rate has decreased for seven of the top-10 geographies in 2011. The highest average rate for phishing activity in 2011 was for organizations in South Africa, with an overall average phishing rate of 1 in 96.3. In 2010, the highest rate was also for South Africa, with an overall average phishing rate of 1 in 99.0.
- The phishing rate has increased across all top-ten industry sectors in 2011. Organizations in the Government and Public Sector were subjected to the highest level of phishing activity in 2011, with 1 in 49.4 emails identified and blocked as phishing attacks. In 2010 the sector with the highest average phishing rate was also the Government and Public Sector, with a phishing rate of 1 in 104.3.
- The spam rate has increased for all sizes of organization in 2011. 1 in 250.5 emails sent to large enterprises with more than 2,500 employees in 2011 were identified and blocked as phishing attacks, compared with 1 in 400.0 in 2010.
- 1 in 266.1 emails sent to small to medium-sized businesses with up to 250 employees in 2011 were identified and blocked as phishing attacks, compared with 1 in 379.7 in 2010.
The Americas Region - Introduction
The Americas Region - Threat Activity Trends
The following section of the Symantec Americas Region (including North America and Latin America) Internet Security Threat Report provides an analysis of threat activity, malicious activity, and data breaches that Symantec observed in the Americas region in 2011. The malicious activity discussed in this section not only includes threat activity, but also phishing, malicious code, spam zombies, bot-infected computers, and network attack origins. Attacks are defined as any malicious activity carried out over a network that has been detected by an intrusion detection system (IDS) or firewall. Definitions for the other types of malicious activities can be found in their respective sections within this report.Threat Activity Trends Metrics for the Americas
AMS Malicious Code Activity Trends
Symantec collects malicious code information from its large global customer base through a series of opt in anonymous telemetry programs, including Norton Community Watch, Symantec Digital Immune System, and Symantec Scan and Deliver technologies. Well over 133 million clients, servers, and gateway systems actively contribute to these programs. New malicious code samples, as well as detection incidents from known malicious code types, are reported back to Symantec. Reported incidents are considered potential infections if an infection could have occurred in the absence of security software to detect and eliminate the threat.- Backdoors allow an attacker to remotely access compromised computers.
- Trojans are malicious code that users unwittingly install onto their computers, most commonly through either opening email attachments or downloading from the Internet. Trojans are often downloaded and installed by other malicious code as well. Trojan horse programs differ from worms and viruses in that they do not propagate themselves.
- Viruses propagate by infecting existing files on affected computers with malicious code.
- Worms are malicious code threats that can replicate on infected computers or in a manner that facilitates them being copied to another computer (such as via USB storage devices).
Malicious Code Activity Trends Metrics for the America
AMS Malicious Activity by Geography
Background
This metric assesses the countries in the Americas (including North America and Latin America) region in which the largest amount of malicious activity takes place or originates. Malicious activity usually affects computers that are connected to high-speed broadband Internet because these connections are attractive targets for attackers. Broadband connections provide larger bandwidth capacities than other connection types, faster speeds, the potential of constantly connected systems, and typically a more stable connection. Symantec categorizes malicious activities as follows:- Malicious code: This includes viruses, worms, and Trojans that are covertly inserted into programs. The purposes of malicious code include destroying data, running destructive or intrusive programs, stealing sensitive information, or compromising the security or integrity of a victim’s computer data.
- Spam zombies: These are compromised systems that are remotely controlled and used to send large volumes of junk or unsolicited emails. These emails can be used to deliver malicious code and phishing attempts.
- Phishing hosts: A phishing host is a computer that provides website services for the purpose of attempting to illegally gather sensitive, personal and financial information while pretending that the request is from a trusted, well-known organization. These websites are designed to mimic the sites of legitimate businesses.
- Bot-infected computers: These are compromised computers that are being controlled remotely by attackers. Typically, the remote attacker controls a large number of compromised computers over a single, reliable channel in a bot network (botnet), which then is used to launch coordinated attacks.
- Network attack origins: These are originating sources of attacks from the Internet. For example, attacks can target SQL protocols or buffer overflow vulnerabilities.
- Web-based attack origins: This measures attack sources that are delivered via the Web or through HTTP. Typically, legitimate websites are compromised and used to attack unsuspecting visitors.
Methodology
To determine malicious activity by source geography, Symantec has compiled geographical data on numerous malicious activities, including malicious code reports, spam zombies, phishing hosts, bot-infected computers, and network attack origins. The proportion of each activity originating in each geography is then determined within the region. The mean of the percentages of each malicious activity that originates in each geography is calculated. This average determines the proportion of overall malicious activity that originates from the geography in question. The rankings are then determined by calculating the mean average of the proportion of these malicious activities that originated in each geography.Data
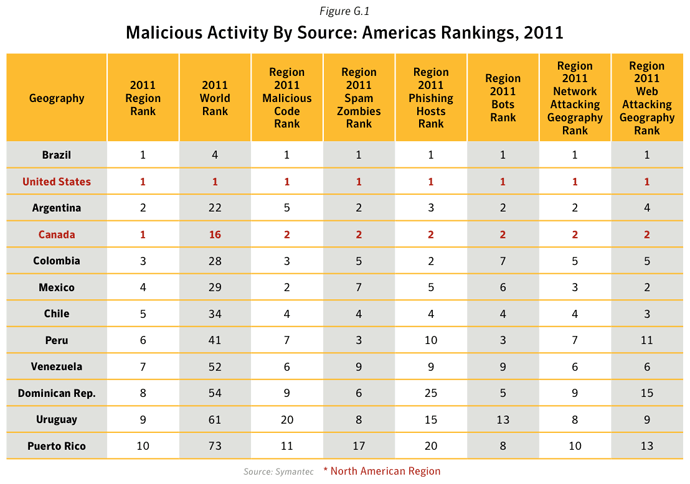
Source: Symantec
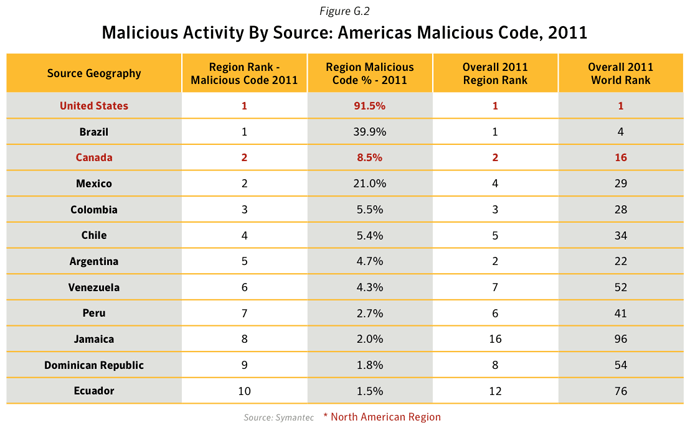
Source: Symantec
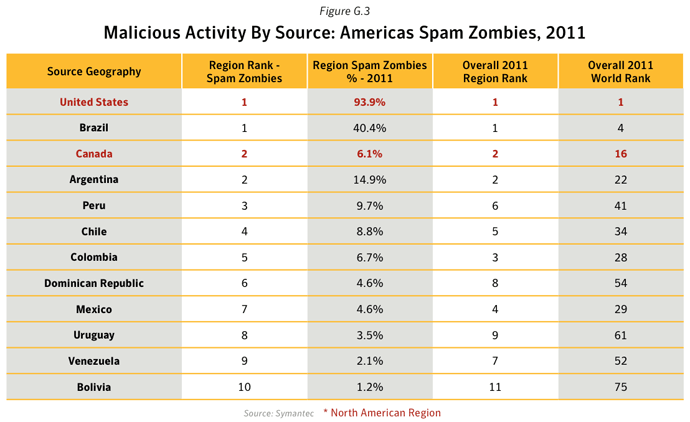
Source: Symantec
Source: Symantec
Source: Symantec

Source: Symantec
Source: Symantec
Commentary
- Malicious activity originating from infected computers in the Brazil has pushed the country to the top of the table as a source of malicious activity in LAM for 2011, and ranked fourth globally.
- The United States was number one for NAM and number one globally. Brazil and the United States were the top source of malicious activity across all categories for each of their respective regions.
- Argentina was ranked in second position overall in LAM, and was ranked second for spam zombies, bots and as a source of network attacks in LAM.
AMS Attack Origin by Country
AMS Attack Origin by Country
This metric assesses the top global countries from which attacks originated that targeted the Americas region in 2011. Note that, because the attacking computer could be controlled remotely, the attacker may be in a different location than the computer being used to mount the attack. For example, an attacker physically located in the Brazil could launch an attack from a compromised system in Australia against a network in Japan.Methodology
This section measures the top originating countries of attacks that targeted computers in the Americas region in 2011. A network attack is generally considered any malicious activity carried out over a network that has been detected by an intrusion detection system (IDS), intrusion prevention system (IPS), or firewall.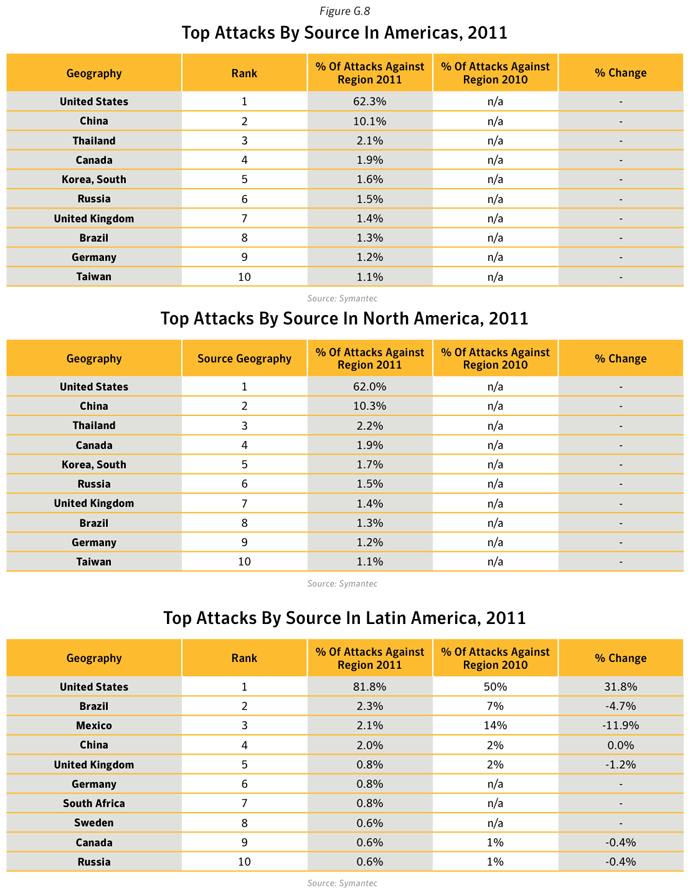
Figure G.8 Top attacks by country in Americas, 2011
Source: Symantec
Commentary
- The United States continues to dominate attacks on the Americas region: In 2011, the United States was the top country of origin for attacks against targets in the Americas region, accounting for half of all attacks detected by Symantec sensors in the region.
- This result is likely due to the high level of attack activity originating in the United States generally, as it was also the top country for originating Web-attacks globally, with 16.9% of the total. It also ranked second position globally as a source for network attacks, with 33.5% of network attacks originating in the United States.
- Moreover, the United States ranked first for overall global malicious activity, with 21.1% of the overall total. The United States also ranked first globally for bot-infected computers (12.6%) and in second position for malicious code (13.3%); much of the attack activity targeting countries in the Americas region would have been conducted through these malicious bot networks.
AMS Top Malicious Code Samples
Background
This metric assesses the top malicious code samples in the Americas region in 2011. Symantec analyses new and existing malicious code samples to determine which threats types and attack vectors are being employed in the most prevalent threats. This information also allows administrators and users to gain familiarity with threats that attackers may favor in their exploits. Insight into emerging threat development trends can help bolster security measures and mitigate future attacks.Methodology
To determine top malicious code samples, Symantec ranks each malicious code sample based on the volume of unique sources of potential infections observed during the reporting period.Data
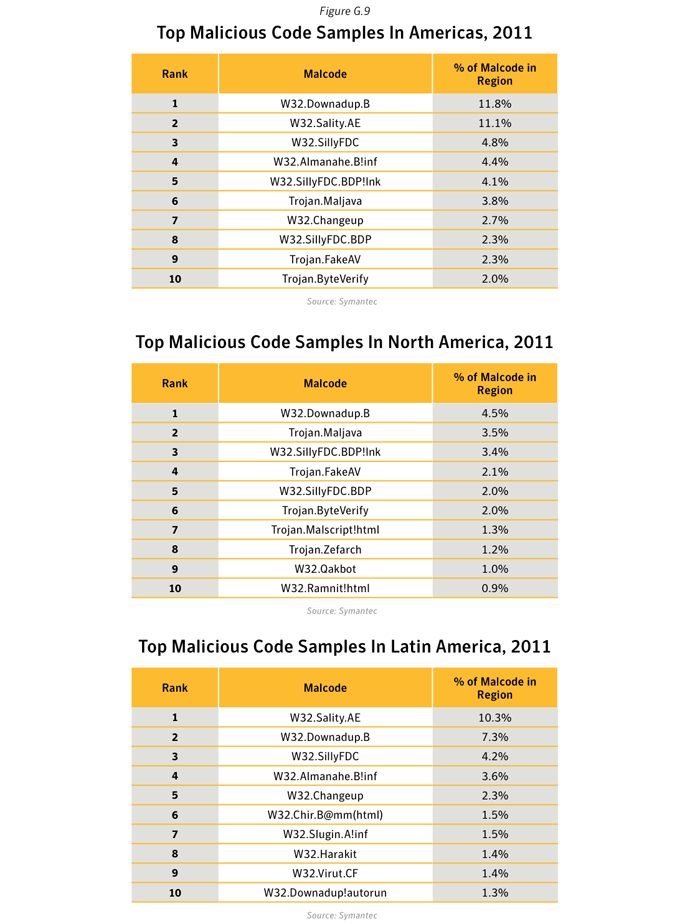
Source: Symantec
Commentary
- The W32.Downadup (aka Conficker) dominates in the Americas region: W32.Downadup.B was ranked in first position in the Americas region in 2011, accounting for 7.3% of potential infections in LAM and 4.5% in NAM.
- The Downadup family of malware was ranked in fourth position globally in 2011, despite losing momentum, when in 2010 it was ranked second-most malicious code family by volume of potential infections globally.
- Downadup propagates by exploiting vulnerabilities in order to copy itself to network shares. Downadup was estimated still to be on more than 3 million PCs worldwide at the end of 2011 , compared with approximately 5 million at the end of 2010.
- Interestingly, variants of Ramnit, which was the number one family of malware globally in 2011, did not feature strongly in the top-10 malware identified in the Americas region, and accounted for less than 1% of potential infections in NAM.
- W32.Sality.AE was ranked number one in LAM, but did not feature in the top-ten for NAM. Reported activity by this virus was the primary contributor to the Sality family being the second highest ranked malicious code family globally in 2011.
- Discovered in 2008, Sality.AE has been a prominent part of the threat landscape since then, including being the global top malicious code family identified by Symantec in 2010 and 2009.
- Sality may be particularly attractive to attackers because it uses polymorphic code that can hamper detection. Sality is also capable of disabling security services on affected computers. These two factors may lead to a higher rate of successful installations for attackers.
Introduction
EMEA Threat Activity Trends
The following section of the Symantec Europe, the Middle East and Africa (EMEA) Internet Security Threat Report provides an analysis of threat activity, malicious activity, and data breaches that Symantec observed in EMEA in 2011. The malicious activity discussed in this section not only includes threat activity, but also phishing, malicious code, spam zombies, bot-infected computers, and network attack origins. Attacks are defined as any malicious activity carried out over a network that has been detected by an intrusion detection system (IDS) or firewall. Definitions for the other types of malicious activities can be found in their respective sections within this report.Threat Activity Trends Metrics for Europe, the Middle East, and Africa
EMEA Malicious Code Activity Trends
Symantec collects malicious code information from its large global customer base through a series of opt in anonymous telemetry programs, including Norton Community Watch, Symantec Digital Immune System, and Symantec Scan and Deliver technologies. Well over 133 million clients, servers, and gateway systems actively contribute to these programs. New malicious code samples, as well as detection incidents from known malicious code types, are reported back to Symantec. Reported incidents are considered potential infections if an infection could have occurred in the absence of security software to detect and eliminate the threat.- Backdoors allow an attacker to remotely access compromised computers.
- Trojans are malicious code that users unwittingly install onto their computers, most commonly through either opening email attachments or downloading from the Internet. Trojans are often downloaded and installed by other malicious code as well. Trojan horse programs differ from worms and viruses in that they do not propagate themselves.
- Viruses propagate by infecting existing files on affected computers with malicious code.
- Worms are malicious code threats that can replicate on infected computers or in a manner that facilitates them being copied to another computer (such as via USB storage devices).
Malicious Code Activity Trends Metrics for Europe, the Middle East, and Africa
EMEA Malicious Activity by Geography
Background
This metric assesses the countries in the Europe, the Middle East, and Africa (EMEA) region in which the largest amount of malicious activity takes place or originates. Malicious activity usually affects computers that are connected to high-speed broadband Internet because these connections are attractive targets for attackers. Broadband connections provide larger bandwidth capacities than other connection types, faster speeds, the potential of constantly connected systems, and typically a more stable connection. Symantec categorizes malicious activities as follows:- Malicious code: This includes viruses, worms, and Trojans that are covertly inserted into programs. The purposes of malicious code include destroying data, running destructive or intrusive programs, stealing sensitive information, or compromising the security or integrity of a victim’s computer data
- Spam zombies: These are compromised systems that are remotely controlled and used to send large volumes of junk or unsolicited emails. These emails can be used to deliver malicious code and phishing attempts.
- Phishing hosts: A phishing host is a computer that provides website services for the purpose of attempting to illegally gather sensitive, personal and financial information while pretending that the request is from a trusted, well-known organization. These websites are designed to mimic the sites of legitimate businesses.
- Bot-infected computers: These are compromised computers that are being controlled remotely by attackers. Typically, the remote attacker controls a large number of compromised computers over a single, reliable channel in a bot network (botnet), which then is used to launch coordinated attacks.
- Network attack origins: These are originating sources of attacks from the Internet. For example, attacks can target SQL protocols or buffer overflow vulnerabilities.
- Web-based attack origins: This measures attack sources that are delivered via the Web or through HTTP. Typically, legitimate websites are compromised and used to attack unsuspecting visitors.
Methodology
To determine malicious activity by source geography, Symantec has compiled geographical data on numerous malicious activities, including malicious code reports, spam zombies, phishing hosts, bot-infected computers, and network attack origins. The proportion of each activity originating in each geography is then determined within the region. The mean of the percentages of each malicious activity that originates in each geography is calculated. This average determines the proportion of overall malicious activity that originates from the geography in question. The rankings are then determined by calculating the mean average of the proportion of these malicious activities that originated in each geography.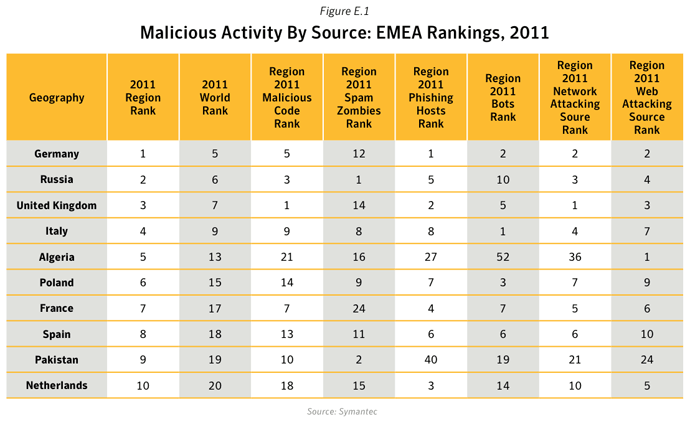
Source: Symantec
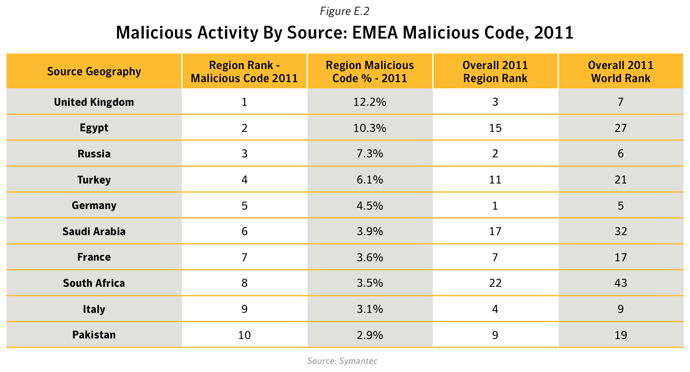
Malicious code, 2011
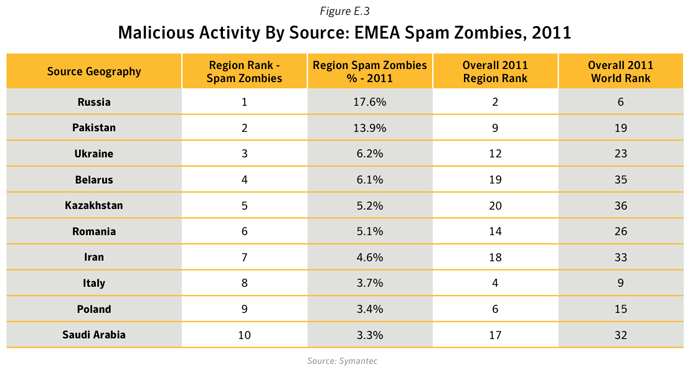
Source: Symantec
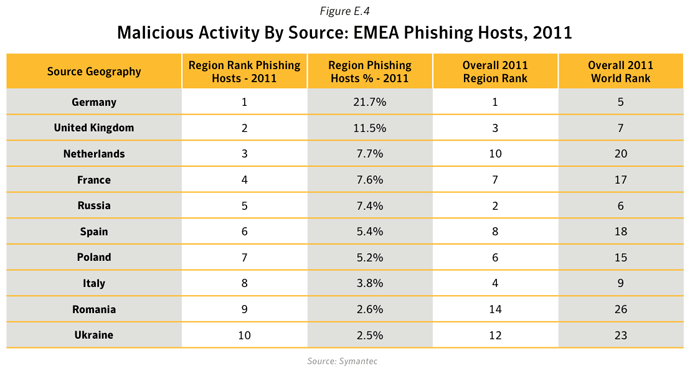
Source: Symantec
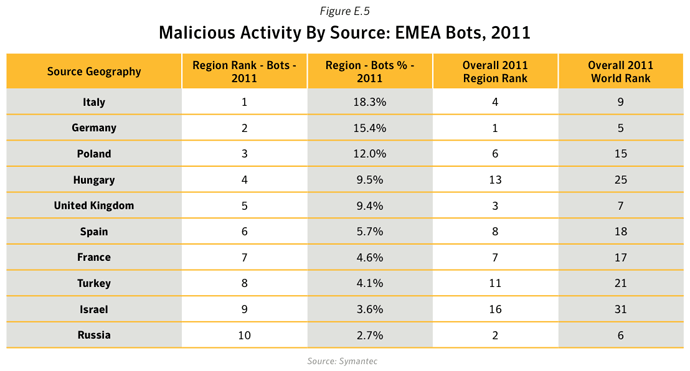
Bots, 2011 Source: Symantec
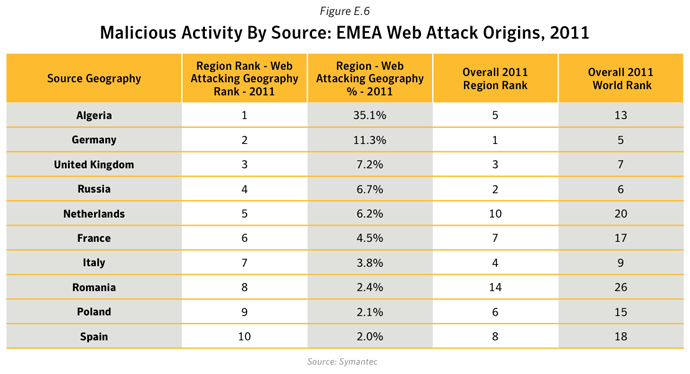
Source: Symantec
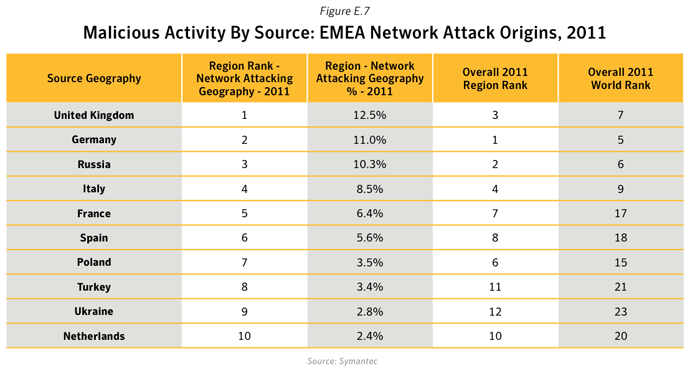
Source: Symantec
Commentary
- Malicious activity originating from computers in Germany has pushed the geography to the top of the table of overall malicious activity in 2011, with Germany being the number one host for phishing Web sites in the region. Germany was also ranked in second position for bot activity, network attacks and Web-based attacks. Germany was ranked in fifth position worldwide as a source for worldwide malicious activity.
- Russia was ranked in second position overall in EMEA and was the top source of spam zombies in the region.
- The United Kingdom was ranked third overall in the region and was in first position for malicious code activity in EMEA and the top source of network attacks in the region.
Attack Origin by Country
Background
This metric assesses the top global countries from which attacks originated that targeted the EMEA region in 2011. Note that, because the attacking computer could be controlled remotely, the attacker may be in a different location than the computer being used to mount the attack. For example, an attacker physically located in the United States could launch an attack from a compromised system in Germany against a network in the United Kingdom.Methodology
This section measures the top originating countries of attacks that targeted computers in EMEA in 2011. A network attack is generally considered any malicious activity carried out over a network that has been detected by an intrusion detection system (IDS), intrusion prevention system (IPS), or firewall.Data
Source: Symantec
Commentary
- The United States continues to dominate attacks on EMEA: In 2011, the United States was the top country of origin for attacks against EMEA targets, accounting for 35.6% of all attacks detected by Symantec sensors in the region. This is the approximately the same percentage as in 2010 and 2009, when the United States also ranked in first position.
- This result is likely due to the high level of attack activity originating in the United States generally, as it was also the top country for originating Web-attacks globally, with 16.9% of the total. It also ranked second position globally as a source for network attacks, with 33.5% of network attacks originating in the United States.
- Moreover, the United States ranked first for overall global malicious activity, with 21.1% of the overall total. The United States also ranked first globally for bot-infected computers (12.6%) and in second position for malicious code (13.3%); much of the attack activity targeting EMEA countries would have been conducted through these malicious bot networks.
- Attacks from China also increased by 7.1 percentage points in 2011,this is owing to a general increase in the number of network attacks originating from China.
- Attacks from Japan, Switzerland, Italy and Spain increased against targets in the EMEA region. These countries did not feature in the top-ten source of attacks in the previous year.
Top Malicious Code Samples
Background
This metric assesses the top malicious code samples in EMEA in 2011. Symantec analyses new and existing malicious code samples to determine which threats types and attack vectors are being employed in the most prevalent threats. This information also allows administrators and users to gain familiarity with threats that attackers may favor in their exploits. Insight into emerging threat development trends can help bolster security measures and mitigate future attacks.Methodology
To determine top malicious code samples, Symantec ranks each malicious code sample based on the volume of unique sources of potential infections observed during the reporting period.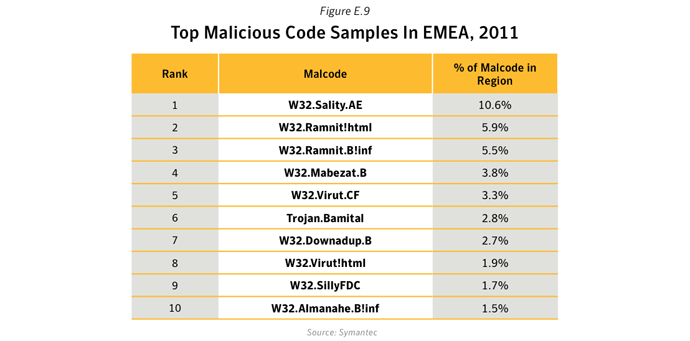
SourceSymantec
Commentary
- The Sality.AE virus continues to dominate in EMEA: The top malicious code sample by volume of potential infections in EMEA for 2011 was Sality.AE. Reported activity by this virus was the primary contributor to the Sality family being the second highest ranked malicious code family globally, by prevalence in 2011.
- Discovered in 2008, Sality.AE has been a prominent part of the threat landscape since then, including being the global top malicious code family identified by Symantec in 2010 and 2009.
- Sality may be particularly attractive to attackers because it uses polymorphic code that can hamper detection. Sality is also capable of disabling security services on affected computers. These two factors may lead to a higher rate of successful installations for attackers.
- Sality propagates by infecting executable files and copying itself to removable drives such as USB devices. The virus then relies on Microsoft Windows AutoRun functionality to execute when those drives are accessed. This can occur when an infected USB device is attached to a computer.
- The reliable simplicity of spreading via USB devices and other media makes malicious code families such as Sality.AE (as well as SillyFDC and others) effective vehicles for installing additional malicious code on computers.
- Ramnit becomes the second most prevalent malicious code family in 2011. Ramnit was ranked in third position in EMEA in 2010. In 2011, Ramnit is ranked in first position globally as the most prevalent malicious code family.
- This is primarily the result of activity by W32.Ramnit!html, which accounts for 51% of all Ramnit malware identified globally in 2011. W32.Ramnit!html is a generic detection for .html files infected by W32.Ramnit.
- First discovered in 2010, W32.Ramnit has been a prominent feature of the threat landscape since then, often switching places with Sality throughout the year as the two families jockey for first position.
- Ramnit spreads by encrypting and then appending itself to DLL, EXE and HTML files. It can also spread by copying itself to the recycle bin on removable drives and creating an AUTORUN.INF file so that the malware is potentially automatically executed on other computers. This can occur when an infected USB device is attached to a computer. The reliable simplicity of spreading via USB devices and other media makes malicious code families such as Ramnit, Sality (as well as SillyFDC and others) effective vehicles for installing additional malicious code on computers.
Best Practice Guidelines for Businesses
- Endpoint intrusion prevention that protects against un-patched vulnerabilities from being exploited, protects against social engineering attacks and stops malware from reaching endpoints;
- Browser protection for protection against obfuscated Web-based attacks;
- Consider cloud-based malware prevention to provide proactive protection against unknown threats;
- File and Web-based reputation solutions that provide a risk-and-reputation rating of any application and Web site to prevent rapidly mutating and polymorphic malware;
- Behavioral prevention capabilities that look at the behavior of applications and malware and prevent malware;
- Application control settings that can prevent applications and browser plug-ins from downloading unauthorized malicious content;
- Device control settings that prevent and limit the types of USB devices to be used.
- Implementing Always On SSL;
- Scanning your website daily for malware;
- Setting the secure flag for all session cookies;
- Regularly assessing your website for vulnerabilities;
- Choosing SSL Certificates with Extended Validation to display the green browser address bar to website users;
- Displaying recognized trust marks in highly visible locations on your website to inspire trust and show customers your commitment to their security.
- Use separate Test Signing and Release Signing infrastructures,
- Store keys in secure, tamper-proof, cryptographic hardware devices, and
- Implement physical security to protect your assets from theft.
- Ensure that you have your security vendors contact information, know who you will call, and what steps you will take if you have one or more infected systems;
- Ensure that a backup-and-restore solution is in place in order to restore lost or compromised data in the event of successful attack or catastrophic data loss;
- Make use of post-infection detection capabilities from Web gateway, endpoint security solutions and firewalls to identify infected systems;
- Isolate infected computers to prevent the risk of further infection within the organization;
- If network services are exploited by malicious code or some other threat, disable or block access to those services until a patch is applied;
- Perform a forensic analysis on any infected computers and restore those using trusted media.
- Do not open attachments unless they are expected and come from a known and trusted source, and do not execute software that is downloaded from the Internet (if such actions are permitted) unless the download has been scanned for viruses;
- Be cautious when clicking on URLs in emails or social media programs, even when coming from trusted sources and friends;
- Do not click on shortened URLs without previewing or expanding them first using available tools and plug-ins;
- Recommend that users be cautious of information they provide on social networking solutions that could be used to target them in an attack or trick them to open malicious URLs or attachments;
- Be suspicious of search engine results and only click through to trusted sources when conducting searches—especially on topics that are hot in the media;
- Deploy Web browser URL reputation plug-in solutions that display the reputation of Web sites from searches;
- Only download software (if allowed) from corporate shares or directly from the vendors Web site;
- If users see a warning indicating that they are “infected” after clicking on a URL or using a search engine (fake antivirus infections), have users close or quit the browser using Alt-F4, CTRL+W or the task manager.
- Advise users to make sure they are using a modern browser and operating system and to keep their systems current with security updates.
- Instruct users to look for a green browser address bar, HTTPS, and trust marks on any websites where they login or share any personal information.
Best Practice Guidelines for Consumers
- Antivirus (file and heuristic based) and malware behavioral prevention can prevents unknown malicious threats from executing;
- Bidirectional firewalls will block malware from exploiting potentially vulnerable applications and services running on your computer;
- Intrusion prevention to protection against Web-attack toolkits, unpatched vulnerabilities, and social engineering attacks;
- Browser protection to protect against obfuscated Web-based attacks;
- Reputation-based tools that check the reputation and trust of a file and Web site before downloading; URL reputation and safety ratings for Web sites found through search engines.
- Consider options for implementing cross-platform parental controls, such as Norton Online Familyxlii.
- Downloading “free,” “cracked” or “pirated” versions of software can also contain malware or include social engineering attacks that include programs that try to trick you into thinking your computer is infected and getting you to pay money to have it removed.
- Be careful which Web sites you visit on the Web. While malware can still come from mainstream Web sites, it can easily come from less reputable Web sites sharing pornography, gambling and stolen software.
- Read end-user license agreements (EULAs) carefully and understand all terms before agreeing to them as some security risks can be installed after an end user has accepted the EULA or because of that acceptance.
- Be cautious when clicking on URLs in emails, social media programs even when coming from trusted sources and friends. Do not blindly click on shortened URLs without expanding them first using previews or plug-ins.
- Do not click on links in social media applications with catchy titles or phrases even from friends. If you do click on the URL, you may end up “liking it” and sending it to all of your friends even by clicking anywhere on the page. Close or quit your browser instead.
- Use a Web browser URL reputation solution that shows the reputation and safety rating of Web sites from searches. Be suspicious of search engine results; only click through to trusted sources when conducting searches, especially on topics that are hot in the media.
- Be suspicious of warnings that pop-up asking you to install media players, document viewers and security updates; only download software directly from the vendor’s Web site
- Never disclose any confidential personal or financial information unless and until you can confirm that any request for such information is legitimate.
- Review your bank, credit card, and credit information frequently for irregular activity. Avoid banking or shopping online from public computers (such as libraries, Internet cafes, etc.) or from unencrypted Wi-Fi connections.
- Use HTTPS when connecting via Wi-Fi networks to your email, social media and sharing Web sites. Check the settings and preferences of the applications and Web sites you are using.
- Look for the green browser address bar, HTTPS, and recognizable trust marks when you visit websites where you login or share any personal information.
- Configure your home Wi-Fi network for strong authentication and always require a unique password for access to it.